Mandiant’s Release of NTLMv1 Rainbow Tables Highlights Urgent Security Risks
In a significant move to underscore the vulnerabilities of outdated authentication protocols, Mandiant, a subsidiary of Google, has publicly released an extensive set of Net-NTLMv1 rainbow tables. This release serves as a stark reminder of the critical security risks associated with the continued use of the deprecated Net-NTLMv1 protocol, which has been considered cryptographically compromised since 1999 and widely recognized as insecure since at least 2012.
Persistent Use of Net-NTLMv1 Despite Known Vulnerabilities
Despite longstanding warnings from the cybersecurity community, Mandiant’s consultants frequently encounter active deployments of Net-NTLMv1 in enterprise environments. This ongoing usage suggests a concerning level of organizational inertia, where outdated systems remain operational due to compatibility concerns, lack of awareness, or resource constraints.
Lowering the Barrier to Credential Recovery
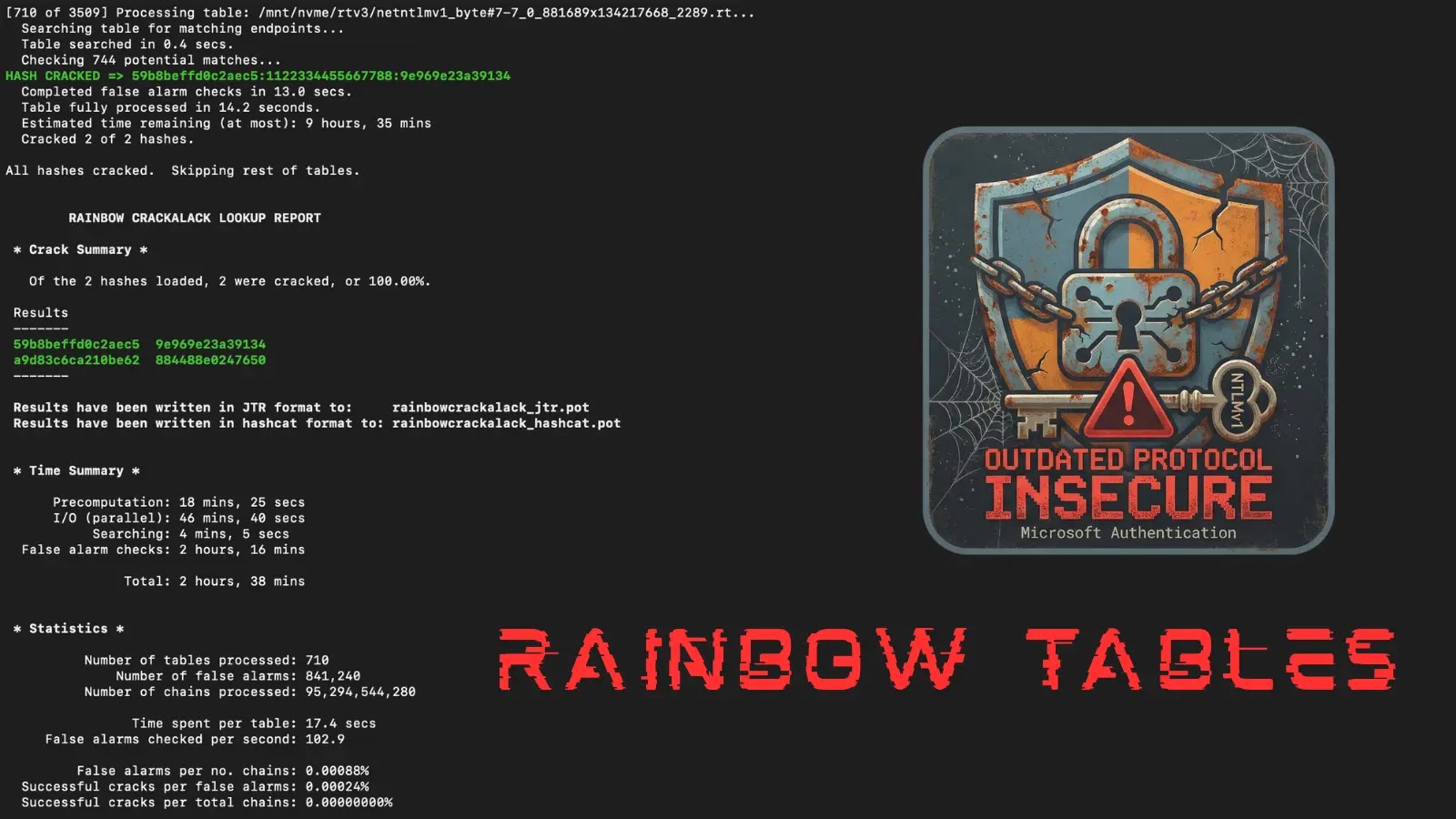
The release of these rainbow tables significantly reduces the complexity and cost associated with exploiting Net-NTLMv1 vulnerabilities. Previously, attackers needed to either upload sensitive authentication data to third-party services or invest in expensive, dedicated hardware to perform brute-force attacks. Now, with Mandiant’s dataset, security professionals and potential attackers alike can recover authentication keys in under 12 hours using consumer-grade hardware costing less than $600 USD. This development transforms Net-NTLMv1 from a theoretical risk into a practical and accessible attack vector for a broader range of threat actors.
