n8n Supply Chain Attack Exploits Community Nodes to Steal OAuth Tokens
In a recent and sophisticated supply chain attack, malicious actors have infiltrated the npm registry by uploading eight deceptive packages designed to target the n8n workflow automation platform. These packages masquerade as legitimate integrations, aiming to steal developers’ OAuth credentials.
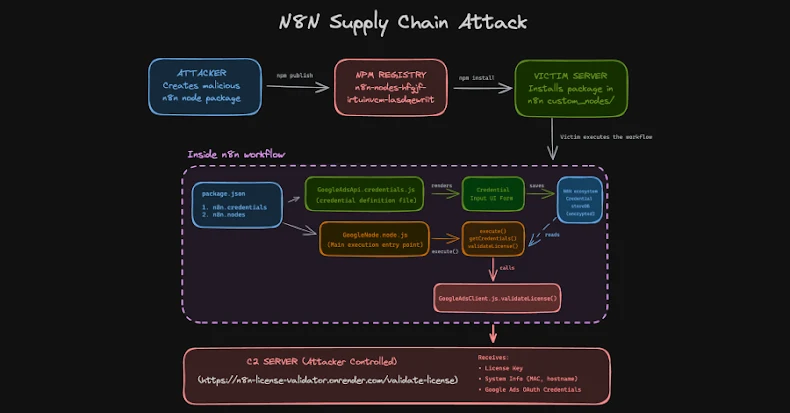
One particularly insidious package, named n8n-nodes-hfgjf-irtuinvcm-lasdqewriit, poses as a Google Ads integration. It prompts users to link their advertising accounts through a seemingly authentic form, only to siphon OAuth credentials to servers controlled by the attackers.
Endor Labs, in a recent report, highlighted the gravity of this attack:
The attack represents a new escalation in supply chain threats. Unlike traditional npm malware, which often targets developer credentials, this campaign exploited workflow automation platforms that act as centralized credential vaults – holding OAuth tokens, API keys, and sensitive credentials for dozens of integrated services like Google Ads, Stripe, and Salesforce in a single location.
The identified malicious packages, now removed from the npm registry, include:
– n8n-nodes-hfgjf-irtuinvcm-lasdqewriit (4,241 downloads, author: kakashi-hatake)
– n8n-nodes-ggdv-hdfvcnnje-uyrokvbkl (1,657 downloads, author: kakashi-hatake)
– n8n-nodes-vbmkajdsa-uehfitvv-ueqjhhhksdlkkmz (1,493 downloads, author: kakashi-hatake)
– n8n-nodes-performance-metrics (752 downloads, author: hezi109)
– n8n-nodes-gasdhgfuy-rejerw-ytjsadx (8,385 downloads, author: zabuza-momochi)
– n8n-nodes-danev (5,525 downloads, author: dan_even_segler)
– n8n-nodes-rooyai-model (1,731 downloads, author: haggags)
– n8n-nodes-zalo-vietts (4,241 downloads, authors: vietts_code and diendh)
Notably, npm users zabuza-momochi, dan_even_segler, and diendh are associated with four other libraries still available for download:
– n8n-nodes-gg-udhasudsh-hgjkhg-official (2,863 downloads)
– n8n-nodes-danev-test-project (1,259 downloads)
– @diendh/n8n-nodes-tiktok-v2 (218 downloads)
– n8n-nodes-zl-vietts (6,357 downloads)
While these packages have not been confirmed to contain malicious code, caution is advised. An updated version of n8n-nodes-gg-udhasudsh-hgjkhg-official was published recently, indicating that the campaign may still be active.
Once installed as a community node, the malicious package operates like any other n8n integration. It displays configuration screens and saves the Google Ads account OAuth tokens in encrypted format to the n8n credential store. However, during workflow execution, it decrypts these tokens using n8n’s master key and exfiltrates them to a remote server.
This incident marks the first known supply chain attack explicitly targeting the n8n ecosystem. By exploiting trust in community integrations, attackers have found a novel method to compromise sensitive credentials.
The implications of this attack are profound. Workflow automation platforms like n8n serve as centralized hubs, managing OAuth tokens, API keys, and other sensitive credentials for numerous integrated services. A breach in such a platform can lead to unauthorized access across multiple services, amplifying the potential damage.
Recommendations for Developers:
1. Audit Packages Before Installation: Thoroughly review packages before integrating them into your workflows.
2. Scrutinize Package Metadata: Look for anomalies in package metadata that might indicate malicious intent.
3. Use Official n8n Integrations: Prioritize official integrations over community nodes to minimize risk.
n8n has also issued a warning regarding the security risks associated with using community nodes from npm. They caution that such nodes can introduce breaking changes or execute malicious actions on the host machine.
In light of this attack, it’s imperative for developers and organizations to exercise heightened vigilance when integrating third-party packages. Regularly updating and monitoring dependencies, coupled with a robust security posture, can mitigate the risks associated with supply chain attacks.