Critical MongoDB Vulnerability CVE-2025-14847 Actively Exploited Globally
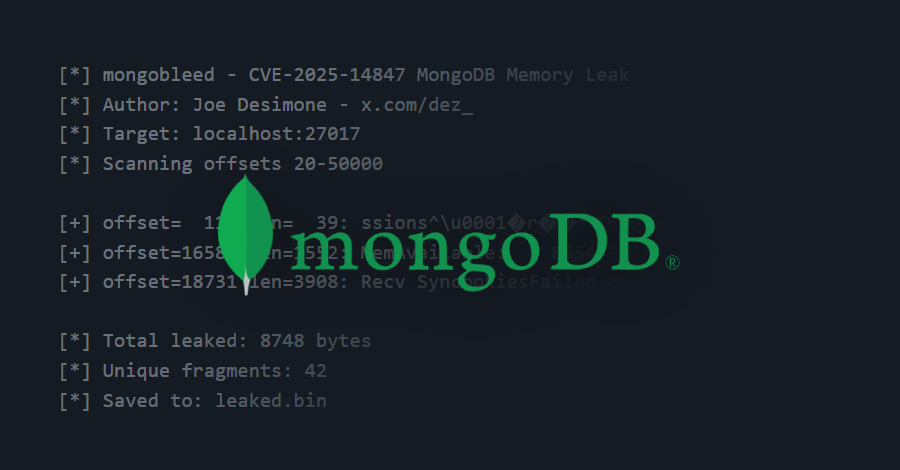
A significant security flaw in MongoDB, identified as CVE-2025-14847 with a CVSS score of 8.7, is currently under active exploitation worldwide. This vulnerability, dubbed MongoBleed, enables unauthenticated attackers to remotely extract sensitive data from the server’s memory.
Technical Details:
The root cause of this vulnerability lies in MongoDB Server’s implementation of zlib message decompression, specifically within the message_compressor_zlib.cpp file. By sending malformed network packets, attackers can exploit this flaw to leak fragments of private data, including user information, passwords, and API keys. The issue arises because the affected logic returns the allocated buffer size instead of the actual decompressed data length, allowing undersized or malformed payloads to expose adjacent heap memory.
Scope of the Threat:
Data from attack surface management company Censys indicates that over 87,000 MongoDB instances are potentially vulnerable, with the highest concentrations in the United States, China, Germany, India, and France. Cloud security firm Wiz reports that 42% of cloud environments have at least one instance of MongoDB running a version susceptible to CVE-2025-14847, encompassing both internet-exposed and internal resources.
Mitigation Measures:
To address this critical vulnerability, users are strongly advised to update their MongoDB installations to the latest patched versions:
– MongoDB 8.2.3
– MongoDB 8.0.17
– MongoDB 7.0.28
– MongoDB 6.0.27
– MongoDB 5.0.32
– MongoDB 4.4.30
For those unable to immediately apply these updates, the following temporary workarounds are recommended:
1. Disable zlib Compression: Start the MongoDB server (`mongod` or `mongos`) with the `networkMessageCompressors` or `net.compression.compressors` option set to exclude zlib.
2. Restrict Network Exposure: Limit the network accessibility of MongoDB servers to trusted sources only.
3. Monitor Logs: Regularly review MongoDB logs for any unusual pre-authentication connection attempts.
Broader Implications:
It’s noteworthy that this vulnerability also affects the Ubuntu rsync package due to its use of zlib. Therefore, administrators should ensure that all systems utilizing zlib are reviewed and updated accordingly to prevent potential exploitation.
Conclusion:
The active exploitation of CVE-2025-14847 underscores the critical need for prompt action. Organizations must prioritize updating their MongoDB instances and implementing the recommended mitigations to safeguard sensitive data and maintain system integrity.