In the realm of digital forensics and incident response (DFIR), the ability to detect and analyze malicious activities on Windows systems is paramount. A critical component in this process is the AmCache, a registry hive that records metadata about executed applications and drivers. Recognizing the importance of this data, Kaspersky researchers have developed AmCache-EvilHunter, an open-source tool designed to streamline the parsing and analysis of AmCache data, thereby enhancing threat detection and response capabilities.
Understanding AmCache
AmCache is a registry hive located at `C:\Windows\AppCompat\Programs\Amcache.hve` on Windows systems. It serves as a repository for metadata concerning executed applications and drivers, including file paths, publisher information, timestamps, binary types (32-bit or 64-bit), and SHA-1 hashes. This data is invaluable for DFIR professionals, as it provides a historical record of software execution, aiding in the identification of both benign and malicious activities.
One of the key advantages of AmCache is its resilience. Even if malware attempts to delete itself to evade detection, the execution records remain intact within AmCache. This persistence makes AmCache an essential resource for incident responders seeking to reconstruct execution timelines and identify indicators of compromise (IOCs).
Introducing AmCache-EvilHunter
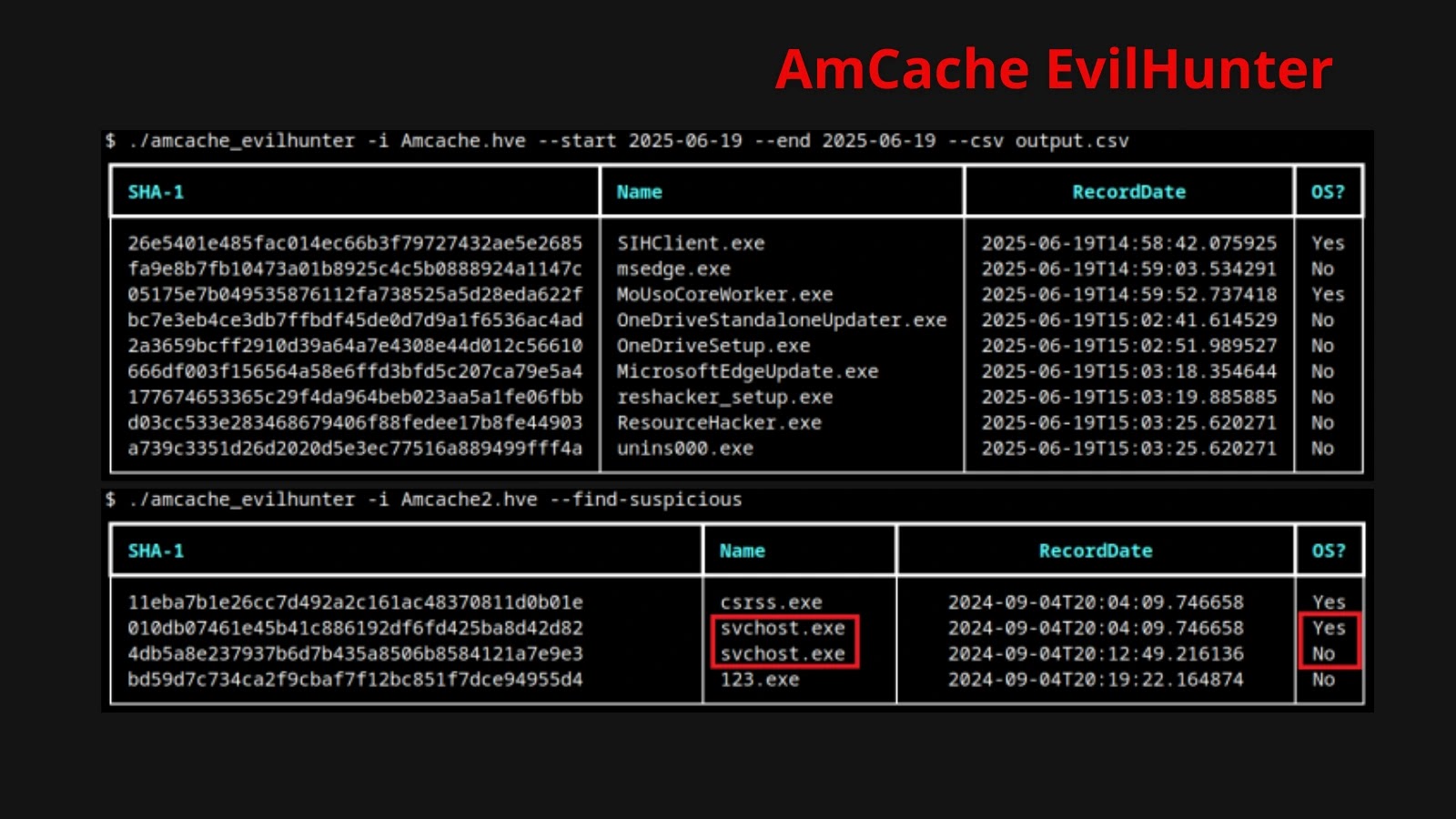
AmCache-EvilHunter is a command-line utility written in Python, developed to automate the parsing and analysis of the AmCache.hve registry hive. By extracting and processing key metadata entries, the tool simplifies the identification of suspicious activities and accelerates the threat detection process.
