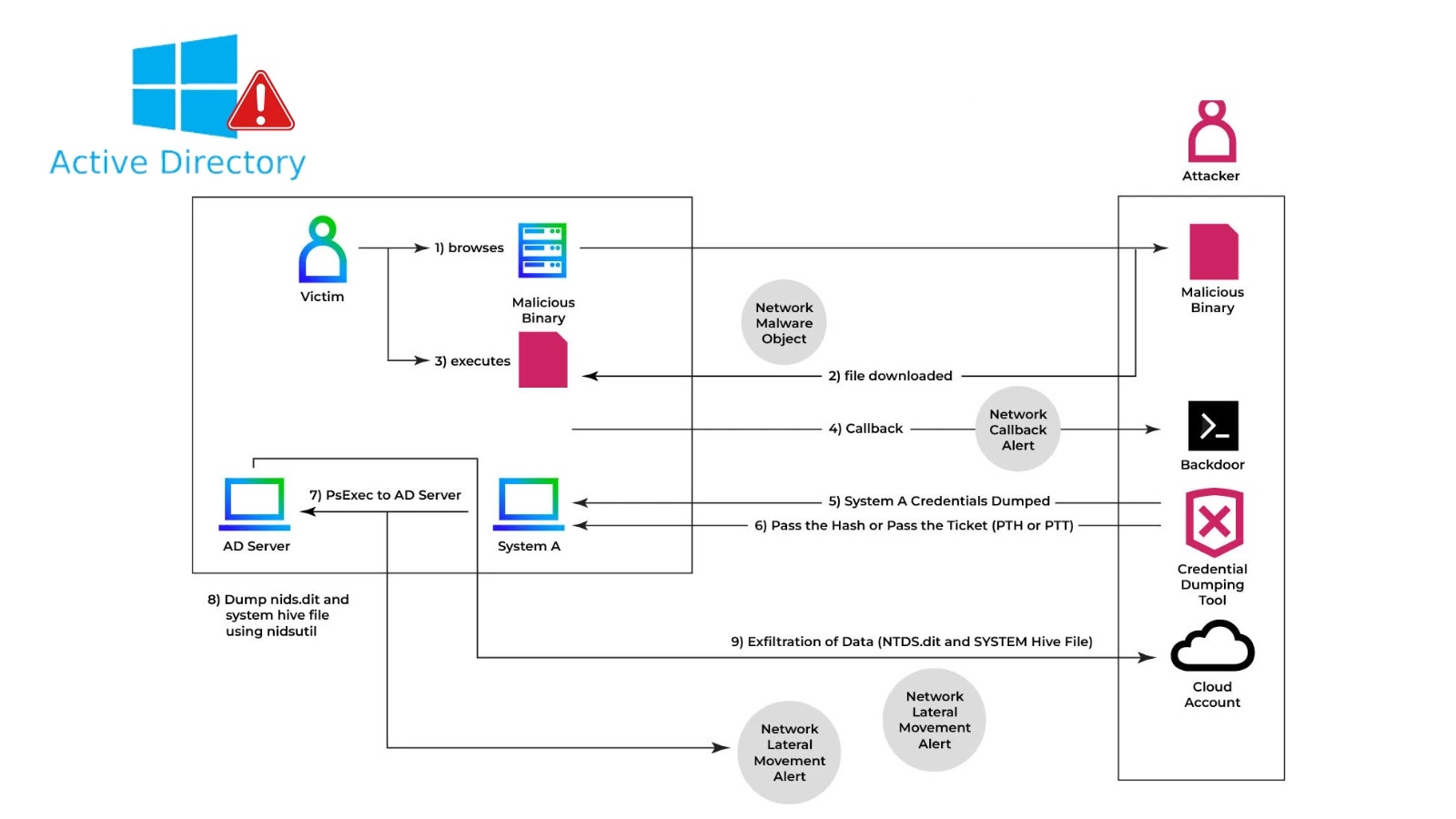
Active Directory (AD) serves as the cornerstone for authentication and authorization within Windows environments. Its central database, NTDS.dit, contains critical information, including user credentials and security descriptors. When malicious actors gain access to this database, they can potentially compromise the entire domain.
The Attack Vector
In a recent incident, attackers initiated their campaign with a phishing attack, successfully obtaining Domain Administrator privileges. With these elevated rights, they executed the following command:
“`
vssadmin create shadow /for=C:
“`
This command creates a Volume Shadow Copy, allowing the attackers to bypass file locks and access NTDS.dit. Subsequently, they extracted the database using:
“`
esentutl /y /vss c:\windows\ntds\ntds.dit /d c:\temp\ntds.dit
“`
To decrypt the extracted data, the SYSTEM registry hive was also obtained:
“`
reg save HKLM\SYSTEM c:\temp\SYSTEM
“`
With both NTDS.dit and the SYSTEM hive in their possession, attackers utilized tools like secretsdump.py from Impacket to decrypt and extract NTLM and AES password hashes for all domain accounts.
Exfiltration Process
The compromised data was archived and compressed using:
“`
tar -czf ntds.tar.gz c:\temp\ntds.dit c:\temp\SYSTEM
“`
The resulting archive was then exfiltrated over SMB to a compromised file share, enabling the attackers to maintain a low profile during data transfer.
Detection and Response
Security solutions like Trellix identified this malicious activity through high-fidelity signatures. Anomalous SMB write patterns exceeding baseline volumes and specific exfiltration signatures for large NTDS file transfers were flagged. Behavioral detection mechanisms also highlighted unexpected esentutl processes running outside standard maintenance windows.
AI-driven alert correlation further streamlined the detection process, reducing analyst workload by 60% and cutting mean time to detect (MTTD) by 45%.
Implications and Mitigation
The unauthorized access and exfiltration of NTDS.dit pose a significant threat to Windows domains. With this data, attackers can gain complete control over all credentials, facilitating lateral movement and potential full domain compromise.
Traditional defenses may not detect the subtle techniques employed during shadow copy creation and offline decryption. Therefore, organizations must adopt a multi-layered security approach, including:
– Regular Monitoring: Implement continuous monitoring of domain controllers for unusual activities, such as unexpected shadow copy creations or esentutl executions.
– Access Controls: Limit administrative privileges and ensure that only authorized personnel have access to critical systems and data.
– Incident Response Planning: Develop and regularly update incident response plans to address potential breaches promptly.
– User Education: Conduct regular training sessions to educate users about phishing attacks and other common threat vectors.
By implementing these measures, organizations can enhance their security posture and mitigate the risks associated with Active Directory breaches.