Phishing Attacks Evolve: How to Strengthen Your Defenses
In today’s digital landscape, phishing attacks have become increasingly sophisticated, often bypassing traditional security measures and posing significant threats to organizations and individuals alike. These deceptive tactics are designed to blend seamlessly into everyday communications, making them harder to detect and more effective in compromising sensitive information.
The Evolving Nature of Phishing Attacks
Phishing has transformed from rudimentary email scams to complex schemes that exploit human psychology and technological vulnerabilities. Modern phishing campaigns often employ the following techniques:
– Highly Convincing Spoofs: Attackers create emails and websites that closely mimic legitimate services, making it challenging for users to distinguish between genuine and fraudulent communications.
– Delayed Malicious Actions: Malicious behaviors are triggered only after user interaction, such as clicking a link or entering information, allowing initial security scans to pass without detection.
– QR Code Exploitation: Phishers embed malicious links within QR codes, which are less likely to be scrutinized by traditional security filters, thereby evading detection.
– Complex Redirect Chains: By using multiple redirects, attackers can obscure the final malicious destination, making it difficult for security systems to trace and block the threat.
– Rapid Domain Rotation: Frequent changes in domain names prevent blocklists from effectively keeping up, allowing phishing sites to remain active longer.
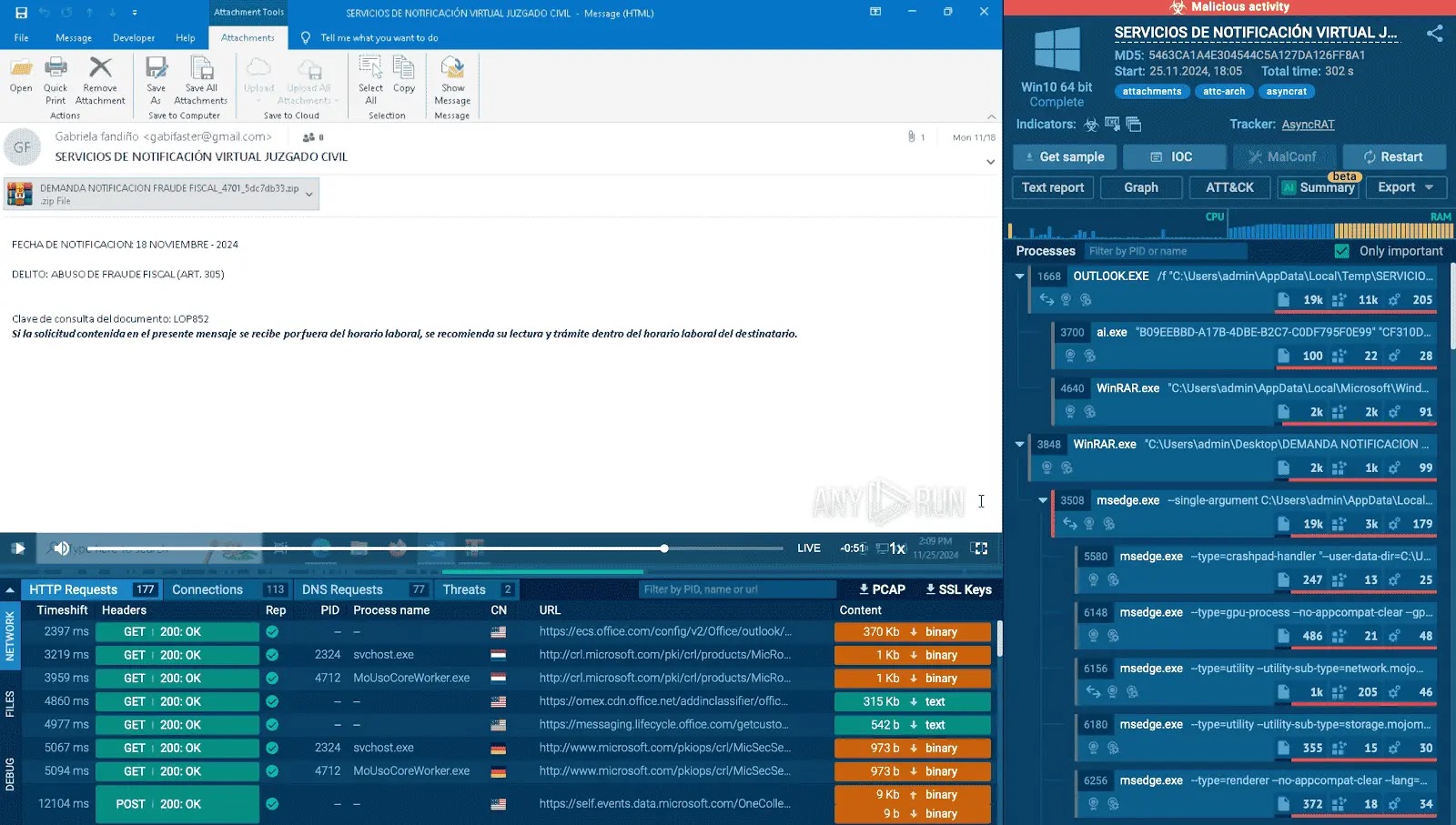
Case Study: PoisonSeed Phishing Kit
A notable example of advanced phishing tactics is the PoisonSeed phishing kit. This toolkit employs an adversary-in-the-middle (AitM) approach to intercept multi-factor authentication (MFA) tokens and session cookies. Victims receive spear-phishing emails that appear to be from legitimate bulk email or CRM providers, such as SendGrid and Mailchimp. These emails contain links that, when clicked, lead to fraudulent login prompts designed to harvest credentials. The PoisonSeed kit’s infrastructure is built upon React, featuring a modular design that includes fake Cloudflare Turnstile challenge pages and customized login forms. This sophisticated setup allows attackers to bypass MFA and gain unauthorized access to accounts. ([cybersecuritynews.com](https://cybersecuritynews.com/poisonseed-phishing-kit-bypasses-mfa/amp/?utm_source=openai))
The Limitations of Traditional Security Measures
