Cybersecurity researchers have recently identified a previously unknown threat actor, designated as TA585, actively deploying a sophisticated malware known as MonsterV2 through targeted phishing campaigns. This discovery underscores the evolving tactics employed by cybercriminals to infiltrate systems and exfiltrate sensitive information.
TA585’s Unique Operational Approach
Unlike many cybercriminal groups that rely on external services for various stages of their attacks, TA585 distinguishes itself by maintaining complete control over its entire attack chain. This self-sufficiency encompasses infrastructure management, delivery mechanisms, and malware deployment. Such autonomy not only enhances the efficiency of their operations but also complicates efforts to trace and mitigate their activities.
Introduction to MonsterV2
First observed on criminal forums in February 2025, MonsterV2 is a versatile malware that functions as a Remote Access Trojan (RAT), information stealer, and loader. Also referred to as Aurotun Stealer—a misspelling of autorun—this malware has been previously disseminated via CastleLoader, also known as CastleBot.
Phishing Tactics and Infection Methods
TA585 employs a variety of sophisticated phishing techniques to distribute MonsterV2:
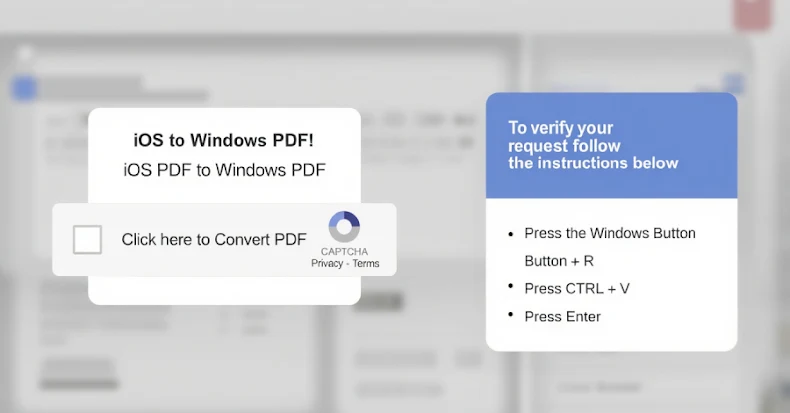
1. IRS-Themed Phishing Campaigns: Victims receive emails impersonating the U.S. Internal Revenue Service (IRS), prompting them to click on fraudulent links leading to PDFs. These documents direct users to web pages utilizing the ClickFix social engineering tactic, which persuades them to execute malicious commands via the Windows Run dialog or PowerShell terminal. This sequence culminates in the deployment of MonsterV2.
2. Malicious JavaScript Injections: In April 2025, TA585 began injecting malicious JavaScript into legitimate websites, presenting users with counterfeit CAPTCHA verifications. This method leverages the ClickFix tactic to initiate the infection process, ultimately delivering the malware through a PowerShell command.
3. Fake GitHub Security Notifications: Another strategy involves sending deceptive GitHub notifications that tag users in fabricated security alerts. These messages contain links to attacker-controlled websites designed to distribute MonsterV2.
Connections to Other Malicious Campaigns
Initial campaigns by TA585 distributed Lumma Stealer before transitioning to MonsterV2 in early 2025. Notably, the JavaScript injections and associated infrastructure, such as the domain intlspring[.]com, have also been linked to the dissemination of Rhadamanthys Stealer. Additionally, the tactics involving web injections and fake GitHub alerts are associated with CoreSecThree, a sophisticated framework active since February 2022, consistently used to propagate stealer malware.
Technical Capabilities of MonsterV2
MonsterV2 is a comprehensive malware suite with a range of functionalities:
– Data Theft: It can exfiltrate sensitive information from infected systems.
– Cryptocurrency Clipping: The malware acts as a clipper by replacing cryptocurrency addresses in the clipboard with those controlled by the attacker, redirecting funds during transactions.
– Remote Control: Utilizing Hidden Virtual Network Computing (HVNC), it allows attackers to remotely control infected machines.
– Command Execution: MonsterV2 can receive and execute commands from a command-and-control (C2) server, enabling various malicious activities.
– Payload Deployment: It has the capability to download and execute additional malicious payloads, such as StealC and Remcos RAT.
Commercialization and Evasion Techniques
The malware is marketed by a Russian-speaking actor, offering two subscription tiers:
– Standard Edition: Priced at $800 per month.
– Enterprise Edition: Available for $2,000 per month, this version includes additional features like stealer, loader, HVNC, and Chrome DevTools Protocol (CDP) support.
A notable characteristic of MonsterV2 is its deliberate avoidance of infecting systems in Commonwealth of Independent States (CIS) countries, indicating a strategic focus on targets outside this region.
To evade detection, MonsterV2 is typically packed using a C++ crypter called SonicCrypt. This method involves executing a series of anti-analysis checks before decrypting and loading the payload, thereby complicating efforts by security tools to identify and neutralize the malware.
Operational Workflow of MonsterV2
Upon execution, MonsterV2 follows a structured process:
1. Decryption and API Resolution: The malware decrypts and resolves essential Windows API functions required for its operations.
2. Privilege Escalation: It attempts to elevate its privileges to gain higher-level access within the system.
3. Configuration Decoding: MonsterV2 decodes an embedded configuration to establish a connection with its C2 server and determine subsequent actions based on predefined parameters:
– Anti-Debugging: If enabled, the malware detects and evades debugging tools.
– Anti-Sandboxing: When activated, it identifies and avoids sandbox environments.
– Persistence Mechanism: If set, the malware establishes persistence on the host system.
– Privilege Escalation: When configured, it attempts to elevate its privileges.
4. C2 Communication: After establishing contact with the C2 server, MonsterV2 transmits basic system information and geolocation data by querying api.ipify[.]org. The server’s response dictates the commands to be executed on the infected host, which may include:
– Information Theft: Executing infostealer functionality to exfiltrate data.
– Command Execution: Running arbitrary commands via cmd.exe or PowerShell.
– Process Management: Terminating, suspending, or resuming target processes.
– Remote Desktop Control: Establishing an HVNC connection to the infected system.
– Screen Capture: Taking screenshots of the desktop.
– Keylogging: Starting a keylogger to record keystrokes.
– File Manipulation: Enumerating, manipulating, copying, and exfiltrating files.
– System Shutdown: Shutting down or crashing the system.
– Payload Deployment: Downloading and executing additional payloads like StealC and Remcos RAT.
Conclusion
TA585 represents a significant evolution in cybercriminal operations, demonstrating a high degree of sophistication and self-reliance. By managing its entire attack chain and deploying versatile malware like MonsterV2, TA585 poses a formidable threat to organizations and individuals alike. This case highlights the critical need for robust cybersecurity measures, continuous monitoring, and user education to defend against such advanced threats.