A newly developed tool named IAmAntimalware has surfaced, capable of injecting malicious code directly into antivirus software processes. This tool, released on October 11, 2025, by developer Two Seven One Three on GitHub, exploits Windows service cloning and digital signature manipulation to bypass antivirus self-protection mechanisms. The cybersecurity community is alarmed by this development, as it could enable stealthy persistence on compromised systems during penetration testing or malicious campaigns.
Understanding IAmAntimalware
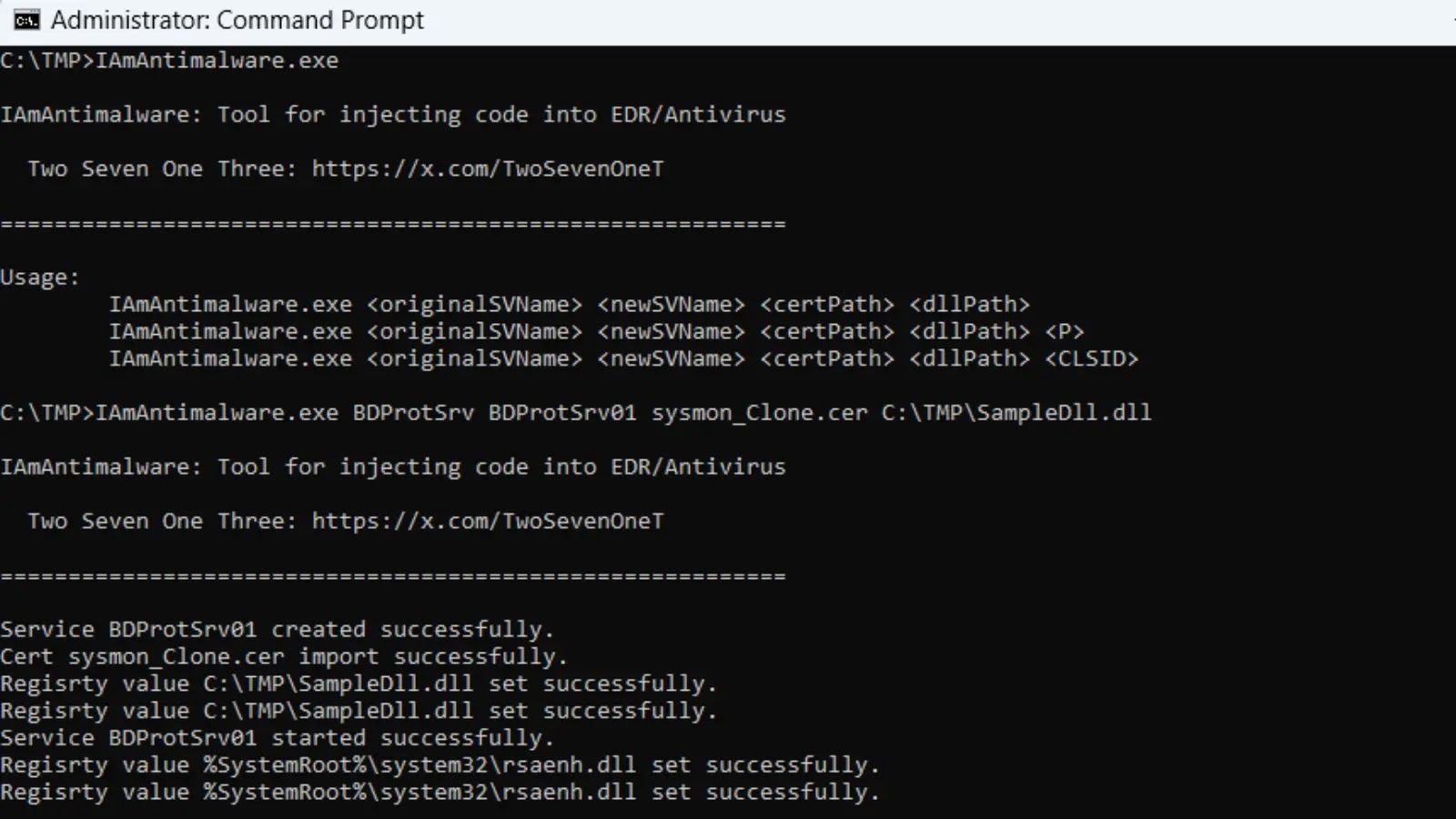
IAmAntimalware operates by cloning legitimate antivirus services, such as those from Bitdefender or Avast, to create identical processes that inherit elevated privileges without triggering alarms. The tool modifies the Windows Cryptography API registry under HKLM\SOFTWARE\Microsoft\Cryptography\Defaults\Provider to hijack the cryptographic provider, loading a user-controlled DLL in place of trusted modules.
Users provide parameters like the original service name, new cloned name, certificate path for signature cloning, and absolute DLL path; an optional “P” flag enables Protected Process Light (PPL) support for enhanced evasion. For scenarios avoiding cryptographic hijacking, the tool supports COM object CLSID manipulation, requiring TrustedInstaller privileges to spoof component loading.
Signature cloning relies on a companion tool, CertClone, which duplicates valid Windows certificates like those from Sysmon, ensuring the injected DLL appears legitimate to integrity checks. This multi-layered approach circumvents common antivirus safeguards, including process introspection, elevated privilege monitoring, and code signing verification, allowing injected code to write files or execute commands in protected directories.
Demonstrated Effectiveness
In demonstrations detailed by the creator, IAmAntimalware successfully injected a sample DLL into Bitdefender’s BDProtSrv process, enabling the creation of unauthorized files in the antivirus installation folder, a feat impossible for standard user processes. Similar tests on Trend Micro and Avast confirmed effectiveness, though Avast required a GUI process targeting stability.
The injected code, such as a simple backdoor writing a marker file, evades detection by operating within whitelisted, unkillable processes that antivirus developers hesitate to terminate to avoid system instability.
Potential Implications
Early reports indicate no widespread exploitation yet, but the tool’s open-source nature and simplicity, written entirely in C++, could accelerate adoption in red team exercises or by threat actors. Security analysts rate the technique medium severity due to its reliance on system access and lack of zero-day exploits, yet it underscores vulnerabilities in antivirus trust models.
This tool highlights a critical irony: antivirus processes, granted SYSTEM-level privileges for threat hunting, become prime targets for subversion. By injecting into these exceptions to normal security rules, attackers can disable alerts, exfiltrate data, or maintain persistence undetected, complicating incident response.
Mitigation Strategies
Mitigation strategies include monitoring unusual module loads in antivirus processes, enforcing strict certificate trust policies, and leveraging PPL more rigorously to isolate critical services. Experts urge organizations to validate antivirus integrity regularly and consider endpoint detection tools with behavioral analytics beyond signature-based checks.
As the tool gains traction, evidenced by Reddit discussions and YouTube demos, vendors like Microsoft and antivirus providers face pressure to patch service cloning vectors. While intended for ethical pentesting, IAmAntimalware exemplifies how defensive tools can be weaponized, demanding vigilant updates in an evolving threat landscape.