In a recent wave of cyberattacks, threat actors are exploiting the trust users place in widely-used collaboration tools by distributing weaponized versions of Microsoft Teams. This sophisticated campaign aims to deceive individuals into downloading malicious installers, thereby granting attackers unauthorized remote access to their systems.
Tactics Employed by Cybercriminals
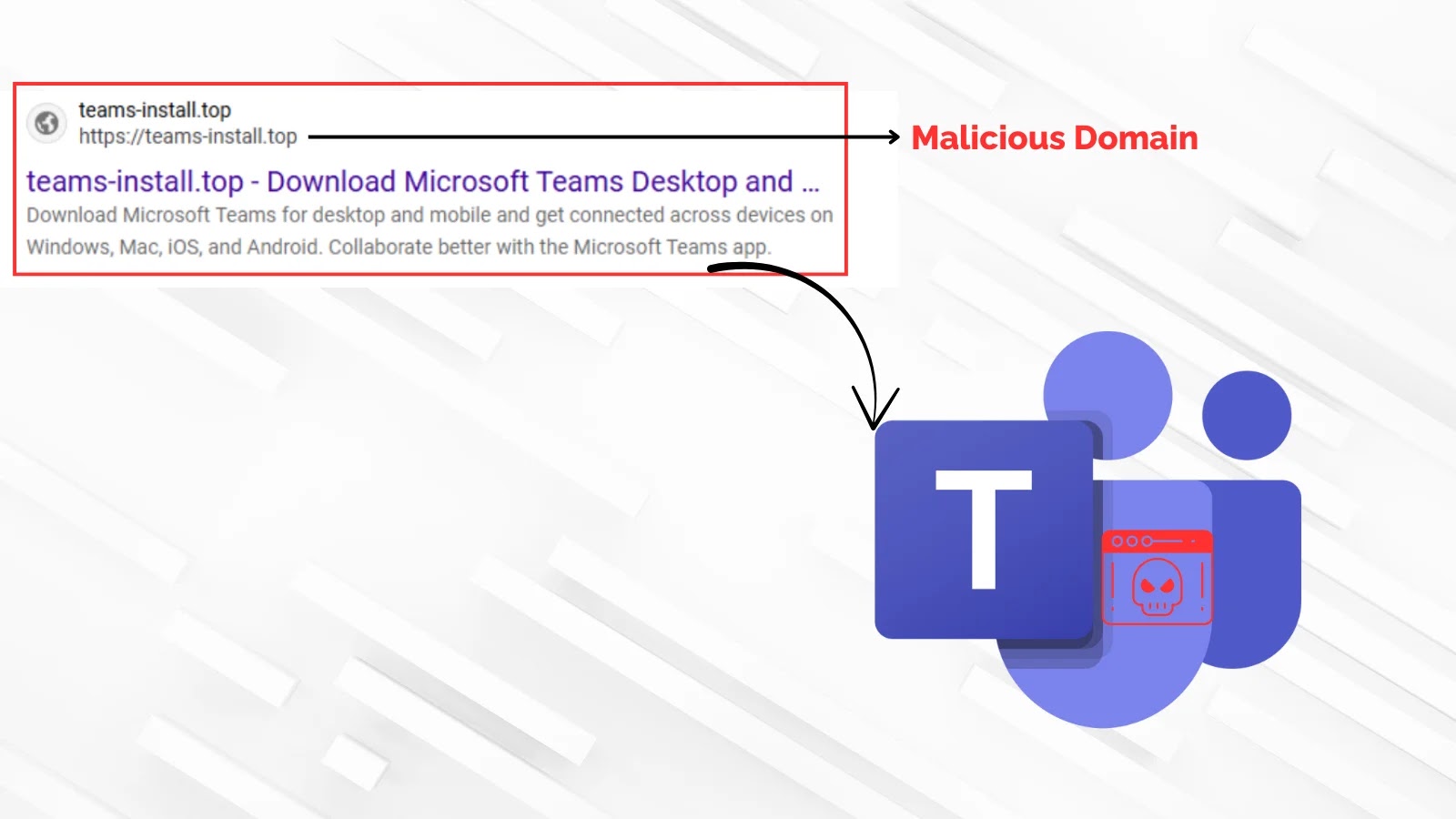
The attackers employ a combination of search engine optimization (SEO) poisoning and malicious advertisements to lure unsuspecting users. When individuals search for terms like Microsoft Teams download, they are presented with deceptive ads that redirect them to counterfeit websites designed to mimic Microsoft’s official download pages. One such fraudulent domain, `teams-install[.]top`, has been identified offering a malicious file named `MSTeamsSetup.exe`.
To enhance the illusion of legitimacy, these fake installers are often signed with dubious digital certificates from issuers such as 4th State Oy and NRM NETWORK RISK MANAGEMENT INC. This tactic helps the malicious software evade basic security checks that typically flag unsigned applications.
Deployment of the Oyster Backdoor
Upon execution of the counterfeit installer, a multi-stage attack is initiated, culminating in the deployment of a persistent backdoor known as Oyster, also referred to as Broomstick. The malware drops a malicious DLL file named `CaptureService.dll` into the `%APPDATA%\Roaming` directory and establishes persistence by creating a scheduled task called `CaptureService`. This task is configured to run the DLL at regular intervals, ensuring the backdoor remains active even after system reboots and allowing it to blend seamlessly with normal Windows operations.
The Oyster backdoor provides attackers with a robust foothold in the compromised network. It facilitates remote access, collects system information, and communicates with command-and-control (C2) servers to exfiltrate data and receive further instructions or payloads. In this campaign, Oyster has been observed communicating with C2 domains such as `nickbush24[.]com` and `techwisenetwork[.]com`.
Broader Implications and Similar Campaigns
This campaign is part of a larger trend where cybercriminals weaponize well-known software brands to achieve initial access. Similar tactics have been observed in previous campaigns distributing fake installers for applications like PuTTY, WinSCP, and Google Chrome. By leveraging malvertising and SEO poisoning, attackers effectively target a broad audience, exploiting user trust in both search engines and popular enterprise tools.
The use of the Oyster backdoor is particularly concerning, as it has been linked to ransomware operations like Rhysida, which have utilized it to infiltrate corporate networks. This strategy signifies a shift where threat actors are not solely relying on phishing emails but are actively compromising the software supply chain at the user-download level.
Mitigation Strategies
To mitigate the risks associated with such attacks, organizations and individuals are strongly advised to:
– Download Software from Official Sources: Always obtain software directly from official vendor websites. Avoid downloading applications from third-party sites or links provided in unsolicited communications.
– Use Bookmarks for Frequent Downloads: For frequently accessed download pages, use saved bookmarks instead of relying on search engine results, especially sponsored advertisements, which can be manipulated by attackers.
– Verify Digital Signatures: Before executing any downloaded installer, verify its digital signature to ensure it originates from a trusted source. Be cautious of software signed with unfamiliar or untrusted certificates.
– Educate Users: Conduct regular training sessions to raise awareness about social engineering tactics and the importance of downloading software from legitimate sources.
– Implement Endpoint Protection: Deploy robust endpoint detection and response (EDR) solutions capable of identifying and mitigating malicious activities associated with such campaigns.
By adopting these proactive measures, users and organizations can significantly reduce the risk of falling victim to these sophisticated cyberattacks.