AWS CodeBuild Misconfiguration Exposes GitHub Repositories to Potential Supply Chain Attacks
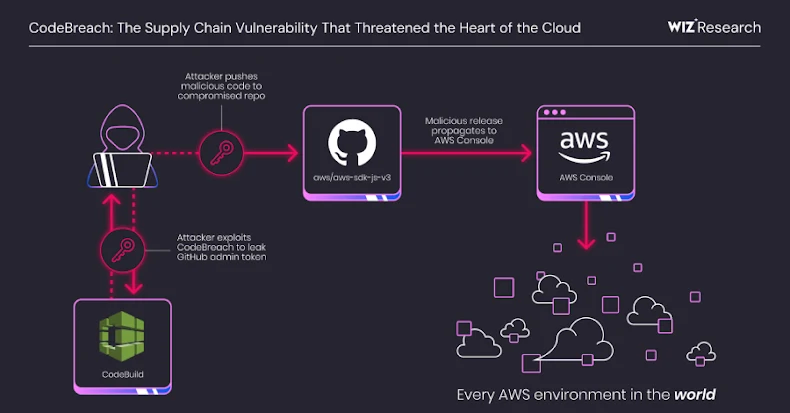
A significant misconfiguration within Amazon Web Services (AWS) CodeBuild has been identified, potentially allowing unauthorized access to AWS’s own GitHub repositories, including the AWS JavaScript SDK. This vulnerability, dubbed CodeBreach by cloud security firm Wiz, was responsibly disclosed on August 25, 2025, and subsequently patched by AWS in September 2025.
Understanding the Vulnerability
The core of the issue lies in the continuous integration (CI) pipelines of AWS CodeBuild. Specifically, a flaw in the webhook filters designed to trigger builds under certain conditions could have been exploited by unauthenticated attackers. This exploitation could lead to unauthorized access to the build environment, exposure of privileged credentials such as GitHub admin tokens, and the ability to push malicious code to compromised repositories, thereby facilitating supply chain attacks.
Technical Breakdown
AWS CodeBuild utilizes webhook filters to ensure that only specific events initiate a CI build. For instance, builds can be configured to trigger only when code changes are committed to a designated branch or when a GitHub account ID (ACTOR_ID) matches a predefined regular expression pattern. These filters are crucial for protecting against untrusted pull requests.
However, the misconfiguration affected several AWS-managed open-source GitHub repositories, including:
– aws-sdk-js-v3
– aws-lc
– amazon-corretto-crypto-provider
– awslabs/open-data-registry
These projects implemented an ACTOR_ID filter but omitted the start (^) and end ($) anchors in their regular expression patterns. This oversight allowed any GitHub user ID that contained an approved ID as a substring (e.g., 755743) to bypass the filter and trigger the build.
Given that GitHub assigns numeric user IDs sequentially, Wiz researchers predicted that new user IDs (currently nine digits long) would eclipse a trusted maintainer’s six-digit ID approximately every five days. By automating the creation of GitHub Apps, which generate corresponding bot users, attackers could produce a target ID (e.g., 226755743) by initiating numerous new bot user registrations.
With the actor ID in hand, an attacker could trigger a build and obtain the GitHub credentials of the aws-sdk-js-v3 CodeBuild project. This includes a Personal Access Token (PAT) belonging to the aws-sdk-js-automation user, which possesses full administrative privileges over the repository. Such access could be exploited to push code directly to the main branch, approve pull requests, and exfiltrate repository secrets, setting the stage for widespread supply chain attacks.
AWS’s Response and Mitigation Measures
In response to the disclosure, AWS acknowledged the misconfiguration in the webhook actor ID filters for the affected repositories, clarifying that this was a project-specific issue and not a flaw in the CodeBuild service itself. AWS has since remediated the identified issues and implemented additional safeguards, including credential rotations and enhanced security measures for build processes containing GitHub tokens or other credentials in memory. Importantly, AWS reported no evidence of the CodeBreach vulnerability being exploited in the wild.
Recommendations for Mitigating Similar Risks
To prevent similar vulnerabilities, it is essential to ensure that untrusted contributions do not trigger privileged CI/CD pipelines. This can be achieved by:
– Enabling the new Pull Request Comment Approval build gate.
– Utilizing CodeBuild-hosted runners to manage build triggers via GitHub workflows.
– Ensuring that regular expression patterns in webhook filters are properly anchored.
– Generating unique PATs for each CodeBuild project and limiting their permissions to the minimum required.
– Considering the use of dedicated, unprivileged GitHub accounts for CodeBuild integration.
Broader Implications and Industry Context
This vulnerability underscores the critical importance of securing CI/CD environments. Such environments are attractive targets for adversaries due to their complexity, the handling of untrusted data, and the presence of privileged credentials. A subtle misconfiguration can lead to significant security breaches with far-reaching consequences.
This incident is part of a broader pattern of security concerns within CI/CD pipelines. For example, in 2024, research from Sysdig highlighted how insecure GitHub Actions workflows associated with the pull_request_target trigger could be exploited to leak privileged GITHUB_TOKENs, granting unauthorized access to numerous open-source projects through a single pull request from a fork.
Similarly, analyses from Orca Security revealed insecure pull_request_target configurations in projects from major companies like Google, Microsoft, and NVIDIA. These misconfigurations could allow attackers to execute arbitrary code, exfiltrate sensitive secrets, and push malicious code or dependencies to trusted branches—a phenomenon termed pull_request_nightmare.
Conclusion
The CodeBreach vulnerability serves as a stark reminder of the potential risks associated with misconfigurations in CI/CD pipelines. Organizations must remain vigilant, regularly audit their CI/CD configurations, and implement robust security measures to protect against supply chain attacks and ensure the integrity of their software development processes.