October 2025 Sees Surge in Sophisticated Phishing and Ransomware Attacks Exploiting Trusted Platforms
In October 2025, the cybersecurity landscape experienced a significant escalation in both phishing campaigns and ransomware attacks. Cybercriminals increasingly exploited reputable cloud services to infiltrate corporate systems, steal credentials, and disrupt critical infrastructure. This trend underscores the urgent need for organizations to adopt advanced behavioral detection mechanisms beyond traditional static indicators.
Exploitation of Legitimate Platforms in Phishing Campaigns
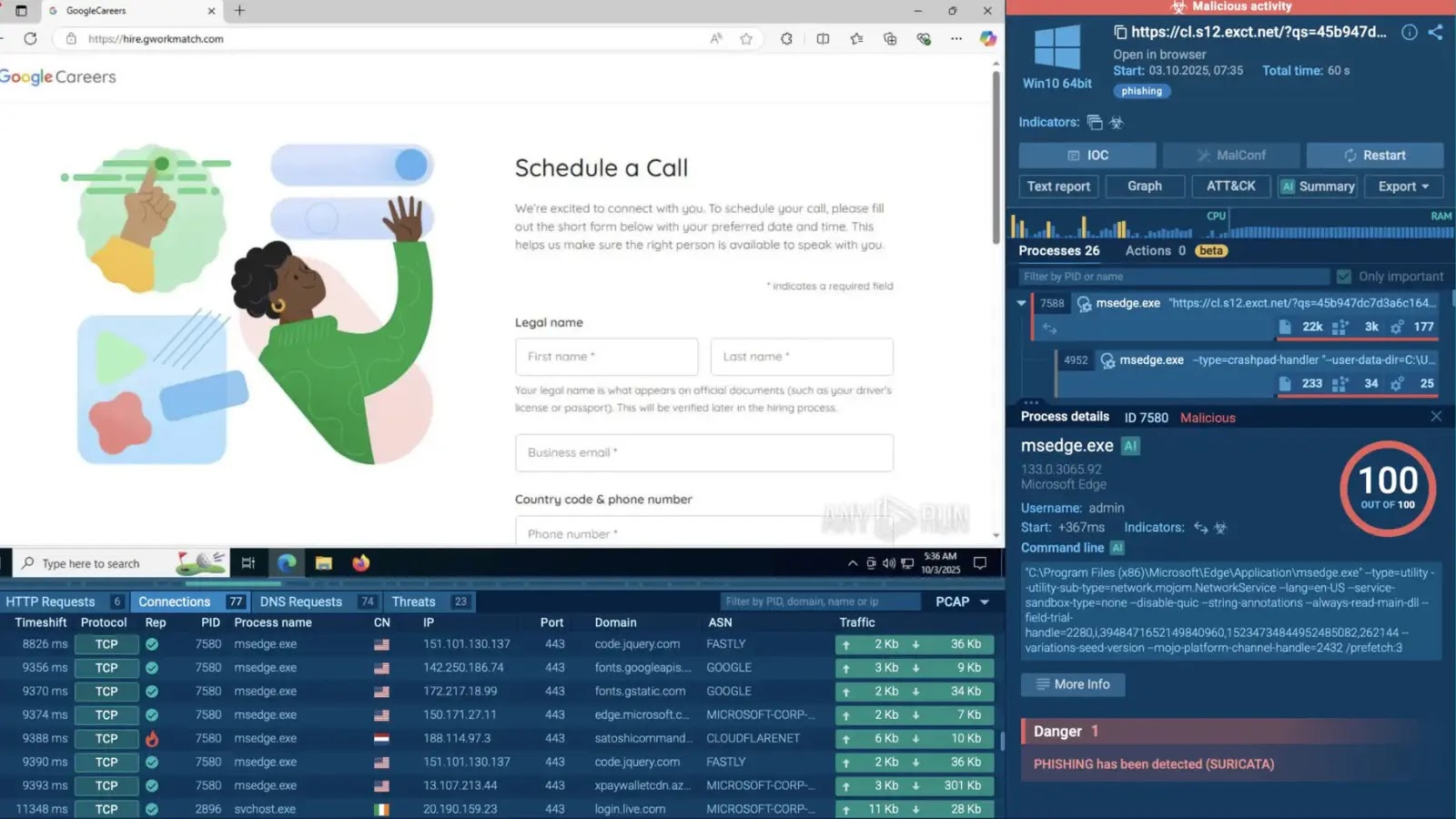
Phishing attacks during this period demonstrated heightened sophistication by leveraging trusted services to bypass conventional security filters. One notable campaign impersonated Google Careers, enticing victims with fraudulent job offers. The attack sequence involved:
1. Deceptive Emails: Victims received emails purporting to be from Google Careers, prompting them to apply for non-existent positions.
