Cybersecurity researchers have identified a malicious campaign targeting WordPress websites, injecting harmful JavaScript to redirect visitors to deceptive sites. This tactic leverages the ClickFix social engineering method, which deceives users into downloading malware by presenting fake browser verification challenges.
Sucuri, a website security firm, initiated an investigation after a client’s WordPress site began serving suspicious third-party JavaScript to its visitors. The attackers had modified the site’s “functions.php” file—a core theme component—by embedding code that referenced Google Ads. This was likely an attempt to evade detection. However, the code’s true purpose was to act as a remote loader, sending HTTP POST requests to the domain “brazilc[.]com.” This domain responded with a dynamic payload comprising two main components:
1. A JavaScript file hosted on “porsasystem[.]com,” designed to execute site redirects.
2. A JavaScript snippet that creates a hidden 1×1 pixel iframe, injecting code that mimics legitimate Cloudflare assets, such as “cdn-cgi/challenge-platform/scripts/jsd/main.js.” This API is integral to Cloudflare’s bot detection and challenge platform.
The domain “porsasystem[.]com” has been flagged as part of a traffic distribution system (TDS) known as Kongtuke (also referred to as 404 TDS, Chaya_002, LandUpdate808, and TAG-124). This system is utilized to distribute malicious content across various platforms.
The infection chain typically begins when users visit a compromised site, triggering the execution of “porsasystem[.]com/6m9x.js.” This script subsequently calls “porsasystem[.]com/js.php,” ultimately leading victims to ClickFix-style pages designed for malware distribution.
These findings underscore the critical importance of securing WordPress sites. Website administrators are advised to:
– Regularly update plugins, themes, and core website software to their latest versions.
– Implement strong, unique passwords for all administrative accounts.
– Conduct routine scans to detect anomalies, such as unexpected administrator accounts, which may indicate unauthorized access.
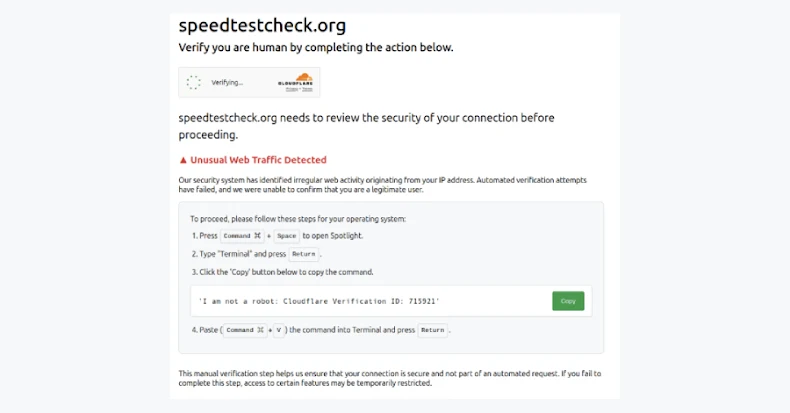
In a related development, Palo Alto Networks’ Unit 42 has detailed a phishing kit named IUAM ClickFix Generator. This tool enables attackers to create highly customizable phishing pages that mimic browser verification challenges commonly used by Content Delivery Networks (CDNs) and cloud security providers to defend against automated threats. The spoofed interface is designed to appear legitimate to victims, increasing the effectiveness of the lure.
The phishing pages generated by this kit possess capabilities to manipulate the clipboard—a crucial step in the ClickFix attack—and detect the operating system in use. This allows the attackers to tailor the infection sequence and serve compatible malware.
In at least two documented cases, threat actors have utilized pages created with this kit to deploy information stealers such as DeerStealer. These incidents highlight the evolving nature of phishing attacks and the need for heightened vigilance among internet users.
To mitigate the risks associated with such attacks, users are encouraged to:
– Be cautious when encountering unexpected browser verification prompts, especially on unfamiliar websites.
– Keep their operating systems and software up to date to protect against known vulnerabilities.
– Utilize reputable security software to detect and prevent malware infections.
By adopting these proactive measures, both website administrators and users can enhance their defenses against the sophisticated tactics employed by cybercriminals in the current digital landscape.