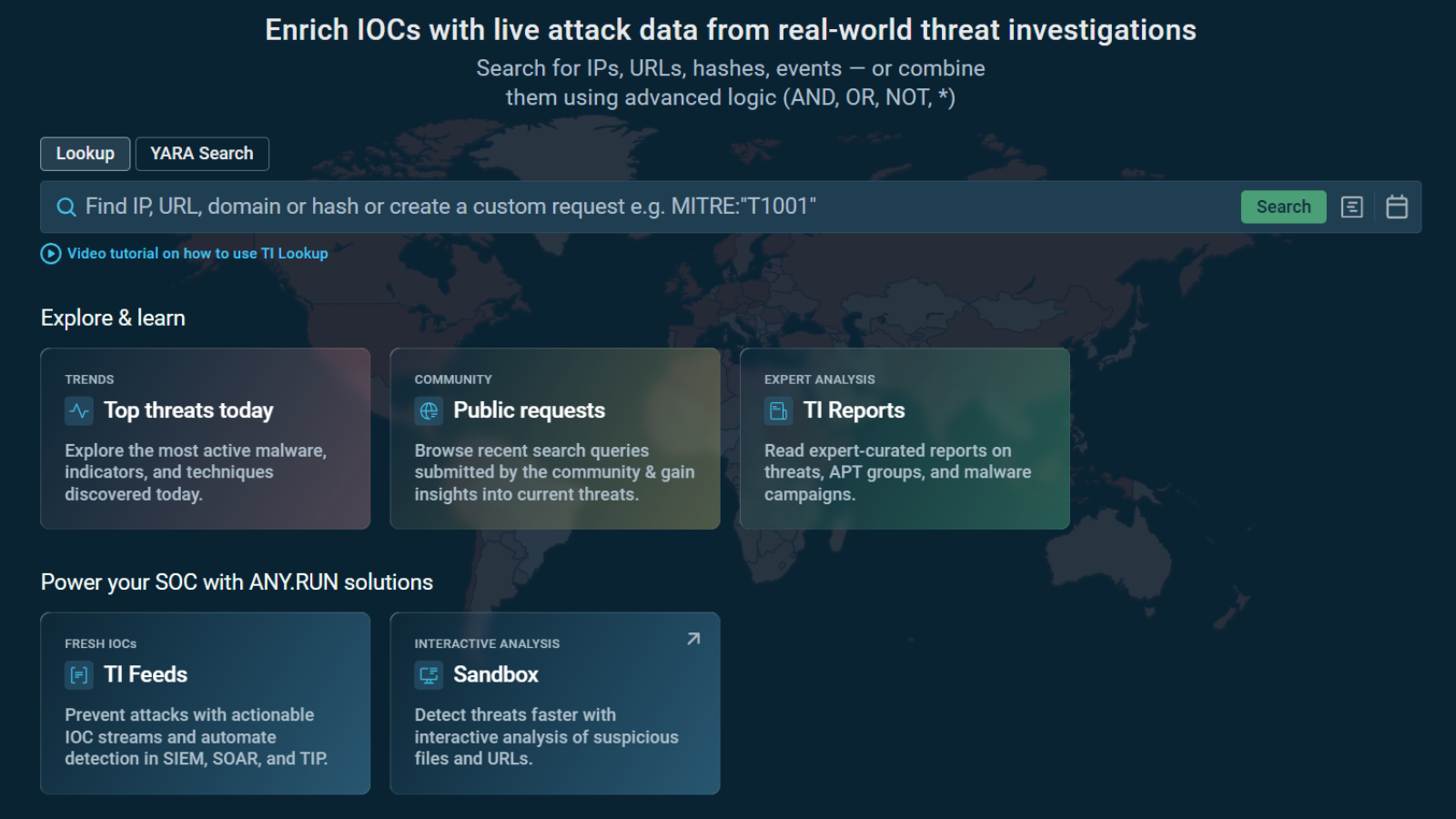
Security Operations Centers (SOCs) are the frontline defense against cyber threats, yet they often grapple with persistent challenges that hinder their effectiveness. By integrating high-quality threat intelligence into their operations, SOCs can address and overcome these obstacles, leading to enhanced performance and security posture.
