In the evolving landscape of cybersecurity threats, attackers are increasingly exploiting Microsoft Exchange inbox rules to establish persistence and exfiltrate data within enterprise environments. A newly developed tool, known as Inboxfuscation, leverages Unicode-based obfuscation techniques to craft malicious inbox rules that can bypass conventional security controls. This innovative approach poses significant challenges for detection and mitigation, necessitating a deeper understanding of the methods employed and the strategies required to counteract them.
Understanding Inboxfuscation and Its Implications
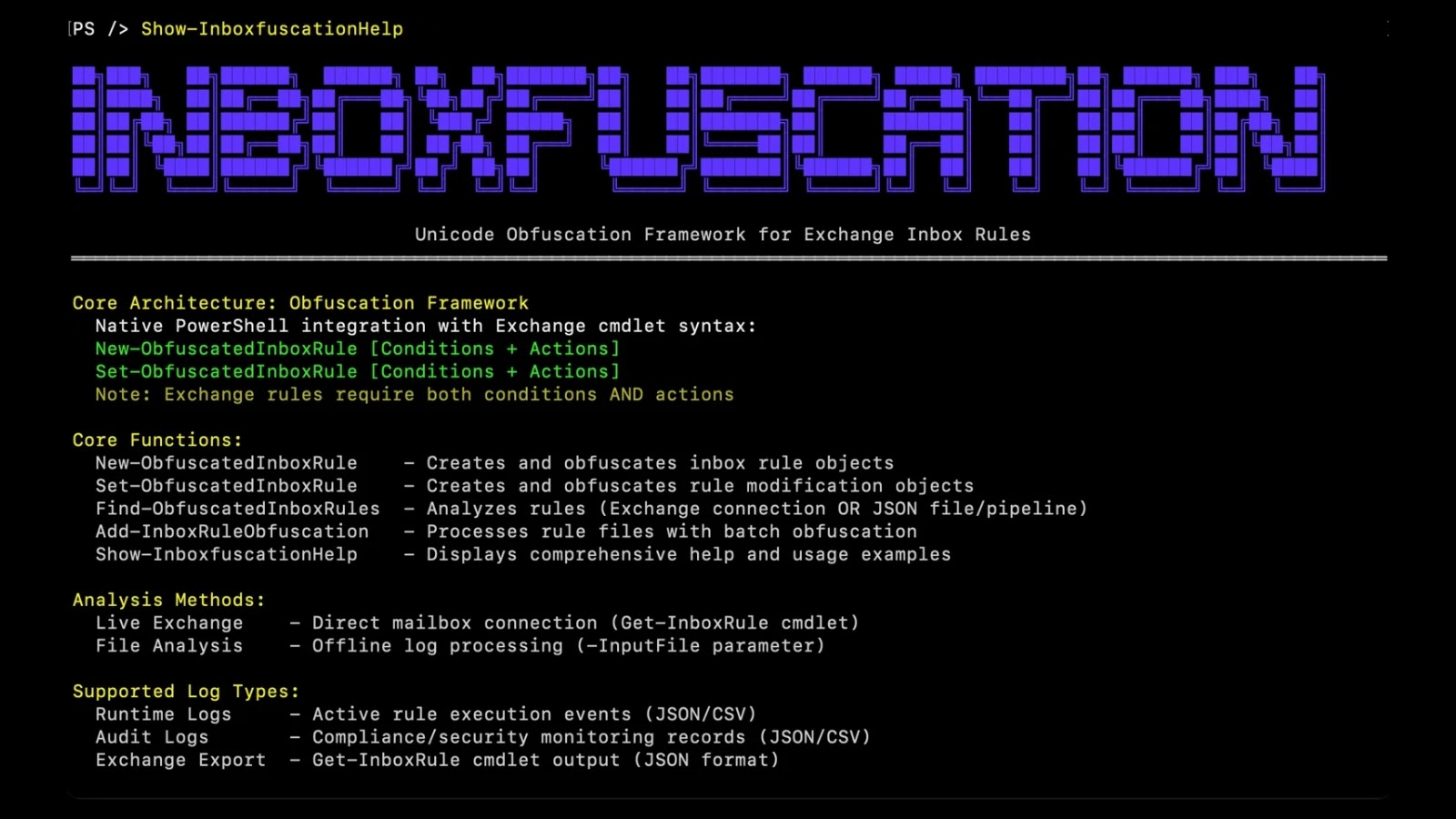
Inboxfuscation is a framework developed by Permiso that demonstrates how attackers can weaponize Exchange’s rule engine to create stealthy persistence mechanisms. By utilizing Unicode-based obfuscation, this tool enables the creation of malicious inbox rules that evade both human review and code-based detection. The implications of such a tool are profound, as it highlights a critical blind spot in current email security postures and underscores the need for advanced detection mechanisms.
