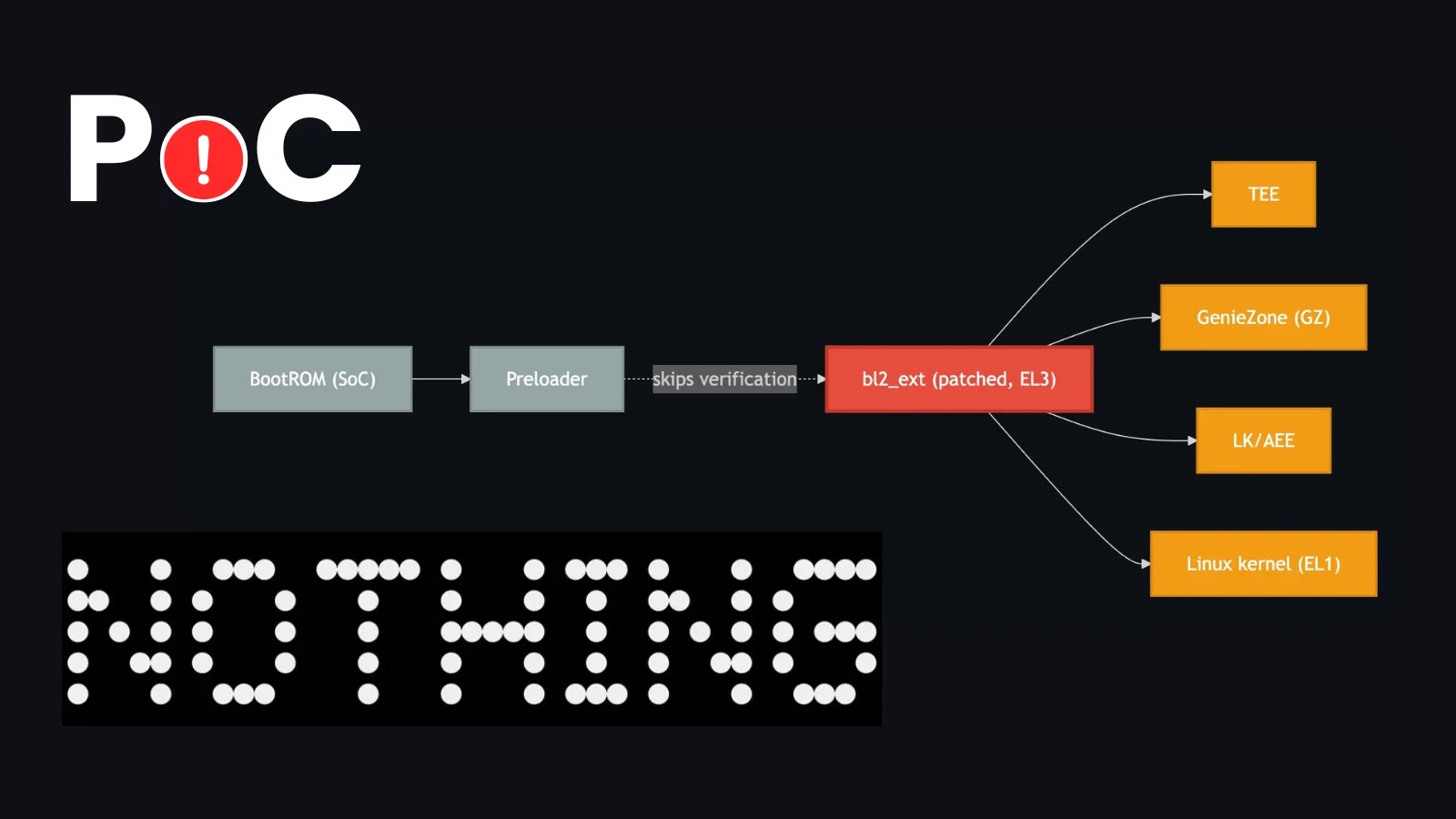
A recently disclosed proof-of-concept (PoC) exploit, named Fenrir, has unveiled a critical vulnerability within the secure boot process of the Nothing Phone (2a) and CMF Phone 1. This flaw potentially extends to other devices utilizing MediaTek systems-on-a-chip (SoCs). The exploit enables arbitrary code execution at Exception Level 3 (EL3), the highest privilege level in ARM architecture, effectively compromising the device’s secure boot mechanism.
