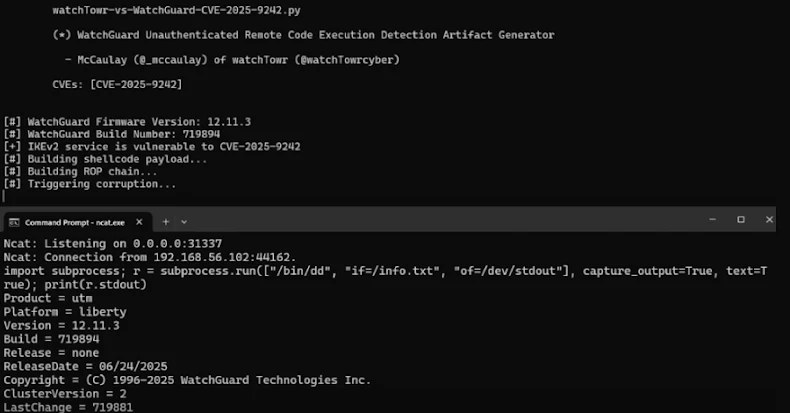
Cybersecurity experts have recently identified a significant security flaw in WatchGuard’s Fireware operating system, designated as CVE-2025-9242. This vulnerability, with a CVSS score of 9.3, poses a severe risk by allowing unauthenticated attackers to execute arbitrary code on affected devices.
Understanding the Vulnerability
The flaw is an out-of-bounds write issue located in the ‘iked’ process of Fireware OS. It impacts versions 11.10.2 through 11.12.4_Update1, 12.0 through 12.11.3, and 2025.1. Specifically, the vulnerability affects both mobile user VPNs utilizing IKEv2 and branch office VPNs configured with a dynamic gateway peer.
The root cause lies in the ‘ike2_ProcessPayload_CERT’ function within the ‘ike2_payload_cert.c’ file. This function copies client identification data to a local stack buffer of 520 bytes before validating the client’s SSL certificate. Due to the absence of a length check on the identification buffer, attackers can exploit this oversight to trigger a buffer overflow during the IKE_SA_AUTH phase of the VPN handshake, leading to remote code execution.
Potential Exploitation and Risks
Security researcher McCaulay Hudson from watchTowr Labs highlights that this vulnerability possesses characteristics attractive to ransomware groups:
– It affects internet-exposed services.
– Exploitation does not require authentication.
– It enables arbitrary code execution on perimeter devices.
Although Fireware OS lacks an interactive shell like ‘/bin/bash,’ attackers can manipulate the instruction pointer register to spawn a Python interactive shell over TCP. This is achieved by leveraging the ‘mprotect()’ system call, effectively bypassing no-execute (NX) bit protections.
Once a remote Python shell is established, attackers can escalate their access to a full Linux shell through the following steps:
1. Executing ‘execve’ within Python to remount the filesystem as read/write.
2. Downloading a BusyBox binary onto the target device.
3. Creating a symbolic link from ‘/bin/sh’ to the BusyBox binary.
Mitigation Measures
WatchGuard has addressed this vulnerability in the following Fireware OS versions:
– 2025.1: Fixed in 2025.1.1
– 12.x: Fixed in 12.11.4
– 12.3.1 (FIPS-certified release): Fixed in 12.3.1_Update3 (B722811)
– 12.5.x (T15 & T35 models): Fixed in 12.5.13
Users operating on version 11.x should note that this version has reached its end-of-life and is no longer supported.
Recommendations for Users
To safeguard against potential exploitation:
– Update Fireware OS: Ensure your device is running one of the patched versions listed above.
– Review VPN Configurations: Particularly if using IKEv2 with dynamic gateway peers, verify that configurations adhere to best security practices.
– Monitor Network Activity: Be vigilant for unusual or unauthorized access attempts, especially targeting VPN services.
– Implement Multi-Factor Authentication (MFA): Enhance security by requiring multiple forms of verification for access.
Broader Implications
This discovery underscores the critical importance of regular software updates and proactive vulnerability management. VPN services, often exposed to the internet, are prime targets for attackers. Organizations must prioritize the timely application of security patches to mitigate risks associated with such vulnerabilities.
Conclusion
The identification and remediation of CVE-2025-9242 highlight the ongoing challenges in cybersecurity. By staying informed and implementing recommended security measures, organizations can better protect their networks and sensitive data from potential threats.