Key Features of AmCache-EvilHunter
1. Comprehensive Metadata Extraction: The tool parses critical registry keys such as `InventoryApplicationFile`, `InventoryDriverBinary`, `InventoryApplication`, and `InventoryApplicationShortcut`. This extraction reveals detailed information, including file paths, publisher data, LinkDate timestamps, binary types, and SHA-1 hashes.
2. Advanced Filtering Options: AmCache-EvilHunter offers several filtering capabilities to enhance analysis efficiency:
– Date Range Filtering: Users can specify a date range to focus on records within a particular timeframe. For example, to extract executables present between September 1 and September 30, 2025, the following command can be used:
“`
python amcache-evilhunter.py –input Amcache.hve –output results.csv –start-date 2025-09-01 –end-date 2025-09-30
“`
– Suspicious File Identification: The `–find-suspicious` flag applies heuristics to highlight anomalous entries, such as files with one-letter names (e.g., `1.exe`), random hexadecimal filenames, and common typo variants like `scvhost.exe`.
– Publisher Information Filtering: The `–missing-publisher` flag filters out entries lacking publisher information, which can be indicative of unsigned or potentially malicious files.
– Operating System Component Exclusion: The `–exclude-os` flag omits known operating system components from the analysis, reducing noise and focusing on non-system binaries.
3. Integrated Threat Intelligence Lookups: For each identified SHA-1 hash, users can perform automated lookups against threat intelligence platforms such as VirusTotal and Kaspersky OpenTIP. This integration appends detection counts and threat classification tags to the output, providing immediate insights into the potential maliciousness of the files.
4. Keyword and Program ID Search: Analysts can search for specific keywords or ProgramId values using the `–search` flag. For instance, to confirm the presence of a tool like WinSCP, the following command can be used:
“`
python amcache-evilhunter.py –input Amcache.hve –search winscp.exe
“`
Technical Implementation
AmCache-EvilHunter utilizes the Registry Python library to load and parse the REGF-formatted AmCache hive. It iterates through subkeys and values to extract relevant metadata, which is then processed according to the specified filters and options. The tool’s modular architecture allows for easy extension, enabling developers to integrate support for custom IOC feeds or incorporate it into Security Orchestration, Automation, and Response (SOAR) platforms.
Binaries and scripts for AmCache-EvilHunter are available on GitHub, supporting both Windows and Linux deployments.
Enhancing DFIR Workflows
By automating the parsing, filtering, and threat intelligence lookups of AmCache data, AmCache-EvilHunter significantly reduces manual effort in DFIR workflows. Incident responders can rapidly reconstruct execution timelines, identify stealthy rootkits via `InventoryDriverBinary` entries, and generate robust IOCs from `InventoryApplicationFile` records. As adversaries increasingly employ self-erasing malware to evade detection, tools like AmCache-EvilHunter ensure that crucial execution evidence is preserved and accessible.
Conclusion
The introduction of AmCache-EvilHunter marks a significant advancement in the field of digital forensics and incident response. By providing an efficient and automated means to parse and analyze AmCache data, the tool empowers security professionals to detect and respond to malicious activities on Windows systems more effectively. Its integration with threat intelligence platforms and advanced filtering options make it a valuable asset in the ongoing effort to enhance cybersecurity defenses.