Article Title:
Microsoft Quietly Patches Long-Exploited Windows LNK Vulnerability
In November 2025, Microsoft discreetly addressed a longstanding vulnerability in Windows shortcut (.lnk) files, identified as CVE-2025-9491. This flaw had been actively exploited by cybercriminals since 2017 to conceal malicious commands within shortcut files, effectively deceiving users who inspected file properties.
Discovery and Initial Response
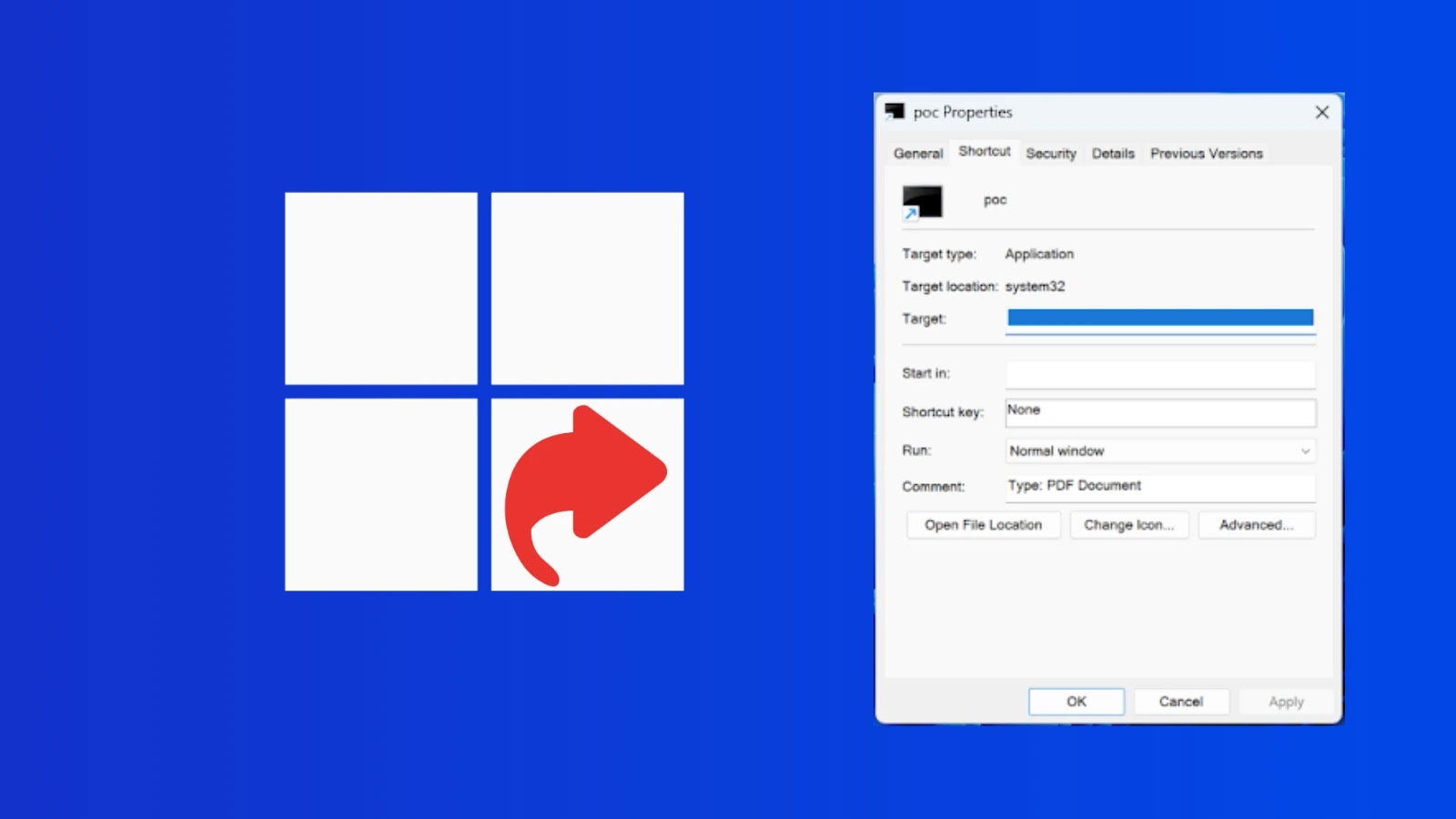
The vulnerability first gained public attention on March 18, 2025, when Trend Micro’s Zero Day Initiative (ZDI) published Advisory ZDI-25-148. Researchers Peter Girnus and Aliakbar Zahravi detailed how attackers crafted malicious .lnk files that exploited a limitation in the Windows Properties dialog. Specifically, the dialog displayed only the first 260 characters of the Target field, allowing any commands beyond this limit to remain hidden from users.
Despite being notified of the issue in September 2024, Microsoft initially declined to release a patch, stating that the vulnerability did not meet its servicing criteria. The company emphasized that existing security measures, such as the Mark of the Web (MoTW) feature, provided sufficient protection by warning users about files from untrusted sources.
Escalation and Active Exploitation
The situation escalated in late October 2025 when Arctic Wolf researchers reported that a Chinese-affiliated threat actor, UNC6384, was actively exploiting the vulnerability. The group targeted Hungarian and Belgian diplomatic entities during September and October 2025, deploying PlugX malware through weaponized .lnk files. These files leveraged the UI misrepresentation flaw to conceal malicious PowerShell commands, effectively bypassing user scrutiny.
Despite evidence of active exploitation, Microsoft maintained its stance. In Advisory ADV25258226, the company reiterated that due to the required user interaction and existing security warnings for untrusted file formats, the issue was not considered a vulnerability. Microsoft highlighted that users receive warnings when opening files from the internet, although these protections can be circumvented through known vulnerabilities.
Silent Patch Implementation
In November 2025, Microsoft included a fix for CVE-2025-9491 in its Patch Tuesday updates without explicitly acknowledging it among the 63 officially patched vulnerabilities. The update modified how Windows displays .lnk file properties, ensuring that the Properties dialog now shows the entire Target command regardless of length. However, the information remains in a single-line field, requiring users to select and scroll to view the complete command.
Alternative Solutions and Recommendations
In response to the vulnerability, ACROS Security developed a micropatch that takes a more proactive approach. Their solution truncates any .lnk file Target field exceeding 260 characters when opened through Windows Explorer and alerts users about the suspicious activity. This method aims to block the over 1,000 malicious shortcuts identified by Trend Micro while preserving functionality for legitimate shortcuts created through standard Windows interfaces.
The exploitation of this vulnerability underscores the challenges associated with UI-based security issues, where attackers manipulate users’ trust in the operating system’s interface. Security experts recommend that organizations implement additional endpoint detection capabilities and conduct security awareness training to help users recognize suspicious shortcut files, particularly those received via email or downloaded from untrusted sources.