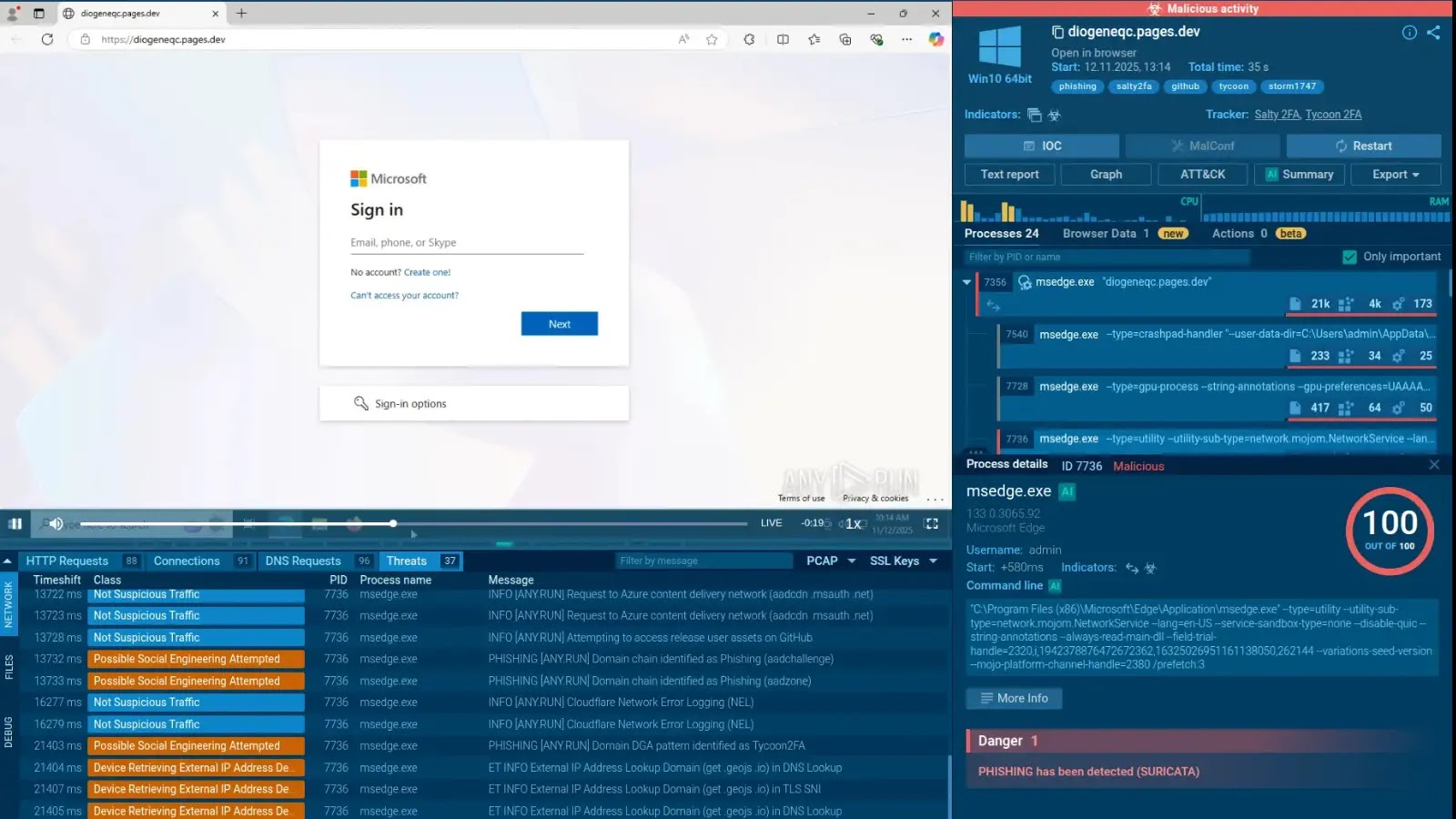
Emerging Threat: Salty2FA and Tycoon2FA Phishing Kits Target Enterprise Credentials
In the ever-evolving landscape of cyber threats, a new and sophisticated phishing attack has emerged, combining elements from two notorious phishing kits: Salty2FA and Tycoon2FA. This fusion signifies a notable shift in the Phishing-as-a-Service (PhaaS) domain, presenting heightened challenges for cybersecurity defenses.
Understanding the Phishing Kits
Traditionally, phishing kits like Salty2FA and Tycoon2FA have operated independently, each with distinct code structures and delivery methods. Salty2FA is recognized for its advanced techniques in bypassing multi-factor authentication (MFA) through adversary-in-the-middle (AiTM) strategies. Similarly, Tycoon2FA employs sophisticated evasion tactics to intercept credentials and session tokens, effectively circumventing MFA protections.
The Convergence of Salty2FA and Tycoon2FA
Recent analyses have uncovered a convergence of these two kits in phishing campaigns targeting enterprise users. This amalgamation complicates attribution efforts and suggests potential collaboration or operational merging between the threat actors behind these tools.
The decline in standalone Salty2FA activity observed in late 2025 coincides with the emergence of hybrid samples where Salty2FA’s infrastructure fails, triggering a fallback mechanism that retrieves Tycoon2FA payloads. This seamless transition indicates that the operators anticipated infrastructure instability and engineered redundancy using a rival or partner kit.
Technical Analysis of the Hybrid Attack Mechanism
Code-level analysis reveals that these hybrid payloads initiate with Salty2FA’s traditional trampoline scripts, designed to load the next stage of the attack. However, when the primary Salty2FA domains fail to resolve, the scripts execute a hardcoded fallback command, fetching malicious content from Tycoon2FA infrastructure.
This structural similarity suggests that Salty2FA may not be an independent competitor but rather another tool in the arsenal of a known threat group, potentially used for different targeting profiles or as a testing ground for new evasion features.
Implications for Cybersecurity Defenses
For security operations centers (SOCs), the blurring of lines between Salty2FA and Tycoon2FA necessitates an updated defense strategy. Reliance on static indicators of compromise (IOCs) for a single kit is no longer sufficient, as a campaign might pivot from one framework to another mid-execution.
Experts recommend treating these kits as a single threat cluster. Defenders should correlate alerts involving Salty2FA’s initial delivery vectors, such as HTML trampoline files, with Tycoon2FA’s known network behaviors, including traffic to domain generation algorithm (DGA)-generated domains and fast-flux infrastructure.
Recommendations for Mitigation
To effectively counteract these evolving threats, organizations should consider implementing the following measures:
1. Enhanced Behavioral Analysis: Deploy advanced behavioral analysis tools capable of detecting anomalies indicative of phishing attacks, regardless of the specific kit used.
2. Comprehensive Employee Training: Conduct regular training sessions to educate employees about the latest phishing tactics and the importance of vigilance when handling emails and attachments.
3. Multi-Layered Authentication: Implement robust multi-factor authentication methods that are resistant to AiTM attacks, such as hardware tokens or biometric verification.
4. Regular Security Audits: Perform frequent security audits to identify and remediate vulnerabilities that could be exploited by phishing kits.
5. Incident Response Planning: Develop and regularly update incident response plans to ensure swift action in the event of a phishing attack, minimizing potential damage.
Conclusion
The fusion of Salty2FA and Tycoon2FA phishing kits represents a significant evolution in cyber threats targeting enterprise credentials. By understanding the mechanics of these hybrid attacks and implementing comprehensive defense strategies, organizations can bolster their resilience against such sophisticated phishing campaigns.