Critical RCE Vulnerability in React Native CLI Puts Developers at Risk
A critical remote code execution (RCE) vulnerability, identified as CVE-2025-11953, has been discovered in the @react-native-community/cli NPM package. This package, essential for React Native’s command-line interface, boasts nearly 2 million weekly downloads and is integral to developers building cross-platform mobile applications.
Understanding the Vulnerability
The vulnerability has been assigned a CVSS score of 9.8, indicating its severe nature due to its network accessibility, low complexity, and potential for significant damage. It allows unauthenticated attackers to execute arbitrary operating system commands on a developer’s machine through the package’s development server.
React Native’s CLI, separated from the core codebase for better maintainability, manages crucial tasks such as initializing projects and running the Metro bundler. Commands like `npm start` or `npx react-native run-android` initiate this server, which bundles JavaScript for emulators or devices.
Technical Breakdown
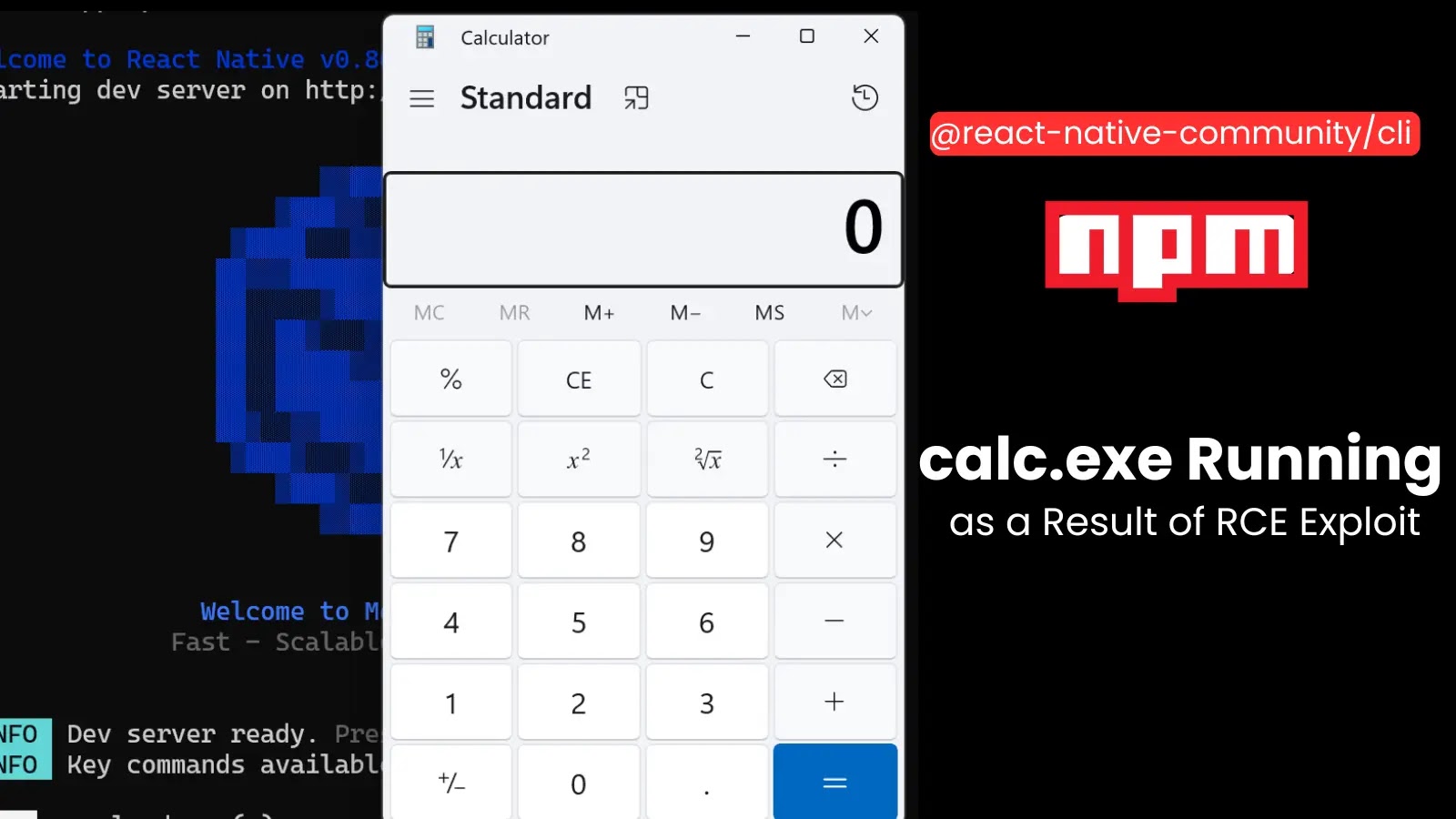
Researchers at JFrog identified that the server’s `/open-url` endpoint improperly handles user input, passing it directly to the open NPM library’s unsafe `open()` function. On Windows systems, this can lead to the execution of shell commands with full parameter control, such as launching applications like `calc.exe` or creating files like pwned.txt. While execution on macOS and Linux is more restricted, attackers could potentially escalate their actions by manipulating URI schemes or file handlers.
Exacerbating Factors
Compounding the issue is a secondary flaw in React Native’s core: the Metro server binds to all network interfaces (0.0.0.0) by default, despite console messages indicating it should only be accessible via localhost. This results from an undefined host parameter in the `runServer` function, exposing endpoints to remote attackers. Developers using vulnerable CLI versions (4.8.0 to 20.0.0-alpha.2) in the @react-native-community/cli-server-api package are particularly at risk, especially those not utilizing frameworks like Expo, which employ alternative servers.
Risk Assessment
The level of risk varies among developers. Projects that utilize Metro for hot reloading during development, common in standard React Native setups for Windows, macOS, iOS, or Android, are more susceptible. Global installations or bundled dependencies further amplify the threat. JFrog demonstrated that exploiting this vulnerability on Windows is straightforward, while Unix-like systems require more intricate methods, such as exploiting URI handlers for remote file execution.
Mitigation and Recommendations
Meta’s security team responded promptly by releasing a fix in CLI version 20.0.0. Developers are strongly advised to update their installations via npm, either within project folders or globally, and verify the update with the command `npm list @react-native-community/cli-server-api`.
For immediate protection, developers should bind the server to localhost by executing `npx react-native start –host 127.0.0.1`. This vulnerability highlights the dangers associated with third-party dependencies like the open package and the risks posed by default network exposures in development tools.