In the ever-evolving landscape of cybersecurity threats, a new and sophisticated malware framework named VoidLink has emerged, specifically targeting Linux-based cloud environments. Discovered in December 2025 by Check Point Research, VoidLink is engineered for prolonged, stealthy access to cloud infrastructures, posing significant risks to organizations worldwide.
Unveiling VoidLink: A Cloud-Native Menace
VoidLink is a cloud-first implant written in the Zig programming language, designed to seamlessly integrate into various cloud platforms, including Amazon Web Services (AWS), Google Cloud, Microsoft Azure, Alibaba, and Tencent. Its adaptability allows it to recognize and modify its behavior when operating within Docker containers or Kubernetes pods, making it particularly effective in modern cloud and containerized environments.
Modular Architecture and Plugin System
At the core of VoidLink’s potency is its highly modular architecture, centered around a custom Plugin API inspired by Cobalt Strike’s Beacon Object Files (BOF) approach. This framework supports over 30 plug-in modules, enabling operators to extend or alter its capabilities dynamically. The in-memory plugin system facilitates the addition of functionalities without leaving traces on disk, enhancing its stealth.
Command and Control (C2) Capabilities
VoidLink boasts a versatile command-and-control infrastructure, supporting multiple communication channels such as HTTP/HTTPS, WebSocket, ICMP, and DNS tunneling. This flexibility ensures reliable communication between the malware and its operators, even in restricted network environments. Notably, VoidLink can establish peer-to-peer (P2P) or mesh-style networks among compromised hosts, enabling coordinated attacks and data exfiltration without relying on a centralized C2 server.
Advanced Evasion Techniques
To maintain its covert presence, VoidLink employs sophisticated evasion strategies:
– Rootkit Deployment: Depending on the Linux kernel version, VoidLink utilizes different rootkit techniques:
– LD_PRELOAD: For kernels below version 4.0 or when kernel-level deployment is not feasible.
– Loadable Kernel Module (LKM): For kernels version 4.0 and above.
– eBPF (Extended Berkeley Packet Filter): For kernels version 5.5 and above with eBPF support.
These methods allow VoidLink to hide its processes, files, and network activities effectively.
– Adaptive Stealth Mechanisms: Upon execution, VoidLink assesses the security posture of the infected system, identifying installed security products and hardening measures. It then calculates a risk score and adjusts its behavior accordingly, such as slowing down port scans in highly monitored environments to avoid detection.
Comprehensive Post-Exploitation Modules
VoidLink’s extensive suite of post-exploitation modules includes:
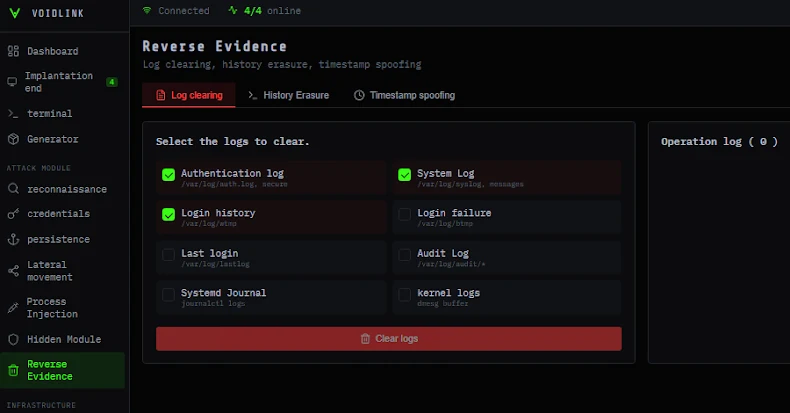
– Anti-Forensics: Capabilities to wipe or edit logs, clear shell history, and perform timestomping to hinder forensic analysis.
– Cloud Exploitation: Tools for Kubernetes and Docker discovery, privilege escalation, container escapes, and probing for misconfigurations.
– Credential Harvesting: Mechanisms to collect credentials and secrets, including SSH keys, Git credentials, local passwords, browser credentials and cookies, tokens, and API keys.
– Lateral Movement: An SSH-based worm to facilitate the spread to other systems within the network.
– Persistence: Techniques to establish long-term access through various persistence mechanisms.
Command and Control Dashboard
Operators of VoidLink are provided with a web-based dashboard, localized for Chinese-speaking users, offering complete control over the malware’s operations. The interface is organized into sections such as Dashboard, Attack, and Infrastructure, covering functionalities from agent management and implant building to post-exploitation activities like reconnaissance, credential access, persistence, lateral movement, process injection, stealth, and evidence wiping.
Implications and Recommendations
The emergence of VoidLink underscores a significant shift in cyber threats targeting Linux-based cloud environments. Its advanced capabilities and modular design make it a formidable tool for cyber espionage and data exfiltration.
Recommendations for Mitigation:
1. Regular System Updates: Ensure all systems, especially those running Linux, are updated with the latest security patches to mitigate vulnerabilities that VoidLink exploits.
2. Enhanced Monitoring: Implement comprehensive monitoring solutions capable of detecting anomalous activities, including unusual network traffic patterns and system behaviors indicative of rootkit presence.
3. Network Segmentation: Isolate critical systems and services to limit the lateral movement capabilities of malware like VoidLink.
4. Security Training: Educate staff on recognizing phishing attempts and other common attack vectors to prevent initial compromise.
5. Incident Response Planning: Develop and regularly update incident response plans to ensure swift action in the event of a breach.
By adopting these measures, organizations can bolster their defenses against sophisticated threats like VoidLink and safeguard their cloud infrastructures from potential compromise.