1. Enhancing Detection Rates
Challenge: Traditional detection methods frequently fall short against sophisticated cyber threats, resulting in unsatisfactory detection rates. Attackers continually refine their tactics, making it imperative for SOCs to stay ahead.
Solution: Incorporating real-time threat intelligence provides SOCs with up-to-date information on emerging threats. By leveraging data from a vast network of SOC teams across various sectors, organizations can proactively identify and mitigate threats before they escalate.
Outcome:
– Proactive Threat Identification: Early detection of emerging threats allows for timely intervention.
– Expanded Threat Coverage: Monitoring the latest malware and phishing campaigns globally ensures comprehensive protection.
– Resource Efficiency: Reducing false positives minimizes wasted time and effort, allowing analysts to focus on genuine threats.
2. Accelerating Incident Response
Challenge: Slow incident response times, often due to a lack of automated processes and contextual information, can exacerbate the impact of cyber incidents.
Solution: Integrating threat intelligence that provides context to each indicator enables analysts to understand the behavior and impact of threats quickly. Access to detailed malware analysis reports linked to threat indicators facilitates informed decision-making and swift action.
Outcome:
– Deep Threat Visibility: Gaining actionable insights into malicious activities enhances understanding and response.
– Reduced Mean Time to Respond (MTTR): Organizations report significant reductions in response times per incident.
– Instant Threat Blocking: Seamless integration with security tools like SIEM, SOAR, or EDR allows for real-time playbook refinement and threat neutralization.
3. Managing Alert Overload
Challenge: SOCs often face an overwhelming volume of alerts, leading to backlogs and potential oversight of critical threats.
Solution: Implementing threat intelligence solutions that automate alert prioritization and provide comprehensive coverage helps SOCs manage and reduce alert fatigue. These solutions can detect even evasive or hidden malware, ensuring no threat goes unnoticed.
Outcome:
– Efficient Alert Management: Automation reduces the manual workload, allowing analysts to focus on high-priority threats.
– Comprehensive Threat Detection: Ensuring wide coverage minimizes the risk of missing critical threats.
– Streamlined Workflows: Quick verification of suspicious samples through threat intelligence lookups accelerates decision-making processes.
4. Addressing Skill Gaps
Challenge: The cybersecurity industry faces a shortage of skilled professionals, making it challenging for SOCs to maintain a team capable of handling complex threats.
Solution: Utilizing threat intelligence platforms that offer user-friendly interfaces and actionable insights can bridge skill gaps. These platforms empower less experienced analysts to make informed decisions and respond effectively to incidents.
Outcome:
– Empowered Analysts: Providing tools that simplify threat analysis enables all team members to contribute effectively.
– Consistent Decision-Making: Standardized threat intelligence ensures uniform responses to incidents.
– Enhanced Training: Access to real-world threat data serves as a valuable resource for ongoing education and skill development.
5. Ensuring Compliance and Reporting
Challenge: Meeting regulatory requirements and generating accurate reports can be time-consuming and complex for SOCs.
Solution: Threat intelligence solutions that include reporting features and compliance tracking can simplify these processes. Automated generation of reports and monitoring of compliance metrics ensure that SOCs meet regulatory standards efficiently.
Outcome:
– Simplified Compliance: Automated tracking and reporting reduce the burden of manual compliance checks.
– Accurate Reporting: Consistent and detailed reports provide clear insights into security posture and incidents.
– Audit Readiness: Maintaining comprehensive records ensures preparedness for audits and assessments.
Conclusion
Integrating high-quality threat intelligence into SOC operations addresses critical challenges, leading to improved detection rates, faster incident response, efficient alert management, skill gap mitigation, and streamlined compliance processes. By adopting these solutions, organizations can enhance their security posture and effectively safeguard against evolving cyber threats.