Critical Vulnerabilities in Fluent Bit Threaten Cloud Infrastructure Security
Fluent Bit, a widely adopted open-source telemetry agent, has recently been found to contain multiple critical vulnerabilities that could jeopardize cloud infrastructures. These flaws, if exploited, may allow attackers to bypass authentication, execute arbitrary code remotely, and manipulate log data, posing significant risks to cloud services and Kubernetes environments.
Overview of Fluent Bit
Fluent Bit serves as a lightweight and high-performance log processor and forwarder, integral to collecting and processing telemetry data across diverse environments, from constrained systems to complex cloud infrastructures. Its efficiency and flexibility have led to its widespread adoption among major cloud providers and enterprises.
Identified Vulnerabilities
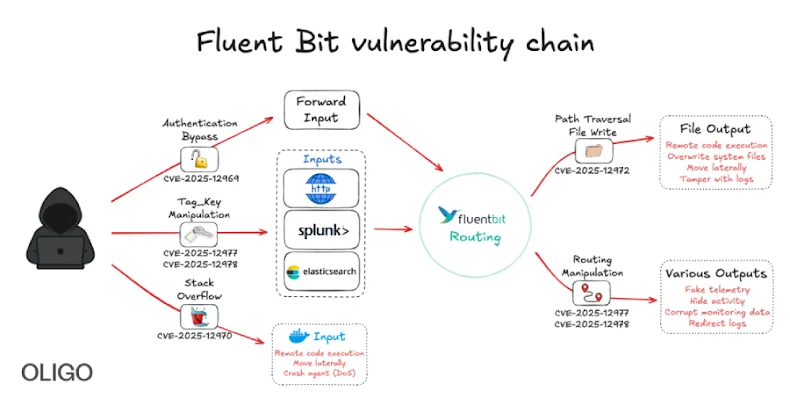
Security researchers have uncovered five critical vulnerabilities within Fluent Bit:
1. CVE-2025-12972: This path traversal vulnerability arises from the use of unsanitized tag values to generate output filenames. Attackers can exploit this flaw to write or overwrite arbitrary files on disk, potentially leading to log tampering and remote code execution.
2. CVE-2025-12970: A stack buffer overflow vulnerability exists in the Docker Metrics input plugin (`in_docker`). By creating containers with excessively long names, attackers can trigger code execution or crash the Fluent Bit agent.
3. CVE-2025-12978: This vulnerability in the tag-matching logic allows attackers to spoof trusted tags by guessing only the first character of a `Tag_Key`. Such exploitation enables rerouting logs, bypassing filters, and injecting malicious or misleading records under trusted tags.
4. CVE-2025-12977: Improper input validation of tags derived from user-controlled fields permits attackers to inject newlines, traversal sequences, and control characters, potentially corrupting downstream logs.
5. CVE-2025-12969: The `in_forward` plugin lacks proper authentication (`security.users`), allowing attackers to send logs, inject false telemetry, and flood security product logs with false events.
Potential Impact
Exploitation of these vulnerabilities could have severe consequences, including:
– Remote Code Execution (RCE): Attackers may execute arbitrary code within the cloud environment, leading to unauthorized access and control.
– Denial-of-Service (DoS): Malicious actors can disrupt cloud services by crashing Fluent Bit instances, rendering logging and monitoring services unavailable.
– Data Manipulation: By altering log data, attackers can erase or rewrite entries to conceal malicious activities, inject false telemetry, and mislead incident responders.
Mitigation Measures
To address these vulnerabilities, the following steps are recommended:
1. Update Fluent Bit: Users should upgrade to versions 4.1.1 or 4.0.12, which contain patches for these vulnerabilities.
2. Restrict Network Access: Limit access to Fluent Bit instances to trusted networks and users to reduce the risk of exploitation.
3. Sanitize Inputs: Ensure that all input data, especially tags and filenames, are properly validated and sanitized to prevent injection attacks.
4. Implement Authentication: Configure authentication mechanisms for all Fluent Bit plugins to prevent unauthorized access and data manipulation.
5. Monitor Logs: Regularly review logs for unusual activities or anomalies that may indicate exploitation attempts.
Conclusion
The discovery of these critical vulnerabilities in Fluent Bit underscores the importance of proactive security measures in cloud environments. Organizations must promptly apply patches, enforce strict access controls, and maintain vigilant monitoring to safeguard their infrastructures against potential attacks.