ToddyCat’s Advanced Tactics: Unveiling New Tools for Email and Credential Theft
The cyber threat group known as ToddyCat has recently enhanced its arsenal with sophisticated tools designed to infiltrate corporate email systems and extract sensitive data. These developments underscore the group’s evolving strategies and the persistent threat they pose to organizations worldwide.
Introduction to ToddyCat’s Recent Activities
Active since at least 2020, ToddyCat has a history of targeting organizations across Europe and Asia. Their operations have consistently involved deploying advanced malware to maintain access and exfiltrate data. Recent analyses have revealed the group’s adoption of new methods to compromise corporate email systems, particularly focusing on Microsoft Outlook and Microsoft 365 platforms.
Exploitation of ESET Vulnerability
In April 2025, ToddyCat was linked to the exploitation of a security flaw in the ESET Command Line Scanner (CVE-2024-11859, CVSS score: 6.8). This vulnerability was leveraged to deliver a previously undocumented malware named TCESB. This malware facilitated unauthorized access and data exfiltration, highlighting the group’s ability to exploit software vulnerabilities to achieve their objectives.
Introduction of TCSectorCopy
One of the notable tools recently employed by ToddyCat is TCSectorCopy, a custom-developed utility designed to extract data from Microsoft Outlook’s Offline Storage Table (OST) files. OST files store a local copy of emails, calendar events, and other mailbox items, allowing users to access their data offline. Accessing these files while Outlook is running is typically restricted to prevent data corruption. However, TCSectorCopy circumvents these restrictions by reading the disk at a low level, copying the OST file sector by sector. Once the OST files are duplicated, ToddyCat utilizes XstReader, an open-source tool, to parse and extract the contents, thereby gaining access to a wealth of corporate communications.
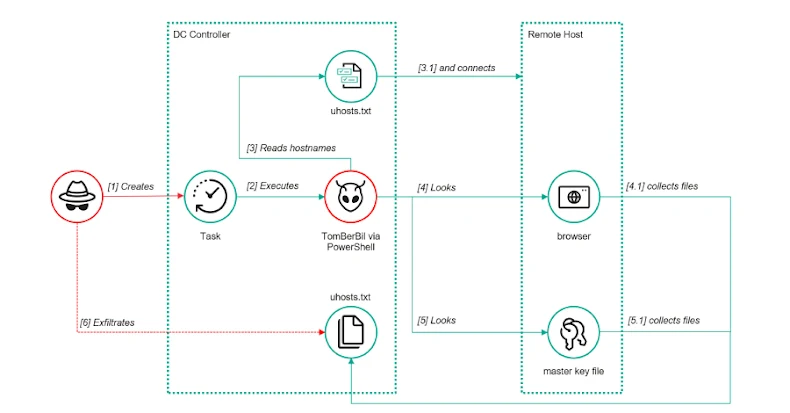
Enhancements to TomBerBil
ToddyCat has also updated its TomBerBil malware, introducing a PowerShell variant that targets Mozilla Firefox. This version operates on domain controllers with elevated privileges, accessing browser files over shared network resources via the SMB protocol. The malware searches for browser history, cookies, and saved credentials on remote hosts. Although these files are encrypted using the Windows Data Protection API (DPAPI), TomBerBil captures the necessary encryption keys, allowing attackers to decrypt and access the sensitive information.
Targeting Microsoft 365 Access Tokens
In addition to local email data, ToddyCat has developed methods to obtain access tokens for Microsoft 365 services. By utilizing SharpTokenFinder, an open-source C# tool, the group enumerates Microsoft 365 applications to locate plaintext authentication tokens stored in memory. These tokens can be used to access corporate emails and other services from outside the compromised infrastructure. In instances where security software blocks attempts to dump the Outlook.exe process, ToddyCat has employed ProcDump from the Sysinternals suite to create memory dumps, circumventing security measures and extracting the desired tokens.
Implications and Recommendations
ToddyCat’s continuous development of sophisticated tools and techniques underscores the evolving nature of cyber threats. Organizations must remain vigilant and adopt comprehensive security measures to protect against such advanced persistent threats. Recommendations include:
– Regular Software Updates: Ensure all software, especially security tools, are up-to-date to mitigate known vulnerabilities.
– Enhanced Monitoring: Implement advanced monitoring solutions to detect unusual activities, such as unauthorized access to OST files or unexpected memory dumps.
– User Education: Train employees on recognizing phishing attempts and the importance of not storing sensitive information, like passwords, in browsers.
– Access Controls: Enforce strict access controls and least privilege principles to limit the potential impact of a compromised account.
– Incident Response Planning: Develop and regularly update incident response plans to quickly address and mitigate breaches.
By adopting these measures, organizations can enhance their resilience against sophisticated threat actors like ToddyCat and protect their critical assets from unauthorized access and data exfiltration.