EVALUSION Campaign: Unveiling the Amatera Stealer and NetSupport RAT Threat
In November 2025, cybersecurity experts identified a sophisticated malware campaign, dubbed EVALUSION, leveraging the ClickFix social engineering technique to disseminate the Amatera Stealer and NetSupport Remote Access Trojan (RAT). This campaign underscores the evolving tactics of cybercriminals in deploying advanced malware to compromise sensitive data.
Understanding the ClickFix Tactic
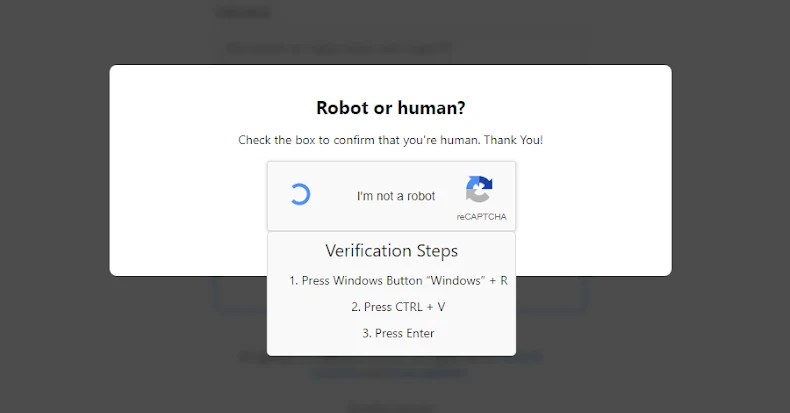
ClickFix is a deceptive strategy where users are misled into executing malicious commands under the guise of resolving non-existent technical issues or completing fake CAPTCHA verifications. This method has gained prominence due to its effectiveness in tricking users into initiating malware installations themselves.
The Amatera Stealer: An Evolution in Data Theft
First detected in June 2025, the Amatera Stealer is considered an advancement of the ACR (AcridRain) Stealer, which was previously available as a malware-as-a-service (MaaS) until its sales were halted in mid-July 2024. Amatera is marketed through subscription plans ranging from $199 per month to $1,499 annually.
Amatera is engineered to exfiltrate a wide array of data, targeting:
– Cryptocurrency wallets
– Web browsers
– Messaging applications
– FTP clients
– Email services
Notably, Amatera employs advanced evasion techniques, such as WoW64 SysCalls, to bypass user-mode hooking mechanisms commonly utilized by sandboxes, antivirus solutions, and Endpoint Detection and Response (EDR) products.
The Infection Chain: From Deception to Compromise
The EVALUSION campaign’s infection process is intricate and multi-staged:
1. Initial Deception: Users encounter phishing pages that prompt them to execute commands via the Windows Run dialog, purportedly to complete a reCAPTCHA verification.
2. Execution of Malicious Commands: The user-initiated command triggers the mshta.exe binary, which launches a PowerShell script. This script downloads a .NET payload from MediaFire, a file hosting service.
3. Payload Deployment: The downloaded payload is the Amatera Stealer DLL, obfuscated using PureCrypter—a C#-based multi-functional crypter and loader also offered as a MaaS by a threat actor known as PureCoder.
4. Process Injection and Data Harvesting: The Amatera DLL is injected into the MSBuild.exe process. Once active, it harvests sensitive data from the compromised system.
5. Secondary Payload Delivery: The stealer contacts an external server to execute a PowerShell command that fetches and runs the NetSupport RAT.
A distinctive aspect of this campaign is the conditional deployment of the NetSupport RAT. The PowerShell script checks if the victim’s machine is part of a domain or contains files of potential value, such as cryptocurrency wallets. If neither condition is met, the RAT is not downloaded, indicating a targeted approach to maximize the impact on valuable systems.
Broader Implications and Related Campaigns
The EVALUSION campaign is part of a broader trend where cybercriminals employ sophisticated social engineering tactics to distribute various malware families. Notable related campaigns include:
– Phishing Emails with Malicious Attachments: Emails containing Visual Basic Script attachments masquerading as invoices have been used to deliver XWorm through batch scripts that invoke PowerShell loaders.
– Compromised Websites with Malicious Redirects: Websites injected with malicious JavaScript redirect visitors to fake ClickFix pages mimicking Cloudflare Turnstile checks, leading to the deployment of NetSupport RAT.
– Fake Booking.com Pages: Users are presented with counterfeit CAPTCHA checks that employ ClickFix lures to execute malicious PowerShell commands, resulting in credential theft.
– Spoofed Internal Notifications: Emails impersonating internal email delivery notifications claim to have blocked important messages related to invoices or package deliveries, tricking recipients into clicking links that siphon login credentials.
– Advanced Phishing Kits: Tools like Cephas and Tycoon 2FA lead users to malicious login pages designed for credential theft.
Mitigation Strategies and Recommendations
To defend against such sophisticated threats, individuals and organizations should adopt comprehensive cybersecurity measures:
– User Education: Regular training sessions to recognize phishing attempts and social engineering tactics.
– Email Filtering: Implement advanced email filtering solutions to detect and block malicious attachments and links.
– Endpoint Protection: Deploy robust endpoint detection and response solutions capable of identifying and mitigating advanced malware.
– Regular Updates: Ensure all systems and software are up-to-date with the latest security patches.
– Network Monitoring: Continuously monitor network traffic for unusual activities that may indicate a compromise.
By staying vigilant and implementing these strategies, organizations can enhance their resilience against evolving cyber threats like the EVALUSION campaign.
Twitter Post:
Alert: The EVALUSION campaign uses ClickFix tactics to deploy Amatera Stealer & NetSupport RAT. Stay vigilant against phishing attacks! #CyberSecurity #MalwareAlert #ClickFix #AmateraStealer #NetSupportRAT
Focus Key Phrase:
EVALUSION campaign deploying Amatera Stealer and NetSupport RAT
Article X Post:
Hashtags:
Article Key Phrase:
Category: Security News