Conventional security tools often fall short in detecting these advanced phishing techniques due to their reliance on static analysis and predefined signatures. Many security solutions assess the safety of a link or attachment based on its initial appearance, which can be deceiving. As phishing tactics evolve to delay malicious actions until after user interaction, these tools may fail to recognize and mitigate the threat in time.
Enhancing Detection with Interactive Sandboxing
To effectively combat modern phishing attacks, organizations should adopt advanced behavioral analysis tools, such as interactive sandboxes. These platforms simulate real user interactions, allowing security teams to observe the full execution of potentially malicious content in a controlled environment. By doing so, they can uncover hidden threats that traditional methods might miss.
For instance, interactive sandboxes can:
– Automate Routine Tasks: They can follow redirects, extract and open hidden links from QR codes, launch appropriate browsers, and solve CAPTCHA challenges automatically.
– Provide Analyst Control: Security professionals can pause the analysis, explore suspicious paths, click through pages, or trigger specific actions as needed, offering a comprehensive view of the attack chain.
This combination of automation and interactivity delivers full visibility into the entire phishing process, enabling organizations to detect and respond to threats more effectively.
Implementing Proactive Security Measures
Beyond adopting advanced detection tools, organizations should implement proactive security measures to mitigate the risk of phishing attacks:
– User Education and Awareness: Regular training sessions can help employees recognize phishing attempts and understand the importance of cautious online behavior.
– Email Filtering and Authentication: Deploying robust email filtering solutions and enforcing email authentication protocols (such as SPF, DKIM, and DMARC) can reduce the likelihood of phishing emails reaching users.
– Multi-Factor Authentication (MFA): While some phishing kits can bypass MFA, it remains a critical layer of security that can deter less sophisticated attacks.
– Regular Security Assessments: Conducting periodic security audits and penetration testing can identify vulnerabilities and ensure that security measures are up to date.
Conclusion
As phishing attacks continue to evolve in complexity and effectiveness, organizations must stay ahead by adopting advanced detection technologies and implementing comprehensive security strategies. By understanding the tactics used by attackers and leveraging tools like interactive sandboxes, security teams can gain the visibility needed to detect and neutralize threats before they cause harm.