Emergence of Udados Botnet: A New Threat to Tech and Telecom Sectors
A newly identified malware family, known as Udados, has surfaced as a formidable threat to the Technology and Telecommunications industries. This botnet orchestrates high-volume HTTP flood Distributed Denial-of-Service (DDoS) attacks, aiming to disrupt business operations by inundating target servers with seemingly legitimate traffic.
Operational Mechanism of Udados
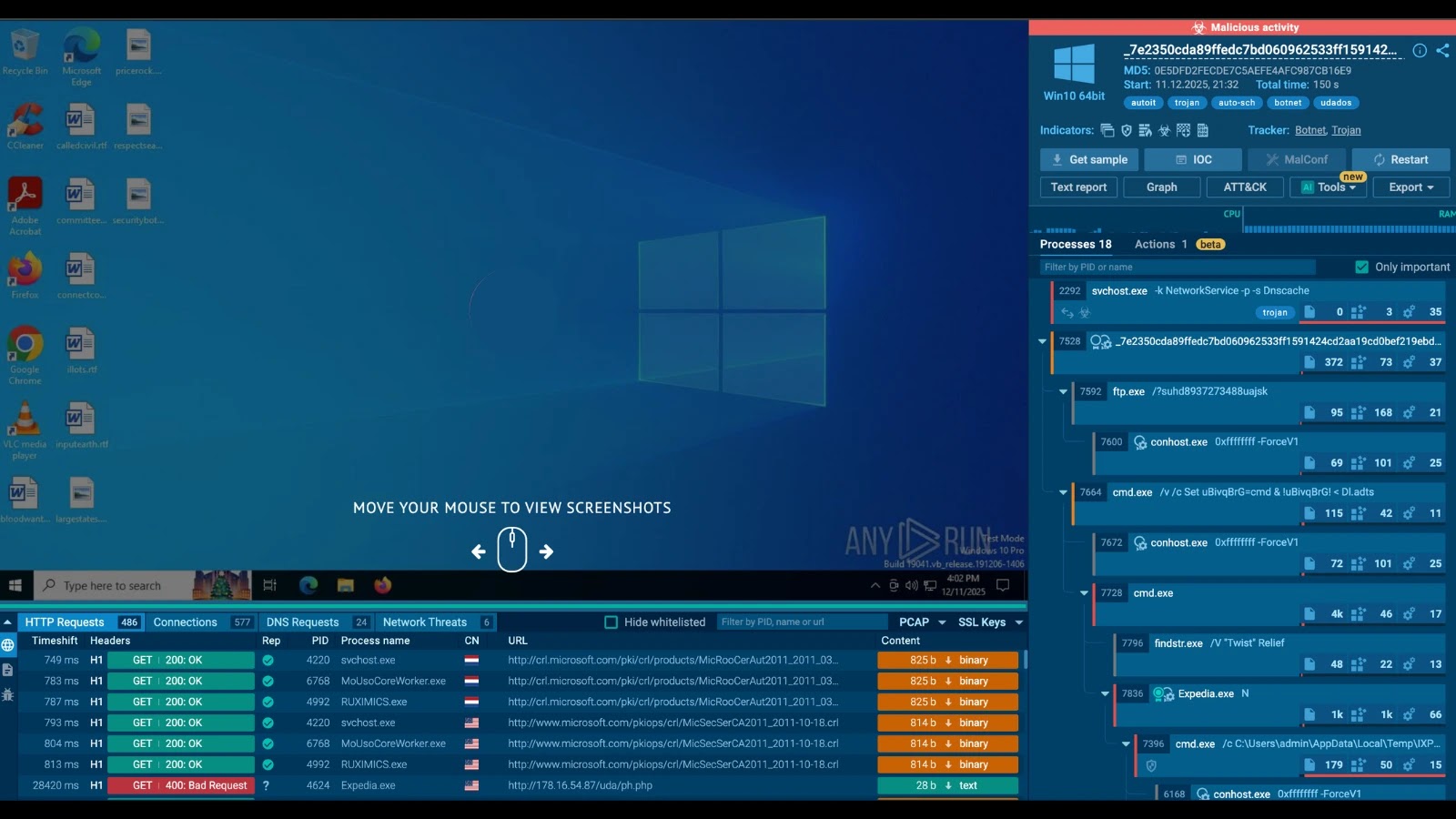
Udados operates by infecting hosts and establishing communication with a Command and Control (C2) server to receive attack directives. Upon infection, compromised systems transmit structured JSON data to the C2 server, encompassing critical system metadata such as user ID (Uid), task execution status (St), bot version (Bv), and privilege level (Priv). This telemetry enables the botnet operator to manage and coordinate the infected hosts effectively.
Once the initial check-in is complete, the C2 server issues specific attack commands. A primary directive observed is the !httppost command, which activates the DDoS module. This command specifies parameters including the attack duration (e.g., 888 seconds), the number of concurrent threads (e.g., 88), and a Base64-encoded payload containing random data.
By utilizing HTTP POST requests, the attack traffic closely resembles legitimate web traffic, complicating detection and mitigation efforts for network defenders.
Infrastructure and Network Indicators
The Udados botnet’s infrastructure is hosted within Autonomous System AS214943, also known as RAILNET. This network has recently been associated with malicious activities, hosting infrastructure for over 30 distinct malware families in late 2025, including significant threats like Remcos and Amadey.
The specific C2 server identified in this campaign is located at IP address 178.16.54[.]87. The malware communicates via the URI /uda/ph.php, serving as a critical indicator for network monitoring. Defenders can detect potential infections by inspecting outbound HTTP traffic for this specific path and the characteristic JSON parameters (uid, st, msg, tid) in the request body.
Mitigation Strategies
Organizations are advised to take the following actions to mitigate the threat posed by the Udados botnet:
– Block Traffic to Identified C2 Infrastructure: Implement firewall rules to block outbound traffic to the identified C2 server at IP address 178.16.54[.]87.
– Monitor for Indicators of Compromise (IoCs): Regularly inspect network logs for the following IoCs:
– SHA256 Hashes:
– 7e2350cda89ffedc7bd060962533ff1591424cd2aa19cd0bef219ebd576566bb
– 770d78f34395c72191c8b865c08b08908dff6ac572ade06396d175530b0403b8
– IPv4 Address: 178.16.54[.]87
– Domain: ryxuz[.]com
– URI Path: /uda/ph.php
– Inspect for Unusual Outbound HTTP Traffic: Monitor for short-term spikes in outbound HTTP traffic from individual hosts, as this behavior often precedes high-volume flood attacks orchestrated by the C2 server.
Conclusion
The emergence of the Udados botnet underscores the evolving landscape of cyber threats targeting the Technology and Telecommunications sectors. By leveraging infected hosts to execute sophisticated HTTP flood DDoS attacks, Udados poses a significant risk to business continuity. Organizations must remain vigilant, implementing robust monitoring and mitigation strategies to detect and neutralize such threats promptly.