In the ever-evolving landscape of cybersecurity, even the most advanced operating systems can harbor vulnerabilities rooted in legacy configurations. A notable example is the WDigest authentication protocol in Windows 11 and Windows Server 2025, which, when enabled, can lead to the caching of plaintext passwords in system memory, thereby increasing the risk of credential theft.
Understanding WDigest Authentication
WDigest is an authentication protocol introduced in earlier versions of Windows to facilitate compatibility with applications requiring hashed credentials. However, this protocol has a significant drawback: it stores user credentials in plaintext within the system’s memory. Recognizing this security risk, Microsoft disabled WDigest by default starting with Windows 10 version 1703. Despite this precaution, the protocol remains present in the system and can be reactivated through specific registry modifications.
Reactivating WDigest: A Simple Yet Risky Process
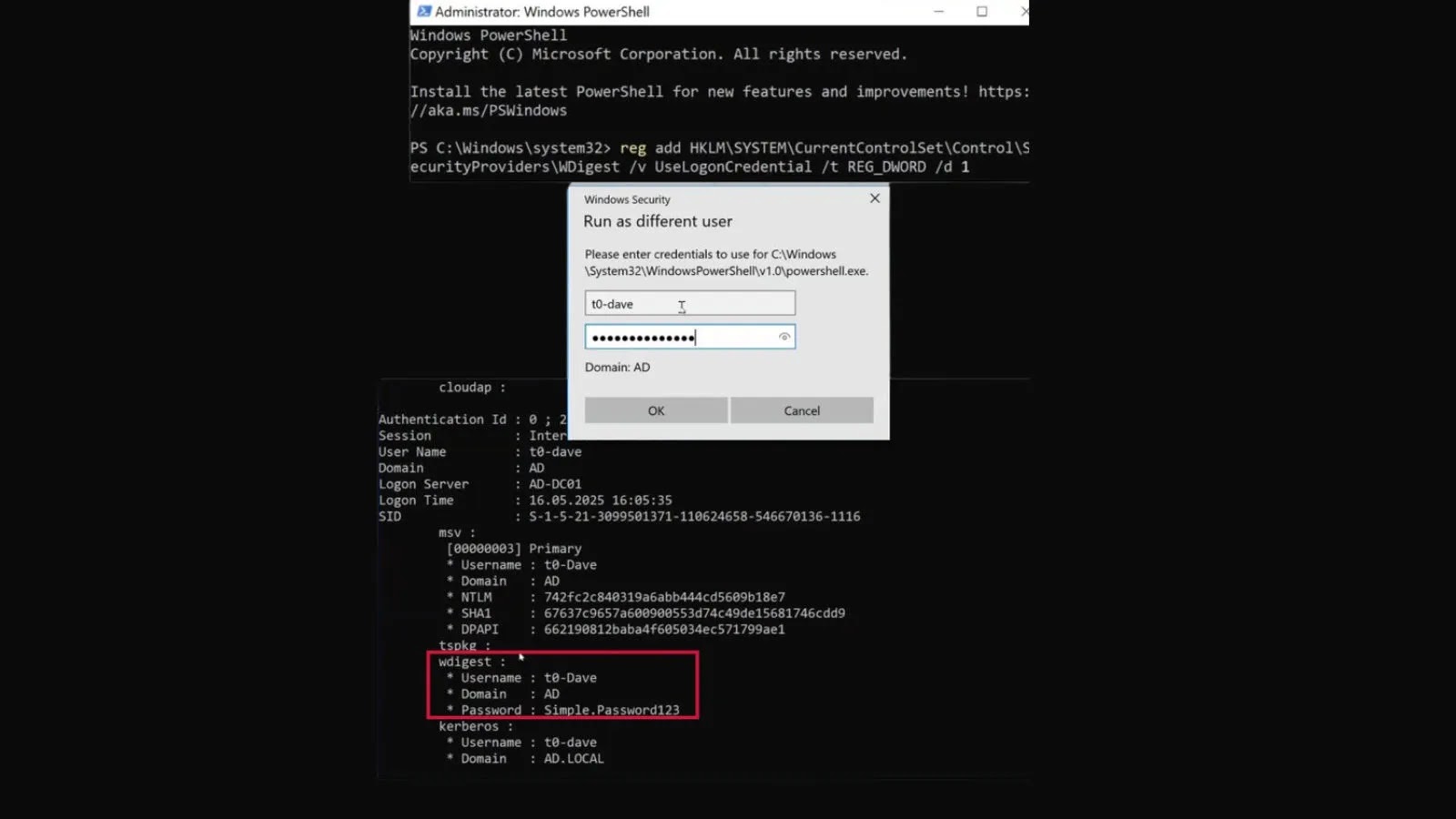
Re-enabling WDigest involves altering a registry key:
– Navigate to `HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest\UseLogonCredential`.
– Set the value to `1`.
This change takes effect immediately upon the next user logon without necessitating a system reboot. Once enabled, Windows begins storing unencrypted passwords in memory during user sessions.
The Implications of Plaintext Credential Caching
Storing plaintext credentials in memory poses a significant security threat. Malicious actors or malware with local access can exploit this vulnerability to extract sensitive information, facilitating unauthorized access and lateral movement within networks. Tools like Mimikatz have historically leveraged WDigest to retrieve credentials from memory, underscoring the protocol’s potential for misuse.
Mitigation Strategies
To safeguard systems against the risks associated with WDigest, consider the following measures:
1. Verify WDigest Status: Regularly inspect the registry key `HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest\UseLogonCredential` to ensure its value is set to `0`, indicating that WDigest is disabled.
2. Utilize the Protected Users Group: In Active Directory environments, adding high-privilege accounts to the Protected Users group can prevent the use of WDigest and other less secure authentication methods.
3. Implement Credential Guard: For organizations using Windows 11 Enterprise or Education editions, enabling Credential Guard can provide an additional layer of security by isolating the Local Security Authority Subsystem Service (LSASS) process, thereby protecting credentials from unauthorized access.
4. Monitor System Activity: Employ monitoring tools to detect unusual memory access patterns or unauthorized registry changes that could indicate attempts to enable WDigest or extract credentials.
Conclusion
While WDigest was designed to support legacy applications, its potential to compromise system security cannot be overlooked. Organizations and individual users must remain vigilant, ensuring that this protocol remains disabled unless absolutely necessary. By adopting proactive security measures and staying informed about potential vulnerabilities, users can better protect their systems against credential theft and unauthorized access.