Matrix Push C2: Exploiting Browser Notifications for Stealthy, Cross-Platform Phishing Attacks
Cybercriminals are increasingly exploiting browser notifications to execute sophisticated phishing attacks through a novel command-and-control (C2) platform known as Matrix Push C2. This browser-native, fileless framework utilizes push notifications, deceptive alerts, and link redirects to target users across various operating systems.
In these schemes, potential victims are manipulated into enabling browser notifications via social engineering tactics on either malicious or compromised legitimate websites. Once permission is granted, attackers exploit the web push notification system inherent in browsers to dispatch alerts that mimic legitimate messages from the operating system or the browser itself. These counterfeit notifications often feature trusted branding, recognizable logos, and persuasive language to enhance their credibility.
Examples of such deceptive alerts include warnings about suspicious account logins or prompts for browser updates, accompanied by Verify or Update buttons. Clicking these buttons redirects victims to fraudulent websites designed to harvest sensitive information.
A notable aspect of this technique is its ability to operate entirely within the browser environment, eliminating the need for traditional malware installation. This method bears resemblance to the ClickFix attack, where users are tricked into compromising their own systems by following malicious instructions, effectively circumventing standard security measures.
Furthermore, since the attack is executed through the web browser, it poses a cross-platform threat. Any browser application on any operating system that subscribes to these malicious notifications becomes part of the attackers’ network, providing them with a persistent communication channel.
Matrix Push C2 is marketed as a malware-as-a-service (MaaS) kit to other cybercriminals. It is sold directly through crimeware channels, typically via Telegram and cybercrime forums, under a tiered subscription model: approximately $150 for one month, $405 for three months, $765 for six months, and $1,500 for a full year.
Payments are accepted in cryptocurrency, and buyers communicate directly with the operator for access. Matrix Push was first observed at the beginning of October and has been active since then. There’s no evidence of older versions, earlier branding, or long-standing infrastructure, indicating this is a newly launched kit.
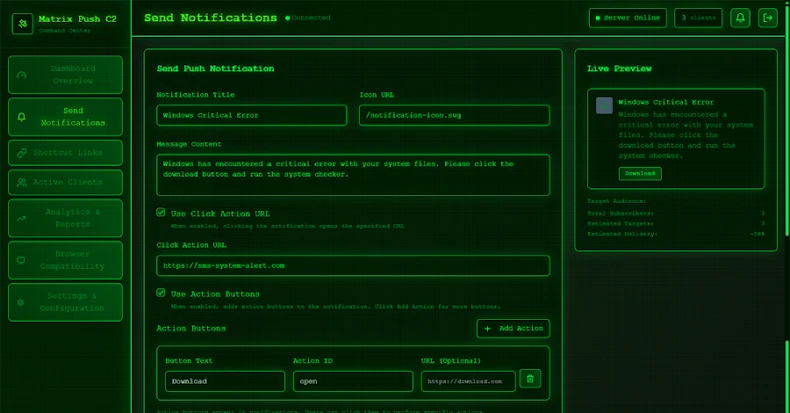
The tool is accessible via a web-based dashboard, enabling users to send notifications, monitor each victim in real-time, track interactions with notifications, create shortened links using an integrated URL shortening service, and even record installed browser extensions, including cryptocurrency wallets.
The core of the attack is social engineering, and Matrix Push C2 comes equipped with configurable templates to enhance the credibility of its fake messages. Attackers can easily customize their phishing notifications and landing pages to impersonate well-known companies and services.
Some of the supported notification verification templates are associated with prominent brands like MetaMask, Netflix, Cloudflare, PayPal, and TikTok. The platform also includes an Analytics & Reports section that allows its customers to measure the effectiveness of their campaigns and refine them as needed.
Matrix Push C2 signifies a shift in how attackers gain initial access and exploit users. Once a user’s endpoint (computer or mobile device) is under this kind of influence, the attacker can gradually escalate the attack.
They might deliver additional phishing messages to steal credentials, trick the user into installing more persistent malware, or even leverage browser exploits to gain deeper control of the system. Ultimately, the end goal is often to steal data or monetize the access, for example, by draining cryptocurrency wallets or exfiltrating personal information.