A sophisticated cybercriminal campaign has been identified, targeting Android users in Indonesia and Vietnam. This operation involves banking trojans disguised as legitimate government identity applications and payment services, aiming to steal sensitive financial information.
Campaign Overview
Active since August 2024, the campaign employs advanced evasion techniques to distribute variants of the BankBot trojan family. The attackers have established an extensive infrastructure comprising over 100 domains to facilitate their malicious activities.
Deceptive Tactics
The threat actors exhibit significant operational sophistication by creating fake Google Play Store pages and replicating government service applications, such as M-Pajak tax payment services and digital identity verification systems. By exploiting user trust in official platforms, they deceive victims into downloading malicious APK files embedded with banking trojans capable of harvesting financial credentials.
Advanced Delivery Mechanism
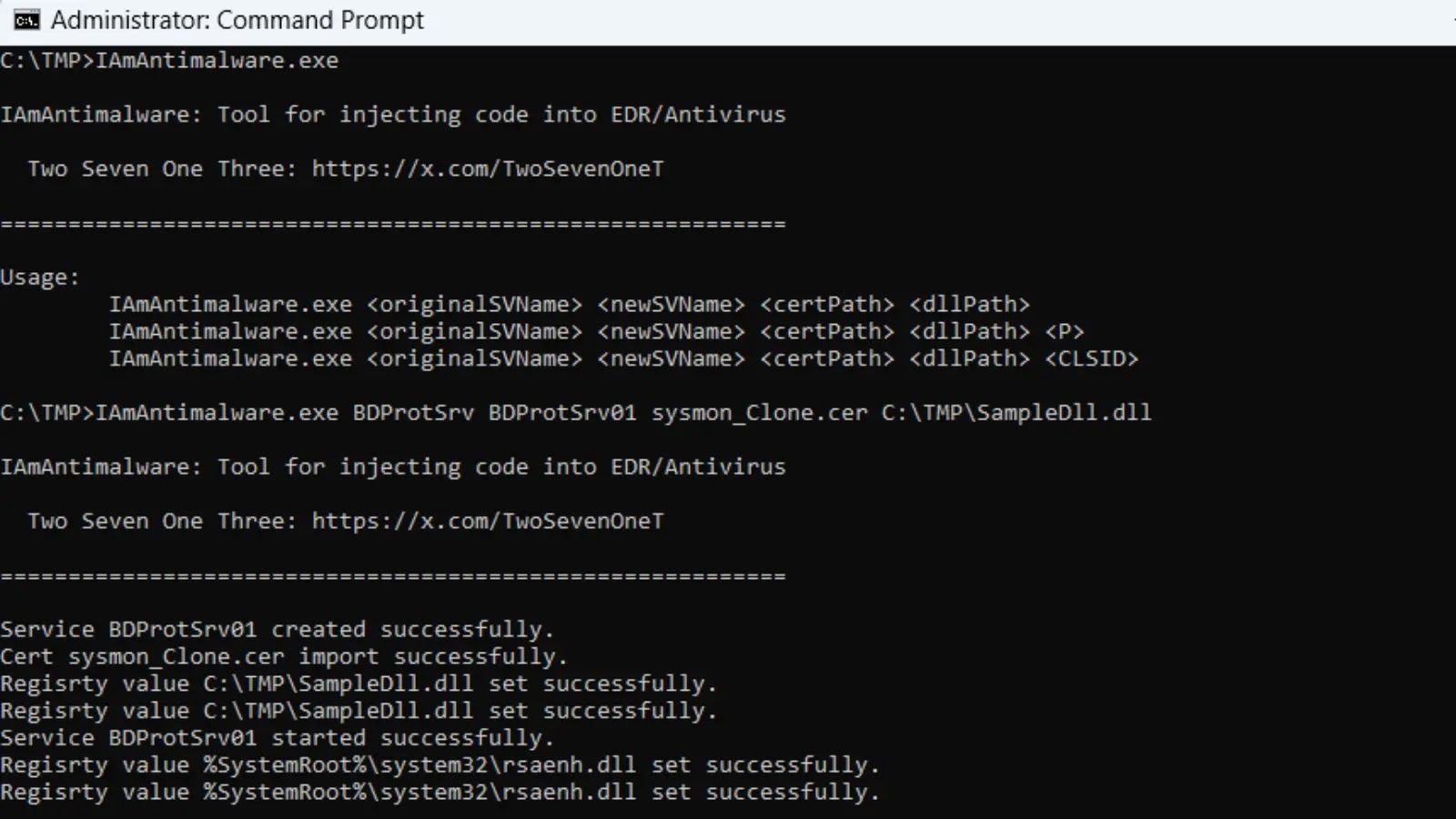
To circumvent traditional network security controls and evade automated detection systems, the attackers utilize a sophisticated malware delivery system leveraging WebSocket technology. Instead of providing direct download links, which are easily detectable by security scanners, the malicious sites use the Socket.IO library to establish real-time bidirectional communication channels between the victim’s browser and command servers.
When users click the Android download button, the system initiates a WebSocket connection using the command `socket.emit(‘startDownload’, …)`. The server responds by transmitting the malicious APK file in fragmented chunks rather than as a complete file transfer. The browser collects these fragments through event listeners coded as `socket.on(‘chunk’, (chunk) => { chunks.push(chunk); });`, while simultaneously receiving progress updates that maintain the illusion of a legitimate download process.
Upon completion, the system combines all received chunks in memory and assigns the MIME type `application/vnd.android.package-archive` to create a proper APK file structure. The delivery mechanism then generates a temporary local URL and programmatically triggers an invisible download link, prompting the browser’s standard file download interface.
This elaborate process effectively disguises malware distribution as encrypted WebSocket traffic, allowing malicious payloads to bypass network security systems configured to block direct APK downloads while remaining invisible to static URL-based security scanners that crawl websites for malicious links.
Implications and Recommendations
The use of such advanced techniques underscores the evolving nature of cyber threats targeting mobile users. To mitigate the risk of infection, users are advised to:
– Download applications only from official and reputable sources.
– Verify the authenticity of applications, especially those claiming to be from government agencies or financial institutions.
– Keep devices updated with the latest security patches.
– Utilize robust security solutions capable of detecting and preventing sophisticated malware.
By remaining vigilant and adopting these practices, users can better protect themselves against such deceptive and harmful cyber campaigns.