A significant security flaw has been identified in the Sudo utility, a fundamental tool in Unix-like operating systems, following the public release of a proof-of-concept (PoC) exploit. This vulnerability, designated as CVE-2025-32463, specifically targets the chroot feature in Sudo versions 1.9.14 through 1.9.17, allowing local attackers to escalate their privileges to root with minimal effort.
Discovery and Technical Details
Security researcher Rich Mirch uncovered this flaw, which exploits the way Sudo handles user-specified root directories. By manipulating these directories, unauthorized users can execute commands with superuser privileges. The vulnerability has been assigned a critical CVSS score of 9.3, highlighting the severe risk it poses to systems relying on Sudo for privilege management.
The root cause of the vulnerability lies in Sudo’s improper path resolution when utilizing the –chroot option, introduced in version 1.9.14 to support user-defined root environments. In affected versions, an attacker can create a malicious /etc/nsswitch.conf file within a controlled directory. This manipulation tricks Sudo into loading an arbitrary shared library during command evaluation, effectively bypassing sudoers file restrictions and granting root privileges to users not explicitly authorized for escalation.
Mirch’s analysis of Sudo’s path resolution logic revealed that the chroot feature’s implementation introduces a vector for local privilege escalation. Notably, exploiting this flaw does not require network access or high-level privileges, making it particularly dangerous in multi-user environments such as servers and development machines. The Stratascale advisory emphasizes that this vulnerability could lead to full system compromise, including data exfiltration or malware deployment.
Proof of Concept Demonstration
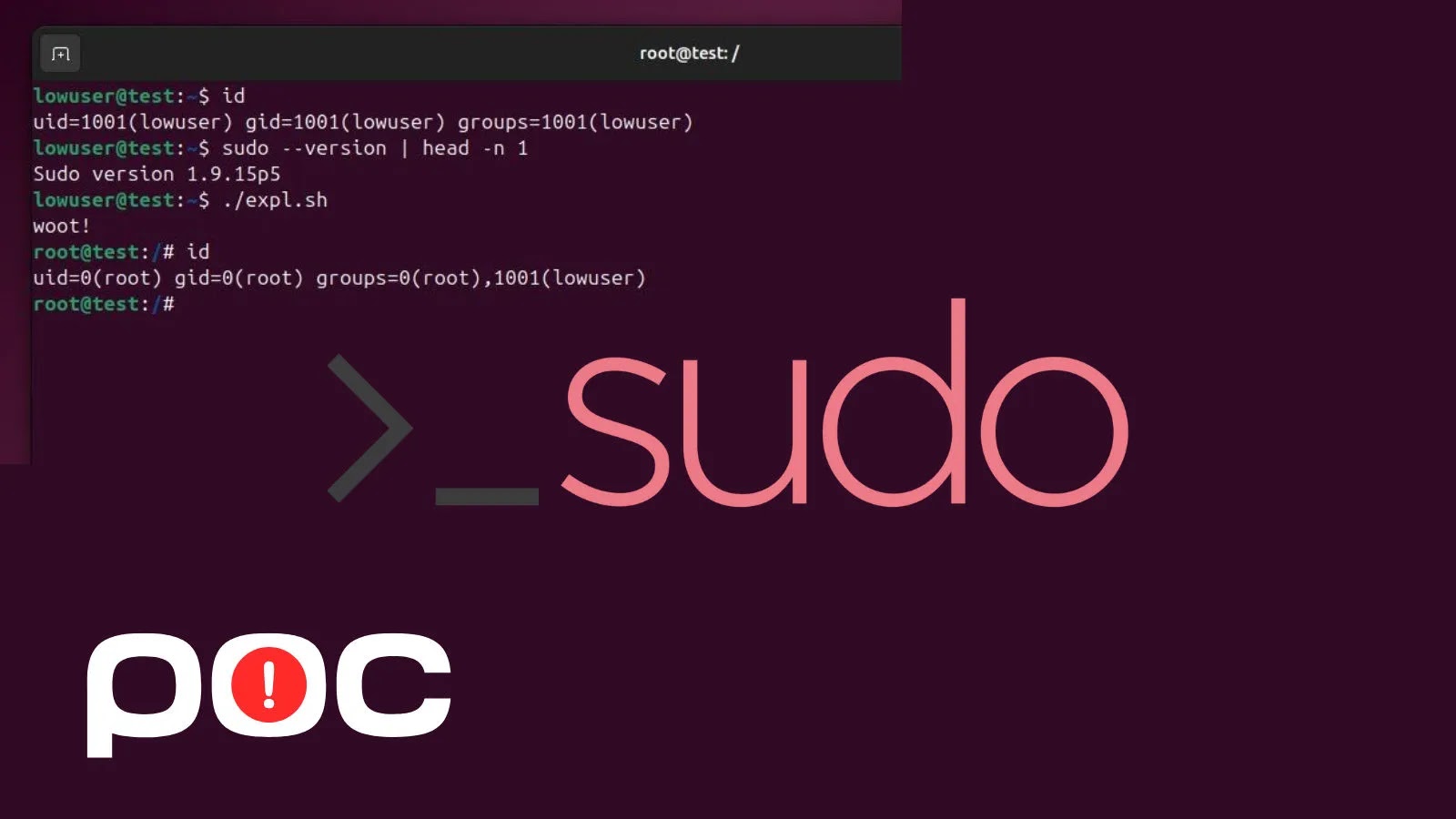
A GitHub repository maintained by researcher kh4sh3i provides a straightforward PoC exploit, demonstrating the privilege escalation in a controlled environment. The process involves cloning the repository, navigating to the directory, making the exploit.sh script executable, and running it after verifying the initial user ID.
The script leverages the chroot option to manipulate Sudo’s environment, resulting in successful privilege escalation, as evidenced by the post-execution ID output showing root access. Terminal screenshots in the repository illustrate the process: starting as a low-privilege user in the lowuser group, the exploit executes via sudo, changing the context to root@test with full administrative capabilities.
