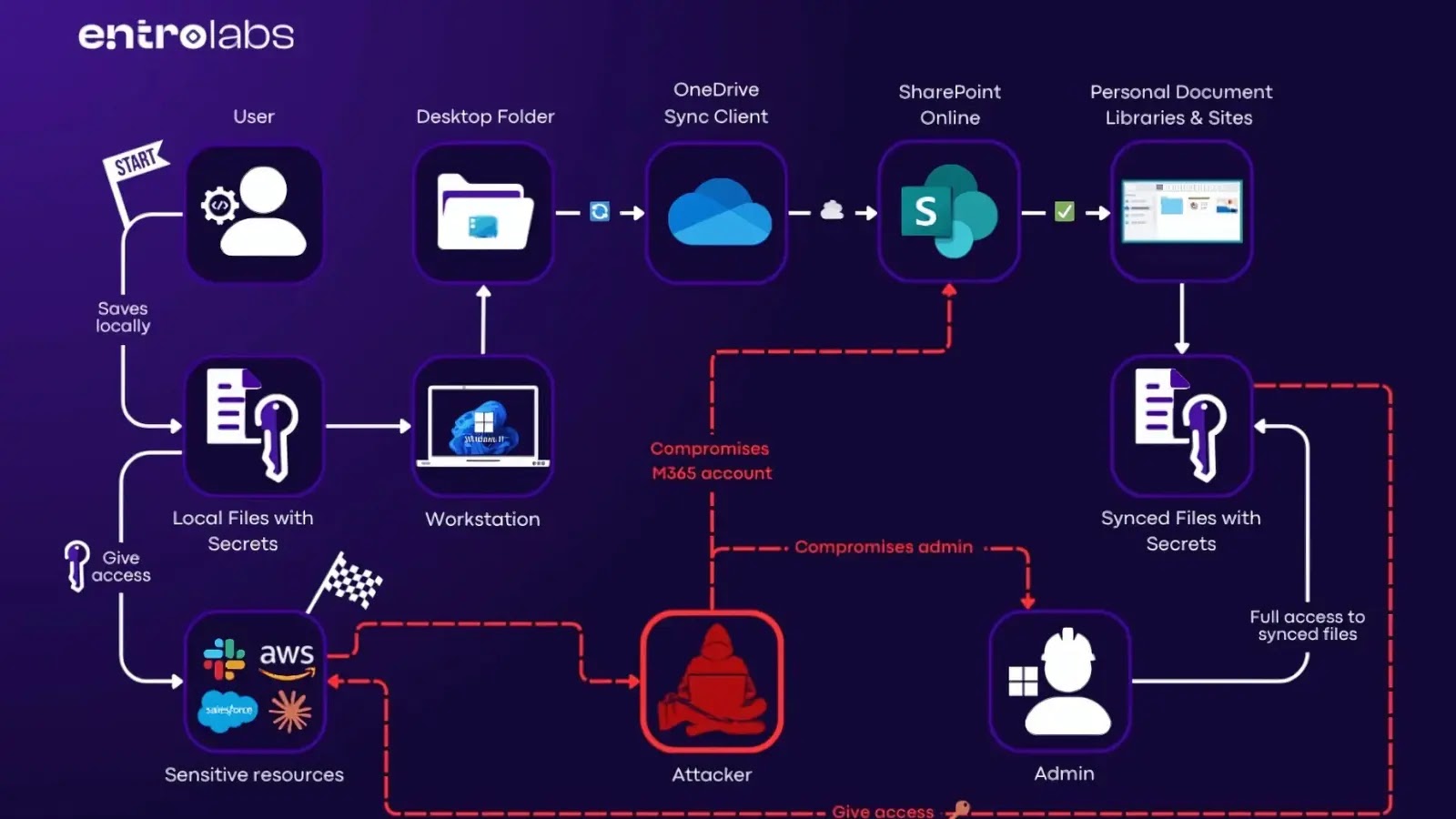
Microsoft OneDrive’s default auto-sync functionality, particularly the Known Folder Move (KFM) feature, is inadvertently exposing sensitive enterprise data by automatically transferring local files to SharePoint Online. This process, intended to enhance user convenience, has been identified as a significant security vulnerability, with research indicating that approximately 20% of exposed secrets within enterprises originate from files synced to SharePoint.
Understanding the Known Folder Move (KFM) Feature
KFM is designed to automatically synchronize essential user folders, such as Desktop and Documents, with OneDrive. In enterprise environments, this synchronization extends to SharePoint Online document libraries, ensuring that users can access their files across various devices. However, this seamless integration also means that sensitive information stored in these folders becomes accessible to a broader audience than initially intended.
From Local Storage to Widespread Exposure
The core issue lies in the silent upload of locally saved files, including configuration files like .env or .json, and spreadsheets named passwords.xlsx, to the cloud. Once these files reside in SharePoint, they are governed by the platform’s sharing and access policies, making them accessible to administrators who can grant themselves permissions to read these synced files. Consequently, what begins as a local backup can escalate into a potential organization-wide vulnerability.
This risk is not confined to enterprise accounts. On Windows 10 and 11, the OneDrive sync client is enabled by default for personal accounts as well. Users often bypass the initial setup, where the option to opt out is presented as a recommended step, leading to their files being backed up without their full awareness.
Patterns of Secret Exposure in SharePoint
Research into enterprise environments has identified common patterns of secret exposure in SharePoint. Specific file types are particularly likely to contain unencrypted secrets:
– Spreadsheets (.xlsx): Over 50% of secrets found on SharePoint were located in workbooks used for tracking, logs, or as developer scratchpads.
– Plain Text Files: Files such as .txt, .json, and .pem accounted for 18% of the exposed secrets. These often contain configuration details or certificate bundles.
– Scripts and Documents: PowerShell scripts, SQL dumps, and Word documents also frequently contained credentials, demonstrating that almost any file can become a security risk when automatically synced.
This auto-sync functionality undermines a standard security best practice for developers, who store secrets in local .env files to avoid hardcoding them in source code. With KFM enabled, these supposedly local-only files are synced to SharePoint, making them discoverable across the entire Microsoft 365 tenant.
The Silent Expansion of Security Breaches
The silent nature of this auto-sync feature significantly amplifies the potential damage of a security breach. If an attacker compromises a single Microsoft 365 user account, they not only gain access to emails and applications but also to all the local files synced from the user’s computer. For a compromised administrator account, the risk is even greater, as they can systematically search the entire SharePoint environment for sensitive data.
Attackers can automate searches for keywords like password, API key, or token to locate and exfiltrate secrets quickly.
Mitigation Strategies
To mitigate this risk, security experts recommend several actions:
1. Raise Awareness: Organizations should educate employees, especially developers, about how their local files may be exposed through auto-sync features.
2. Disable Auto-Sync Where Unnecessary: Administrators can use Group Policy or Intune to disable the auto-sync feature in scenarios where it is not necessary.
3. Implement Continuous Scanning: Security teams should deploy solutions to continuously scan SharePoint environments for exposed secrets, detecting and remedying them before they can be exploited.
By proactively addressing these vulnerabilities, organizations can better protect their sensitive data from unintended exposure and potential exploitation.