Hackers Exploit c-ares DLL Side-Loading to Deploy Malware and Evade Security
In a recent cybersecurity development, experts have uncovered an active malware campaign that exploits a DLL side-loading vulnerability within the open-source c-ares library. This sophisticated attack method enables cybercriminals to bypass traditional security measures and deploy a variety of malicious software, including trojans and data stealers.
Understanding DLL Side-Loading
DLL side-loading is a technique where attackers place a malicious Dynamic Link Library (DLL) file in the same directory as a legitimate executable. When the executable is run, it inadvertently loads the malicious DLL instead of the intended one, granting the attacker unauthorized code execution capabilities. This method is particularly insidious because it leverages trusted applications to execute harmful code, making detection challenging.
The c-ares Library Vulnerability
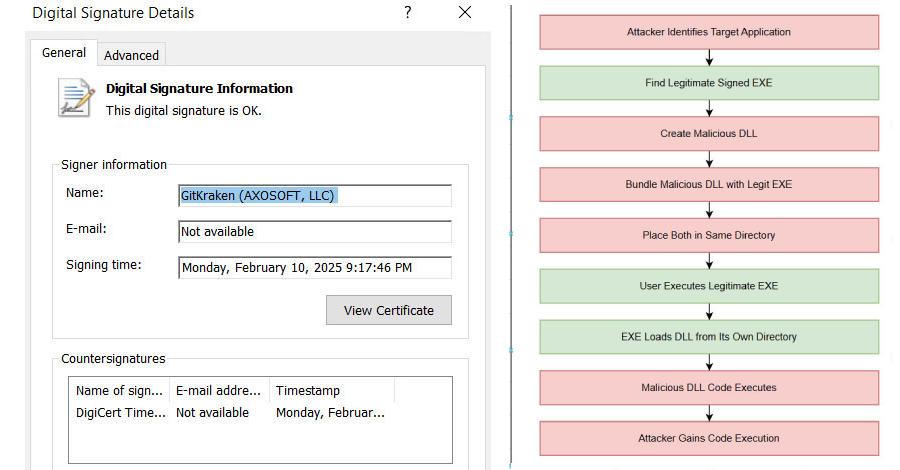
The c-ares library, widely used for asynchronous DNS requests, has become the focal point of this campaign. Attackers pair a malicious version of the `libcares-2.dll` file with a legitimate, signed executable named `ahost.exe`. This executable, often associated with GitKraken’s Desktop application, is exploited to load the malicious DLL, thereby executing the attacker’s code. By renaming `ahost.exe` and placing it alongside the rogue DLL, cybercriminals effectively bypass signature-based security defenses.
Malware Distribution and Targets
The campaign has been observed distributing a wide array of malware, including:
– Agent Tesla
– CryptBot
– FormBook
– Lumma Stealer
– Vidar Stealer
– Remcos RAT
– Quasar RAT
– DCRat
– XWorm
These malicious programs are often disguised as business-related documents, such as invoices or requests for quotes, to deceive recipients into opening them. The primary targets include employees in finance, procurement, supply chain, and administrative roles within sectors like oil and gas, as well as import and export businesses. The use of lures in multiple languages, including Arabic, Spanish, Portuguese, Farsi, and English, indicates a broad and region-specific targeting strategy.
Technical Execution of the Attack
The success of this attack hinges on the placement of the malicious DLL in the same directory as the vulnerable `ahost.exe` binary. By exploiting the search order of DLLs, the malicious file is loaded instead of its legitimate counterpart. This grants the attacker the ability to execute arbitrary code on the compromised system. Notably, the `ahost.exe` executable used in this campaign is signed by GitKraken, adding a layer of legitimacy that can deceive both users and security systems.
Broader Implications and Similar Attacks
This campaign underscores a growing trend where attackers exploit trusted, signed utilities to bypass security defenses. By leveraging legitimate software and manipulating its DLL loading process, threat actors can stealthily deploy powerful malware, enabling persistent remote access and data theft.
Similar techniques have been observed in other malware campaigns. For instance, the Quasar RAT has been known to utilize DLL side-loading to evade detection and exfiltrate data from compromised Windows systems. In this case, attackers used legitimate executables like `ctfmon.exe` and `calc.exe` to load malicious DLLs, highlighting the versatility and effectiveness of this method.
Mitigation Strategies
To defend against such sophisticated attacks, organizations should consider implementing the following measures:
1. Advanced Endpoint Detection and Response (EDR) Solutions: Traditional signature-based defenses are often insufficient against DLL side-loading attacks. Advanced EDR solutions can detect and respond to anomalous behaviors associated with such techniques.
2. Application Control Policies: Implementing strict application control policies can prevent unauthorized executables and DLLs from running, thereby reducing the risk of side-loading attacks.
3. Regular Software Audits: Conducting regular audits of software installations can help identify and remove unnecessary or potentially vulnerable applications.
4. User Education and Awareness: Training employees to recognize phishing attempts and suspicious files can reduce the likelihood of inadvertently executing malicious software.
5. Up-to-Date Threat Intelligence: Staying informed about the latest threats and attack vectors enables organizations to proactively adjust their security postures.
Conclusion
The exploitation of DLL side-loading vulnerabilities, particularly within widely used libraries like c-ares, represents a significant threat to organizational security. By understanding the mechanics of these attacks and implementing robust mitigation strategies, organizations can enhance their defenses against such sophisticated threats.