This visual proof confirms the vulnerability’s reliability on unpatched systems. While intended for educational use, the PoC underscores the need for caution, as unauthorized deployment constitutes illegal activity. Exploit-DB hosts a similar script, highlighting the ease with which malicious actors could adapt this exploit for nefarious purposes.
Impact and Affected Systems
Systems running vulnerable Sudo versions face severe risks, including complete takeover by local threat actors, which could facilitate lateral movement within breached networks. Affected products include major Linux distributions such as Ubuntu 24.04 LTS, 24.10, and 25.04; Red Hat Enterprise Linux variants; and Debian-based setups with Sudo versions 1.9.14 through 1.9.17.
Legacy versions prior to 1.9.14 remain unaffected due to the absence of chroot support. Immediate mitigation involves updating to Sudo version 1.9.17p1 or later, where the chroot feature is deprecated, and the path resolution flaw has been addressed. Administrators are advised to enable AppArmor or SELinux profiles to constrain Sudo operations and monitor logs for suspicious chroot invocations.
Official Responses and Recommendations
The Cybersecurity and Infrastructure Security Agency (CISA) has added this CVE to its Known Exploited Vulnerabilities catalog, mandating federal agencies to apply patches by October 2025. Organizations delaying updates risk heightened exposure, especially in cloud and containerized environments that rely on Sudo for automation.
In response to the vulnerability, Ubuntu and Red Hat have confirmed that their distributions are affected and have rolled out patches in recent updates. Administrators are urged to apply these patches promptly to mitigate the risk of exploitation.
Mitigation Steps
To protect systems from potential exploitation of CVE-2025-32463, administrators should take the following steps:
1. Update Sudo: Upgrade to Sudo version 1.9.17p1 or later, where the chroot feature is deprecated, and the path resolution flaw has been addressed.
2. Restrict Sudo Operations: Implement AppArmor or SELinux profiles to constrain Sudo operations, limiting the potential impact of any exploitation attempts.
3. Monitor System Logs: Regularly review logs for suspicious chroot invocations or other unusual Sudo activities that may indicate exploitation attempts.
4. Educate Users: Inform users about the risks associated with this vulnerability and the importance of adhering to security best practices to prevent exploitation.
Conclusion
The public release of a PoC exploit for CVE-2025-32463 underscores the critical need for prompt action to secure systems against potential attacks. By understanding the nature of this vulnerability and implementing the recommended mitigation steps, administrators can protect their systems from unauthorized privilege escalation and maintain the integrity of their environments.