Critical XWiki Vulnerability Under Active Exploitation: Immediate Action Required
A critical remote code execution (RCE) vulnerability in XWiki’s SolrSearch component is currently under active exploitation by cyber attackers. This flaw allows individuals with minimal guest privileges to execute arbitrary commands on affected systems, posing a significant threat to organizations utilizing this open-source enterprise wiki platform.
Understanding the Vulnerability
XWiki is a widely used open-source enterprise wiki that serves as an alternative to platforms like Confluence and MediaWiki. The identified vulnerability resides in the SolrSearch component and can be exploited by users with basic system access, including those with guest-level privileges. This accessibility makes the flaw particularly dangerous, as it requires minimal credentials to exploit.
Discovery and Exploitation Timeline
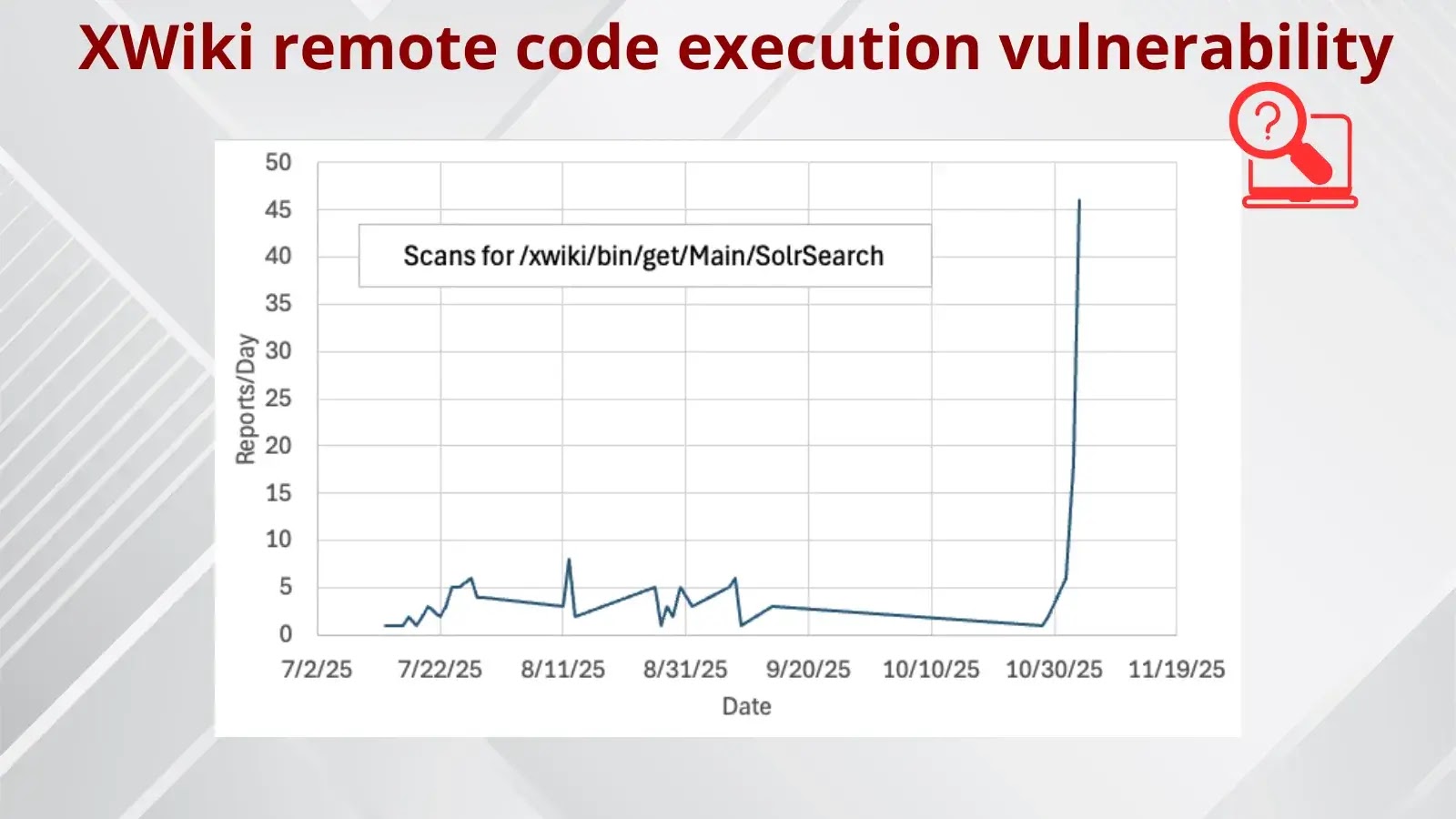
The vulnerability was initially disclosed in February, accompanied by a security advisory and an official patch from XWiki. Despite the availability of this information, the exploitation timeline exhibited an unusual delay. Initial reconnaissance scans were detected in July, but a significant increase in exploitation attempts has only been observed recently.
Exploitation Methodology
Attackers are leveraging this vulnerability by sending specially crafted GET requests to the vulnerable XWiki endpoint, specifically targeting the SolrSearch RSS media function. These malicious requests embed Groovy script commands within asynchronous execution blocks, enabling remote code execution through shell commands.
Captured exploit attempts have revealed that attackers are attempting to download and execute shell scripts from external servers, notably from the IP address 74.194.191.52. The User-Agent string in these requests includes the email address [email protected], which may be associated with the threat actor.
Potential Impact
The severity of this vulnerability lies in its potential to allow complete system compromise through remote code execution. Given that the attack requires no user interaction and is of low complexity, it is particularly attractive to threat actors conducting mass internet scanning campaigns.
Recommended Actions
Organizations utilizing XWiki should take the following immediate actions to mitigate the risk associated with this vulnerability:
1. Apply Security Patches: Ensure that all XWiki installations are updated with the security patch released in February.
2. Monitor for Suspicious Activity: Implement monitoring mechanisms to detect unusual SolrSearch requests that may indicate exploitation attempts.
3. Enhance Network Protections: Deploy network-level defenses to identify and block malicious traffic targeting this vulnerability.
By promptly addressing this vulnerability, organizations can significantly reduce the risk of unauthorized access and potential system compromise.