Mandiant’s Release of Rainbow Tables Exposes Critical NTLMv1 Vulnerabilities
In a significant move to highlight the vulnerabilities of outdated authentication protocols, Mandiant, a subsidiary of Google, has publicly released an extensive set of Net-NTLMv1 rainbow tables. This release serves as a stark reminder of the pressing need for organizations to transition away from Net-NTLMv1, a protocol that has been considered cryptographically compromised since 1999 and widely recognized as insecure since at least 2012.
Despite numerous security advisories over the past two decades, Mandiant’s consultants continue to encounter active deployments of Net-NTLMv1 in enterprise environments. This persistent usage underscores a concerning level of organizational inertia in addressing known security flaws.
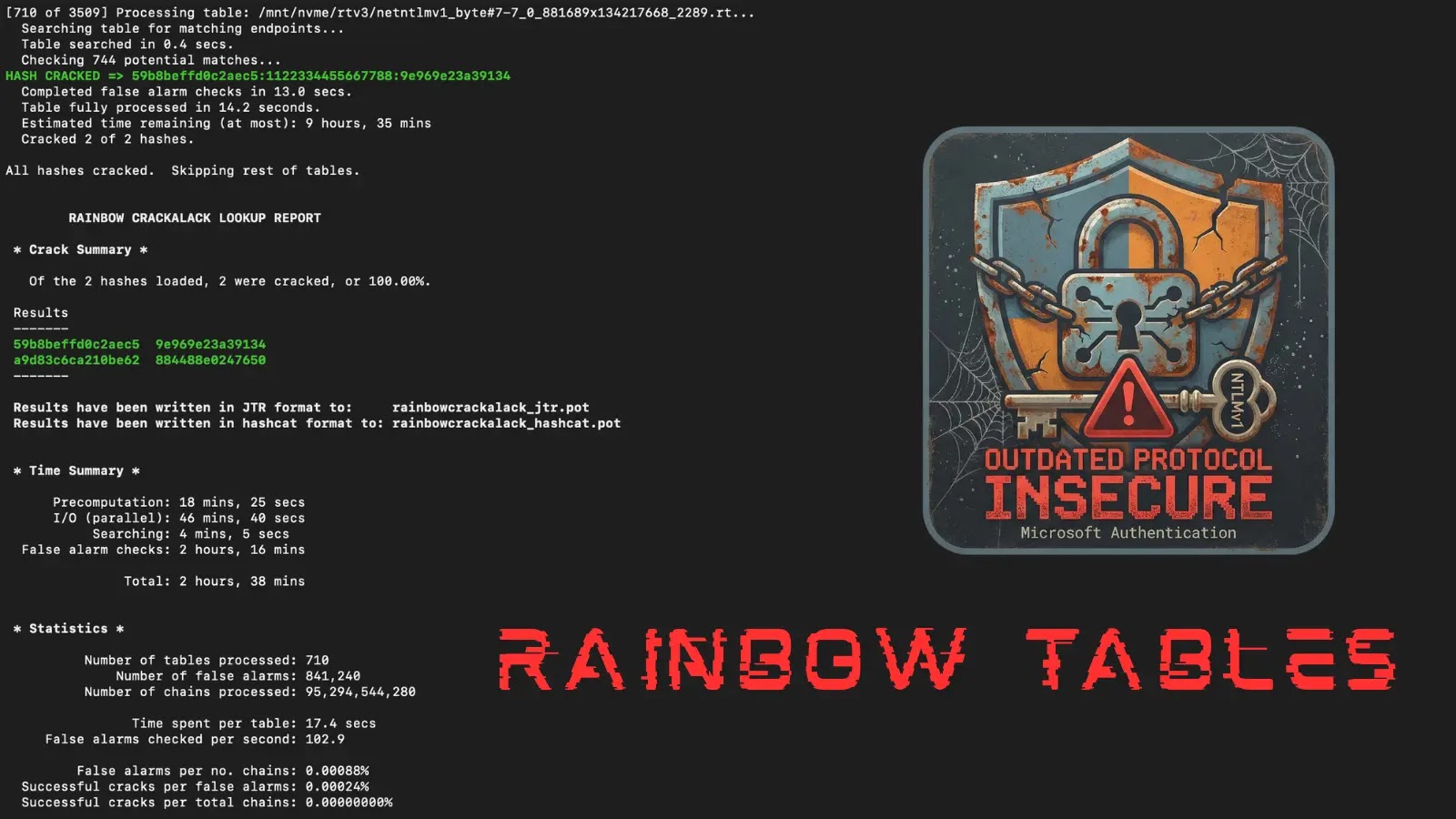
The release of these rainbow tables significantly lowers the barrier for credential recovery. Previously, exploiting Net-NTLMv1 required either uploading sensitive authentication data to third-party services or investing in expensive, dedicated hardware for brute-force attacks. Now, with Mandiant’s dataset, security professionals can recover authentication keys in under 12 hours using consumer-grade hardware costing less than $600. This development transforms Net-NTLMv1 from a theoretical vulnerability into a practical attack vector accessible to a broader range of threat actors.