2. Redirects Through Trusted Services: The emails contained links that routed through Salesforce redirects and Cloudflare Turnstile CAPTCHAs, lending an air of legitimacy to the process.
3. Credential Harvesting: Ultimately, victims were directed to counterfeit login pages hosted on domains like satoshicommands.com, where their credentials were stolen.
This multi-layered attack primarily targeted the technology and consulting sectors, exploiting the inherent trust in well-known brands to facilitate account takeovers and data exfiltration.
Similarly, cybercriminals misused Figma’s public prototype feature to execute Microsoft-themed phishing schemes. Victims received shared document invites that led to fake login pages designed to capture credentials. Notably, groups like Storm-1747 were responsible for nearly half of these attacks, utilizing Figma’s trusted domain to embed interactive lures that evaded email security measures. Victims encountered CAPTCHAs and redirects to credential-stealing sites, often linked to operators such as Mamba.
ClickUp, another reputable platform, was exploited as a redirector in phishing campaigns. Attackers sent emails directing users to doc.clickup.com, which then redirected to Microsoft microdomains and Azure Blob Storage for final payload delivery. This method mimicked legitimate collaboration traffic, making it challenging for security systems to detect and resulting in widespread credential compromises.
Emergence of TyKit: A Reusable Phishing Kit
A significant development in October was the proliferation of TyKit, a reusable phishing kit first identified in May 2025 but reaching peak activity during this month. TyKit employed advanced techniques to evade detection:
– Obfuscated JavaScript in SVG Files: The kit concealed malicious code within SVG image files, using `eval` functions and Base64 encoding to redirect users to counterfeit Microsoft 365 login pages.
– Anti-Debugging Mechanisms: TyKit incorporated measures to thwart analysis, including staged command-and-control (C2) checks.
This campaign targeted sectors such as finance, government, and telecommunications across multiple regions, leading to numerous account thefts through adversary-in-the-middle (AitM) techniques.
LockBit 5.0: A Cross-Platform Ransomware Threat
On the ransomware front, LockBit 5.0 emerged as a formidable cross-platform threat, marking the group’s sixth anniversary by expanding its reach beyond Windows to include Linux and VMware ESXi systems. Key features of this variant include:
– Enhanced Obfuscation: The ransomware utilized advanced techniques such as DLL reflection and anti-analysis routines to evade detection.
– Rapid Encryption of Virtual Machines: By targeting hypervisors, LockBit 5.0 could encrypt multiple virtual machines simultaneously, disrupting entire data centers.
– Region-Based Restrictions and Service Terminations: The malware included functionalities to terminate specific services and apply region-based restrictions, complicating response efforts.
Attacks involving LockBit 5.0 affected enterprises across Europe, North America, and Asia, amplifying downtime and financial losses through shared infrastructure tactics.
Mitigation Strategies
To counter these evolving threats, organizations should implement the following measures:
– Advanced Behavioral Detection: Utilize sandbox environments to analyze SVG files and redirects, as static tools may miss these behaviors.
– Phishing-Resistant Multi-Factor Authentication (MFA): Implement MFA solutions that are resistant to phishing attempts to enhance account security.
– Monitoring for Suspicious Domains: Keep an eye out for domains like segy.zip or hire.gworkmatch.com, which have been associated with recent phishing campaigns.
– Integration of Threat Intelligence Feeds: Incorporate real-time threat intelligence to stay updated on emerging threats and attack vectors.
– Regular Backups and VPN-Enforced Access: Maintain up-to-date backups and enforce VPN access to critical systems to mitigate the impact of potential attacks.
– Behavioral Monitoring in Sandboxes: Employ sandbox environments to monitor for suspicious behaviors, turning isolated indicators into proactive defense rules.
As cybercriminals continue to refine their tactics by exploiting trusted platforms, it is imperative for organizations to rehearse incident response playbooks and stay vigilant against the next wave of sophisticated attacks.