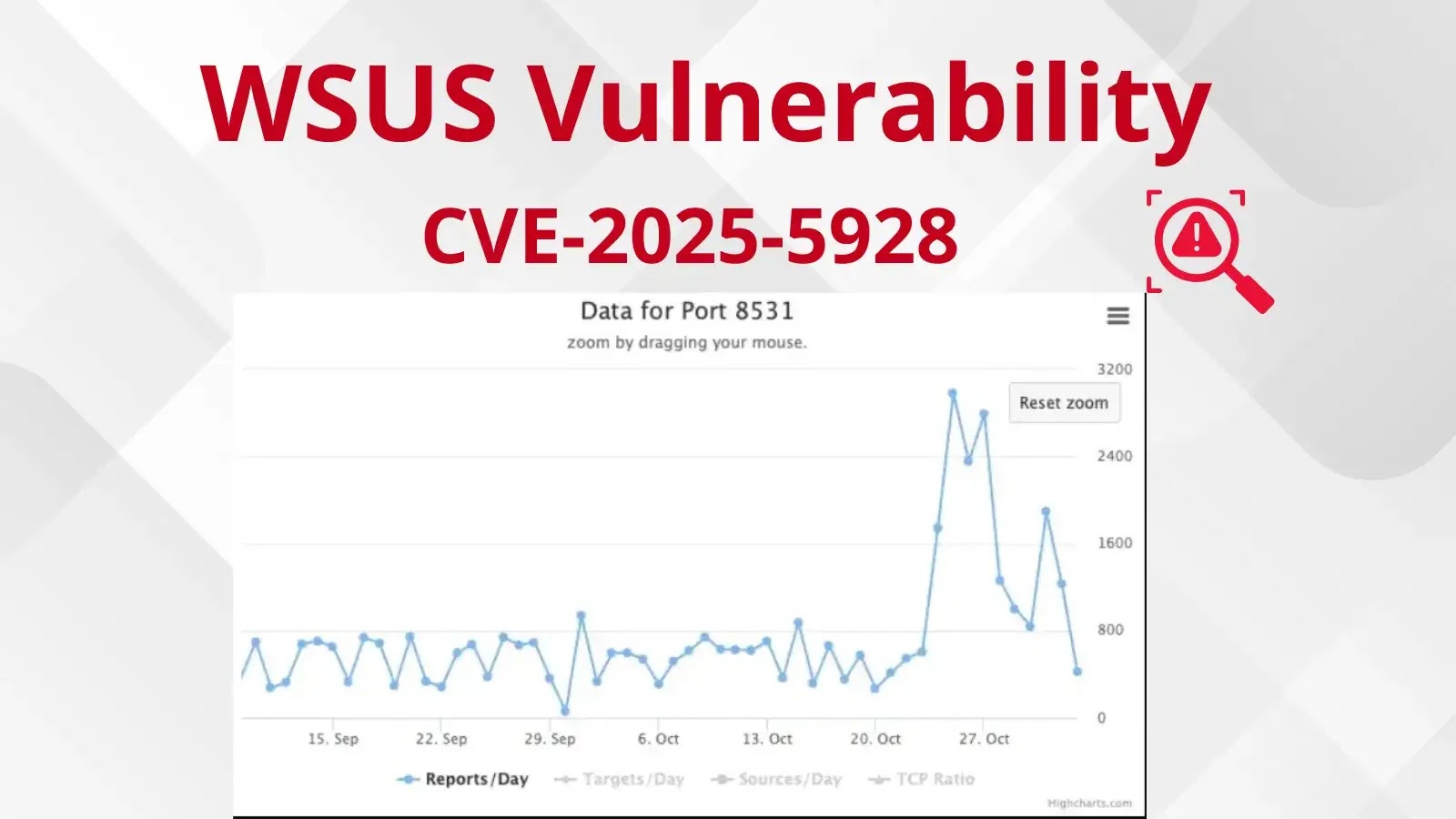
Critical Use-After-Free Vulnerability in Linux Kernel’s POSIX CPU Timers Exposed
A significant security flaw, identified as CVE-2025-38352, has been discovered in the Linux kernel’s implementation of POSIX CPU timers. This vulnerability arises from a race condition within the `handle_posix_cpu_timers()` function, potentially allowing attackers to exploit use-after-free conditions in kernel memory. Such exploitation could lead to privilege escalation and full system compromise.
Technical Details:
The core of this vulnerability lies in the `handle_posix_cpu_timers()` function, responsible for processing timer signals during CPU scheduler ticks. A race condition exists between the collection and processing of firing timers, creating a window where an attacker can free timer structures while they are still in use. This flaw is particularly concerning for systems with the `CONFIG_POSIX_CPU_TIMERS_TASK_WORK` configuration disabled, notably affecting 32-bit Android devices.
Affected Systems:
The vulnerability impacts Linux LTS version 6.12.33 and related builds, especially those utilized in 32-bit Android kernels. Exploitation requires specific conditions:
– A process must enter a zombie state.
– Precise timing coordination is necessary to trigger the race condition.
Proof-of-Concept Exploit:
Security researcher Faraz Sth has publicly released a proof-of-concept (PoC) exploit demonstrating the vulnerability’s potential impact. The exploit involves:
1. Creating a POSIX CPU timer set to fire after a designated CPU time interval.
2. Forcing a thread into a zombie state during critical kernel operations.
3. Reaping the zombie task while timer processing is ongoing.
4. Deleting the timer via the `timer_delete()` syscall, leading to premature memory deallocation.
5. Triggering a use-after-free condition as the kernel continues accessing the freed timer.
Successful execution of this exploit results in Kernel Address Sanitizer (KASAN) warnings, indicating use-after-free write operations within the `posix_timer_queue_signal()` function. On systems without KASAN, kernel warnings appear in the `send_sigqueue()` function.
Implications:
While exploiting this vulnerability requires local system access and precise timing, successful exploitation could grant attackers elevated kernel privileges, leading to complete system control. Reports suggest that this flaw has been actively exploited in limited, targeted attacks, underscoring the urgency for remediation.
Mitigation and Recommendations:
The Linux kernel development team has released patches through stable branches to address this vulnerability. The fix prevents zombie processes from executing timer handling code, effectively eliminating the race condition window.
System administrators and users are strongly advised to:
– Update to the latest patched kernel versions immediately.
– Prioritize patching, especially for Android devices and embedded Linux systems running vulnerable kernel versions.
The public availability of the PoC exploit increases the risk for unpatched systems, making prompt action essential.
Conclusion:
The discovery of CVE-2025-38352 highlights the critical importance of timely vulnerability management within the Linux ecosystem. As attackers continue to exploit such flaws, maintaining up-to-date systems and applying security patches promptly remain paramount in safeguarding against potential threats.