Understanding the Vulnerability
The root of this vulnerability lies in a logical flaw within MediaTek’s boot chain. Specifically, when a device’s bootloader is unlocked (with `seccfg` set to unlocked), the Preloader stage fails to verify the cryptographic signature of the `bl2_ext` partition. This oversight is significant because `bl2_ext` is responsible for authenticating all subsequent components in the boot sequence.
During the boot process, the Preloader transfers execution to `bl2_ext` while still operating at EL3. This transfer without proper verification allows an attacker to modify `bl2_ext` to bypass all further signature checks. Consequently, this leads to a complete breakdown of the chain of trust, permitting the loading of unverified and potentially malicious code.
Implications of the Exploit
By leveraging this flaw, an attacker can achieve code execution at EL3, granting deep control over the device before the main operating system loads. The PoC exploit demonstrates this by altering the `sec_get_vfy_policy()` function to always return a value of 0. This manipulation tricks the bootloader into believing that all subsequent images are verified, effectively bypassing security measures.
The released exploit includes a payload capable of:
– Registering custom fastboot commands.
– Controlling the device’s boot mode.
– Dynamically calling native bootloader functions.
Additionally, the PoC can spoof the device’s lock state, making it appear as locked to pass integrity checks, even when the bootloader is unlocked. However, the researcher notes that the current payload cannot modify memory at runtime due to Memory Management Unit (MMU) faults. Despite this limitation, the exploit provides a robust foundation for further development.
Affected Devices and Mitigation
The exploit has been confirmed to work on the Nothing Phone (2a), codenamed Pacman, and the CMF Phone 1, codenamed Tetris. Furthermore, the developer of the exploit indicates that the Vivo X80 Pro is affected by a similar, potentially more severe, vulnerability where `bl2_ext` is not verified even with a locked bootloader. This issue is believed to be present in other MediaTek devices that use lk2 as their secondary bootloader.
The researcher has issued a strong warning: any attempt to use the exploit can permanently damage or brick a device if not performed correctly. Users are advised to exercise extreme caution, as the process involves flashing a modified bootloader image that can lead to irreversible hardware failure.
Technical Breakdown of the Exploit
The Fenrir exploit targets a critical flaw in the MediaTek boot chain, specifically within the Preloader stage. When the bootloader is unlocked, the Preloader neglects to verify the cryptographic signature of the `bl2_ext` partition. This partition is crucial as it verifies all subsequent components in the boot chain. By exploiting this oversight, an attacker can modify `bl2_ext` to bypass all further signature checks, leading to a total collapse of the chain of trust.
The exploit operates by patching the `sec_get_vfy_policy()` function within `bl2_ext` to always return 0. This alteration deceives the bootloader into accepting all subsequent images as verified, regardless of their authenticity. The payload included in the exploit allows for:
– Registration of custom fastboot commands, enabling attackers to execute arbitrary commands during the boot process.
– Control over the device’s boot mode, allowing attackers to dictate how the device boots.
– Dynamic invocation of native bootloader functions, providing deep control over the device’s boot process.
Additionally, the exploit can spoof the device’s lock state, making it appear locked even when the bootloader is unlocked. This capability can deceive security mechanisms that rely on the bootloader’s lock state to enforce security policies.
Potential Risks and Recommendations
The ability to execute code at EL3 poses significant risks, including:
– Installation of persistent malware that is difficult to detect and remove.
– Extraction of sensitive data from the device.
– Bypassing of security mechanisms implemented at the operating system level.
Given the severity of this vulnerability, it is imperative for users of affected devices to:
– Avoid unlocking the bootloader unless absolutely necessary.
– Refrain from flashing unverified or modified bootloader images.
– Regularly check for firmware updates from the device manufacturer that may address this vulnerability.
Manufacturers are urged to:
– Review and update the boot chain verification processes to ensure all components are properly authenticated, even when the bootloader is unlocked.
– Provide clear guidance to users regarding the risks associated with unlocking the bootloader and flashing custom firmware.
– Release firmware updates to patch this vulnerability and prevent exploitation.
Conclusion
The disclosure of the Fenrir exploit highlights a critical vulnerability in the secure boot process of certain devices using MediaTek SoCs. The ability to execute code at the highest privilege level poses significant security risks. Users and manufacturers must take immediate action to mitigate these risks by adhering to best practices and applying necessary updates. As the landscape of mobile device security continues to evolve, vigilance and proactive measures remain essential in safeguarding against emerging threats.