Understanding the NTLMv1 Vulnerability
The core issue with Net-NTLMv1 lies in its susceptibility to known plaintext attacks (KPA). When an attacker captures a Net-NTLMv1 hash without Extended Session Security (ESS) for the known plaintext value of 1122334455667788, they can employ cryptographic techniques to recover the key material. This key material corresponds to the password hash of the authenticating Active Directory object.
The typical attack sequence begins with coercing authentication from highly privileged targets, such as domain controllers. Tools like PetitPotam or DFSCoerce are used to force these targets to initiate connections. Once the Net-NTLMv1 hashes are captured, attackers preprocess them into DES components using utilities like ntlmv1-multi. Mandiant’s rainbow tables are then applied using tools such as RainbowCrack or RainbowCrack-NG to recover the DES keys. The final key component can be calculated or retrieved using specialized tools, allowing the reconstruction of the full NT hash and leading to credential compromise.
A common escalation path involves obtaining a domain controller machine account hash, which can then facilitate DCSync attacks to compromise any account within Active Directory.
The Role of Rainbow Tables
Rainbow tables are a time-memory trade-off technique first proposed by Martin Hellman in 1980 and formally developed by Philippe Oechslin in 2003. They allow for the rapid reversal of cryptographic hash functions, making them particularly effective in cracking password hashes.
In August 2016, Hashcat added support for cracking DES keys using known plaintext, further democratizing the exploitation of Net-NTLMv1. Mandiant’s release leverages Google Cloud’s computational resources and frontline security expertise to address an entire class of authentication attacks at scale.
The dataset is accessible through the Google Cloud Research Dataset portal or via gsutil commands. SHA512 checksums are provided to verify the integrity of the dataset. The security community has already developed derivative implementations optimized for both CPU and GPU processing.
Detection and Mitigation Strategies
Attackers often use tools like Responder with the –lm and –disable-ess flags, setting authentication to the static value 1122334455667788 to force Net-NTLMv1 negotiation.
Organizations can detect such activities by monitoring Windows Event Log Event ID 4624 (An Account was successfully logged on) and filtering for the Authentication Package field, alerting when LM or NTLMv1 values appear.
Immediate mitigation requires disabling Net-NTLMv1 across the organization. Windows systems should be configured to Send NTLMv2 response only via Local Security Settings or Group Policy, specifically through the Network Security: LAN Manager authentication level settings.
However, it’s important to note that local system configurations can be altered by attackers with administrative access post-compromise. Therefore, continuous monitoring and detection mechanisms are essential beyond policy enforcement alone.
Conclusion
Mandiant’s release of these rainbow tables marks a pivotal moment in the discourse surrounding Net-NTLMv1 security. What was once considered an academic concern has now become a practical, accessible attack vector that demands immediate organizational attention and comprehensive remediation strategies.