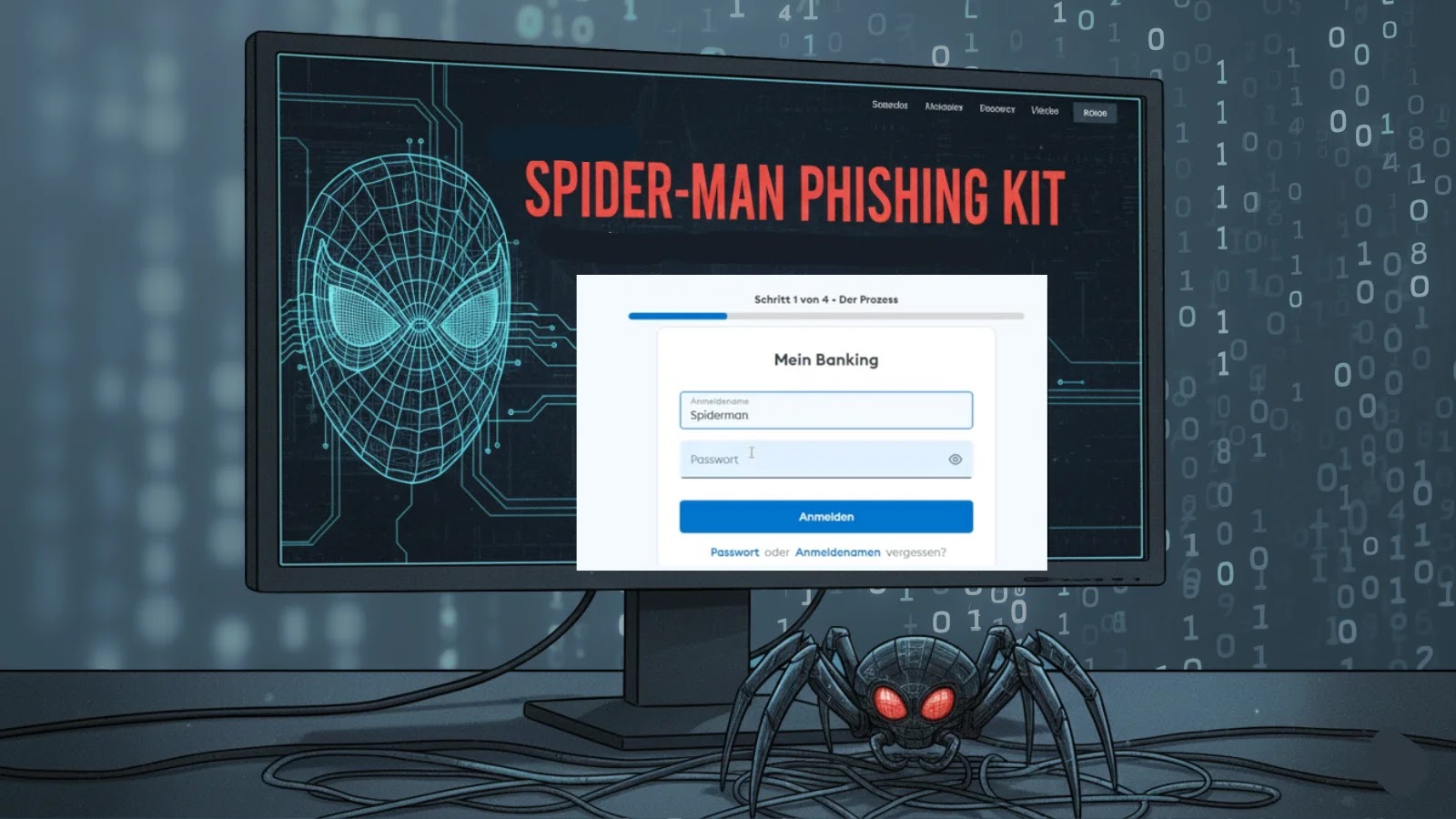
Spiderman Phishing Kit: A New Threat to Bank Security
A new phishing framework named Spiderman has surfaced in the cybercrime community, significantly simplifying the process of creating fraudulent banking login pages. This toolkit enables cybercriminals, even those with minimal technical expertise, to generate accurate replicas of legitimate banking portals with just a few clicks. The primary targets are customers of numerous European financial institutions and cryptocurrency platforms, indicating a concerning advancement in automated cybercrime tools.
Key Features of the Spiderman Phishing Kit:
1. User-Friendly Interface: Spiderman’s design allows attackers to select a target institution from a menu and automatically generate a convincing clone of the bank’s login page. This includes login fields, password prompts, and brand-specific aesthetics, eliminating the need for web development skills.
2. Multi-Target Capability: The kit consolidates targeting for multiple major brands, such as Deutsche Bank, Commerzbank, ING (Germany & Belgium), and CaixaBank, into a single interface. This enables attackers to switch between different institutions and regions swiftly, maintaining a broad range of attacks across various countries.
3. Advanced Security Evasion: Spiderman includes modules designed to bypass two-factor authentication (2FA) by capturing PhotoTAN codes and One-Time Passwords (OTPs) in real-time. As victims enter their credentials on the fraudulent page, attackers can view the session live through a dashboard, allowing them to prompt for additional information like credit card numbers or secondary authentication codes needed for unauthorized transactions.
4. Anti-Detection Measures: The kit employs sophisticated filtering to evade detection by security researchers and automated scanners. Attackers can configure the platform to allow traffic only from specific countries or device types (such as iOS or Android) while blocking known security vendors, data centers, and VPNs. This selective filtering helps keep the phishing pages active longer before being blacklisted.
5. Cryptocurrency Theft Support: Spiderman also targets cryptocurrency assets by capturing seed phrases for wallets like Ledger, MetaMask, and Exodus. This indicates that operators are pursuing a hybrid fraud strategy, targeting both traditional banking and digital assets.
Implications and Recommendations:
The emergence of the Spiderman phishing kit represents a significant escalation in the accessibility and effectiveness of phishing attacks. Its user-friendly design and advanced features lower the barrier to entry for cybercriminals, potentially leading to an increase in phishing campaigns targeting financial institutions and their customers.
To mitigate the risks associated with such sophisticated phishing kits, financial institutions and users should consider the following measures:
– Enhanced Security Protocols: Implement multi-layered security measures, including advanced 2FA methods that are less susceptible to interception.
– User Education: Regularly educate customers about the dangers of phishing attacks and the importance of verifying the authenticity of banking communications.
– Monitoring and Detection: Utilize advanced monitoring tools to detect and respond to phishing attempts promptly.
– Regular Updates: Keep security systems and protocols updated to address emerging threats effectively.
As cybercriminals continue to develop more sophisticated tools like Spiderman, it is crucial for both financial institutions and customers to remain vigilant and proactive in their cybersecurity practices.