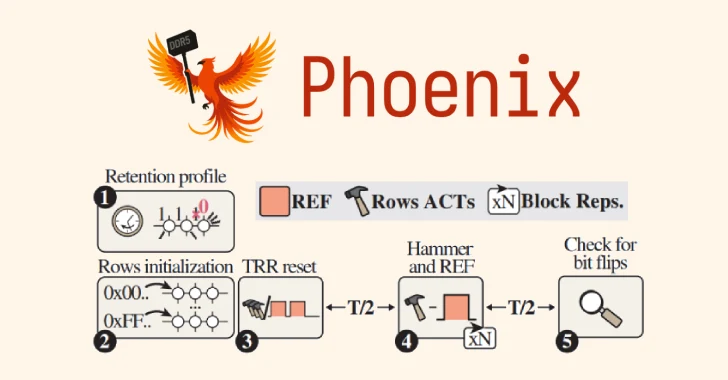
A collaborative research effort between ETH Zürich and Google has unveiled a new variant of the RowHammer attack, named Phoenix (CVE-2025-6202, CVSS score: 7.1), which successfully compromises DDR5 memory chips manufactured by SK Hynix. This discovery underscores the persistent vulnerabilities in modern DRAM technologies, even as they incorporate advanced protective measures.
RowHammer is a hardware vulnerability that exploits the physical properties of DRAM cells. By repeatedly accessing (or hammering) a specific row of memory, an attacker can induce electrical disturbances that cause bit flips in adjacent rows, leading to data corruption. These unintended bit flips can be weaponized to gain unauthorized access, escalate privileges, or disrupt system operations.
Since its initial revelation in 2014, RowHammer has been a significant concern for hardware security. As DRAM manufacturers pursue higher memory densities to meet increasing performance demands, the susceptibility to such attacks has intensified. Research from ETH Zürich in 2020 highlighted that newer DRAM chips require fewer activation cycles to induce bit flips, making them more vulnerable to RowHammer exploits.
To counteract RowHammer attacks, several mitigation strategies have been implemented:
– Error Correction Code (ECC): Designed to detect and correct minor memory errors, ECC was believed to offer a layer of protection against bit flips.
– Target Row Refresh (TRR): This mechanism identifies frequently accessed (or aggressor) rows and refreshes their neighboring rows to prevent bit flips.
However, sophisticated attack variants such as TRRespass, SMASH, Half-Double, and Blacksmith have demonstrated the ability to circumvent these defenses. The Phoenix attack further exemplifies this trend by effectively bypassing TRR protections in DDR5 memory modules.
In their study, the researchers conducted tests on 15 DDR5 memory chips produced between 2021 and 2024. The Phoenix attack successfully induced bit flips across all tested modules, achieving root-level privilege escalation on a standard desktop system equipped with DDR5 memory in just 109 seconds. This rapid exploitation underscores the critical nature of the vulnerability.
The implications of the Phoenix attack are profound:
– Cryptographic Compromise: By targeting RSA-2048 keys within co-located virtual machines, attackers can potentially break SSH authentication, undermining secure communications.
– Privilege Escalation: Manipulating the ‘sudo’ binary allows attackers to elevate local privileges, granting them unauthorized control over the system.
Given the hardware-based nature of RowHammer vulnerabilities, software patches alone are insufficient. The researchers recommend increasing the memory refresh rate by a factor of three, a measure that effectively prevented the Phoenix attack in their test environments. However, this solution may lead to increased power consumption and potential performance degradation.
This discovery follows closely on the heels of other RowHammer-related research:
– OneFlip: A technique that induces a single bit flip to alter Deep Neural Network (DNN) model weights, leading to unintended behaviors.
– ECC.fail: An end-to-end RowHammer attack that effectively compromises DDR4 server machines equipped with ECC memory, challenging the reliability of error correction mechanisms.
The Phoenix attack serves as a stark reminder of the evolving nature of hardware vulnerabilities and the necessity for continuous research and adaptive defense mechanisms in the realm of cybersecurity.