The Mechanics of Unicode-Based Evasion
Traditional inbox rule attacks have typically relied on clear-text keywords and straightforward actions, such as forwarding or deleting messages. These methods are easily flagged by keyword-based detection systems and regular expression (regex) matching. Inboxfuscation, however, transforms this paradigm by employing several sophisticated techniques:
– Substitution with Unicode Variants: Attackers replace standard ASCII characters with visually identical Unicode characters. For example, the word secret can be obfuscated using characters from the MATHEMATICAL ALPHANUMERIC SYMBOLS Unicode block (U+1D4B6), resulting in a string that appears identical to the human eye but differs at the code level.
– Injection of Zero-Width Characters: By inserting zero-width spaces (U+200B) within keywords, attackers can disrupt pattern matching without altering the visual representation of the text.
– Manipulation of Text Directionality: Utilizing bidirectional text control characters, such as RIGHT-TO-LEFT OVERRIDE (U+202E), attackers can alter the display order of characters, further complicating detection efforts.
– Combination of Obfuscation Techniques: By integrating multiple obfuscation methods, attackers can create complex rules that are challenging to detect using conventional security tools.
These techniques exploit the fact that many detection systems are designed to recognize patterns in ASCII text and may not account for the nuances of Unicode characters. As a result, malicious rules crafted using Inboxfuscation can appear benign in Exchange’s Get-InboxRule output while effectively matching sensitive keywords.
Functional Obfuscation Tactics
Beyond character substitution, Inboxfuscation introduces functional obfuscation strategies that enhance the stealthiness of malicious rules:
– Forwarding to Non-Standard Folders: Instead of forwarding emails to external addresses, which is a common red flag, attackers can configure rules to redirect emails to internal folders like the Calendar. This method allows for data exfiltration without triggering external communication alerts.
– Insertion of Null Characters: By embedding null characters (\u0000) within rule definitions, attackers can render these rules invisible to standard retrieval commands, making them difficult to audit and remove.
Challenges in Detection and Mitigation
Conventional detection tools are often ill-equipped to handle Unicode obfuscation due to their reliance on ASCII-based pattern matching and visual similarity assessments. Inboxfuscation’s approach exposes the limitations of these tools and underscores the need for more sophisticated detection mechanisms.
Permiso’s Detection Framework
To address this emerging threat, Permiso has extended its Arbiter Detection module to analyze events across mailboxes and reconstruct multi-step rule creation behaviors. Key components of this detection framework include:
– Character Category Analysis: By examining the character categories used in inbox rules, the system can identify the presence of unusual Unicode characters that may indicate obfuscation attempts.
– Multi-Format Log Parsing: The framework supports various log formats, including JSON, CSV, Exchange export, and Microsoft 365 Graph API logs, enabling comprehensive analysis across different data sources.
– Rule Audit and Historical Analysis: By auditing existing rules and analyzing their historical changes, the system can detect anomalies and patterns indicative of malicious activity.
– SIEM Integration: Structured outputs, including rule names, mailboxes, risk scores, and Unicode character counts, facilitate integration with Security Information and Event Management (SIEM) systems for centralized monitoring and response.
Proactive Mitigation Strategies
To effectively mitigate the risks posed by Unicode-based obfuscation, security teams should implement the following strategies:
– Develop Unicode-Aware Detection Rules: Enhance existing detection systems to recognize and flag suspicious Unicode characters and patterns within inbox rules.
– Conduct Comprehensive Inbox Rule Audits: Regularly review and audit inbox rules across the organization to identify and remediate unauthorized or anomalous configurations.
– Simulate Obfuscated Rules in Testing Environments: Create and test obfuscated rules in controlled environments to understand their behavior and refine detection capabilities.
– Update Exchange Monitoring Pipelines: Modify monitoring systems to flag the use of suspicious Unicode categories and leverage sandboxed environments to inspect rule normalization behaviors.
The Broader Implications for Email Security
While Unicode obfuscation techniques like those employed by Inboxfuscation have not yet been widely observed in live attacks, their technical feasibility exposes a significant vulnerability in current email security measures. By proactively adopting advanced detection frameworks and understanding the mechanics of Unicode-based evasion, defenders can stay ahead of emerging Advanced Persistent Threat (APT) tactics and protect enterprise communications from stealthy persistence techniques.
Conclusion
The advent of tools like Inboxfuscation underscores the continuous evolution of cyber threats and the need for adaptive security measures. By recognizing the potential for Unicode-based obfuscation to bypass traditional detection methods, organizations can implement more robust monitoring and mitigation strategies. Staying informed about such developments and proactively enhancing security postures are essential steps in safeguarding enterprise environments against sophisticated attacks.