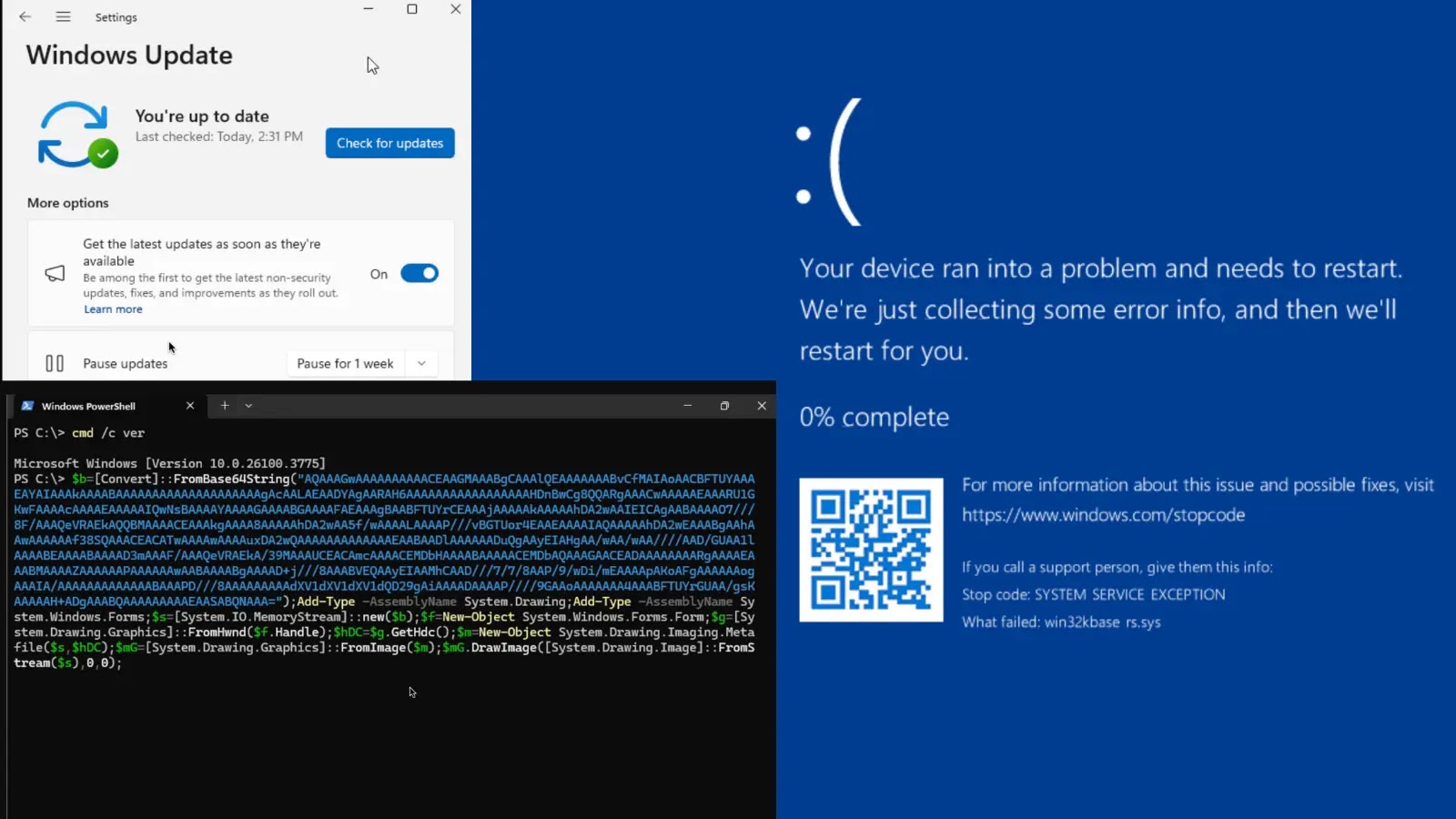
Microsoft’s recent integration of Rust into the Windows kernel, specifically within the Graphics Device Interface (GDI), has unveiled a significant vulnerability. This flaw can induce system-wide crashes, manifesting as the notorious Blue Screen of Death (BSOD), and underscores the complexities associated with incorporating memory-safe languages into critical operating system components.