Technical Breakdown of the Vulnerability
The core issue with Net-NTLMv1 lies in its reliance on a known plaintext attack (KPA) mechanism. When an attacker captures a Net-NTLMv1 hash without Extended Session Security (ESS) for the known plaintext value of 1122334455667788, they can exploit cryptographic weaknesses to recover the key material. This key material corresponds to the password hash of the authenticating Active Directory object, effectively granting the attacker unauthorized access.
Typical Attack Chain Involving Net-NTLMv1
A common attack sequence begins with coercing authentication from high-privilege targets, such as domain controllers. Tools like PetitPotam or DFSCoerce can force these systems to initiate connections, allowing attackers to capture Net-NTLMv1 hashes. Once obtained, these hashes are processed into DES components using utilities like ntlmv1-multi. Mandiant’s rainbow tables, in conjunction with tools such as RainbowCrack or RainbowCrack-NG, are then employed to recover the DES keys. The final key component can be calculated or retrieved using specialized tools, reconstructing the full NT hash and compromising the credentials.
Escalation to Full Domain Compromise
One particularly alarming escalation path involves recovering the machine account hash of a domain controller. With this hash, attackers can perform DCSync attacks, allowing them to replicate directory services and compromise any account within Active Directory. This level of access can lead to complete control over an organization’s network, data exfiltration, and the deployment of further malicious activities.
Historical Context and Development of Rainbow Tables
Rainbow tables, a time-memory trade-off technique, were first proposed by Martin Hellman in 1980 and formally developed by Philippe Oechslin in 2003. In August 2016, Hashcat added support for cracking DES keys using known plaintext, further democratizing the exploitation of Net-NTLMv1 vulnerabilities. Mandiant’s recent release leverages Google Cloud’s computational resources and frontline security expertise to address these authentication weaknesses at scale.
Accessing Mandiant’s Dataset
The dataset is available through the Google Cloud Research Dataset portal or via gsutil commands. SHA512 checksums are provided to verify the integrity of the dataset. The security community has already developed derivative implementations optimized for both CPU and GPU processing, enhancing the accessibility and efficiency of these tools.
Detection and Mitigation Strategies
To detect potential exploitation of Net-NTLMv1, organizations can monitor Windows Event Log Event ID 4624 (An Account was successfully logged on) and filter for the Authentication Package field, alerting when LM or NTLMv1 values appear. Immediate mitigation requires disabling Net-NTLMv1 across the organization. Windows systems must be configured to reject NTLMv1 authentication attempts, and legacy applications dependent on this protocol should be updated or replaced to support more secure authentication methods.
Conclusion
Mandiant’s release of Net-NTLMv1 rainbow tables serves as a critical wake-up call for organizations still relying on outdated authentication protocols. The ease with which these vulnerabilities can now be exploited underscores the necessity for immediate action. Organizations must prioritize the migration to secure authentication methods, such as Kerberos, to protect their systems and data from increasingly accessible and potent cyber threats.