Discovery and Analysis
The vulnerability was identified during a focused fuzzing campaign by Check Point researchers, who were examining Windows’ graphics subsystem for potential weaknesses. Fuzzing, a method that subjects software to a barrage of malformed inputs to uncover bugs, played a pivotal role in this discovery.
Utilizing tools like WinAFL and WinAFL Pet within a controlled testing environment, the researchers concentrated on the Enhanced Metafile Format (EMF) and EMF+ files. These compact structures guide GDI in rendering 2D graphics and are frequently embedded in documents or images, making them a longstanding vector for exploits due to their complexity.
Beginning with a mere 16 seed files, the fuzzers rapidly identified crashes ranging from information leaks to code execution risks in user-space components. However, the most significant breakthrough occurred unexpectedly: repeated system restarts following BugChecks indicated a kernel-level issue. This Denial of Fuzzing condition halted testing and necessitated a shift to kernel forensics.
Technical Breakdown of the Vulnerability
To pinpoint the root cause, Check Point enhanced their setup with memory dump analysis tools such as MemProcFS and Volatility, extracting mutated files from RAM disks. Through iterative refinement, they reduced reproduction time from several days to just 30 minutes across 836 samples.
A strategic modification to their testing harness allowed mutations to be streamed to a remote server via a custom C function and Python listener, capturing the exact 380,000th mutation that triggered the crash.
In-depth analysis revealed the bug resided in `win32kbase_rs.sys`, Microsoft’s Rust-rewritten driver for GDI regions. During the conversion of paths to regions in the `NtGdiSelectClipPath` function, an out-of-bounds array access in `region_from_path_mut()` invoked Rust’s `panic_bounds_check()`, resulting in a `SYSTEM_SERVICE_EXCEPTION`.
The specific trigger involved a malformed `EmfPlusDrawBeziers` record with mismatched point counts (17 points declared as 4) and anomalous coordinates, combined with a wide-stroke pen from an `EmfPlusObject`. This malformed geometry stressed edge block handling, bypassing bounds in the singly linked list representation.
A straightforward PowerShell proof-of-concept demonstrated the exploit’s accessibility: embedding the crafted metafile in a Graphics object via `System.Drawing` led to an immediate BSOD, even from low-privilege sessions on x86/x64 Windows 11 24H2 systems. While this vulnerability does not directly enable remote code execution, it poses a significant denial-of-service threat. For instance, an insider could script crashes across an enterprise, causing widespread disruption.
Microsoft’s Response and Mitigation
Microsoft addressed the flaw in OS Build 26100.4202 through the KB5058499 preview released on May 28, 2025. The update expanded the driver by 16KB, incorporating hardened logic. Key changes included the introduction of dual edge-handling routines—`add_edge_original()` and a bounds-checked `add_edge_new()`—controlled by a feature flag. The full rollout followed in June, although initial testing indicated the feature flag was disabled.
Check Point promptly reported the issue, but Microsoft’s Security Response Center (MSRC) classified it as a non-critical denial-of-service vulnerability, asserting that Rust’s panic mechanism functioned as intended.
Implications and Lessons Learned
This incident marks one of the first public Rust kernel bugs since its integration, which was promoted at BlueHat IL 2023 for enhancing security. While Rust mitigates certain vulnerabilities like buffer overflows, it does not eliminate design flaws or the consequences of incomplete testing.
As Windows continues to adopt memory-safe languages, such incidents serve as a reminder that language choice alone is not a panacea. Comprehensive fuzzing and validation remain essential to prevent scenarios where security mechanisms inadvertently cause system failures.