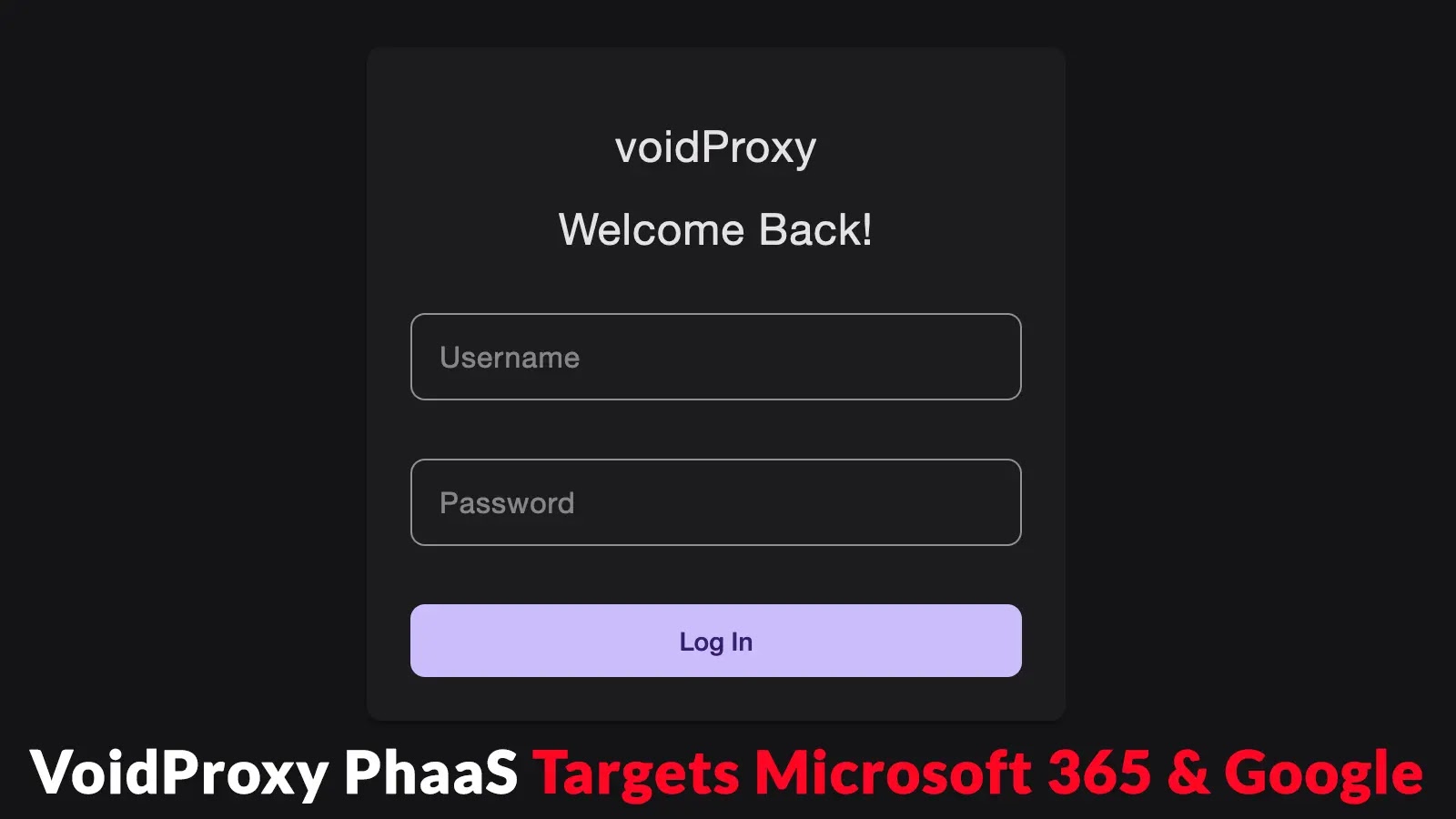
In recent months, cybersecurity experts have identified a significant uptick in advanced phishing campaigns utilizing a newly uncovered Phishing-as-a-Service (PhaaS) platform known as VoidProxy. First detected in August 2025, VoidProxy employs a combination of anti-analysis techniques and adversary-in-the-middle (AitM) capabilities to stealthily target Microsoft 365 and Google accounts.
Sophisticated Attack Mechanisms
VoidProxy’s operations commence with phishing emails sent from compromised legitimate Email Service Provider (ESP) accounts, effectively bypassing spam filters. These emails incorporate multiple redirects through URL shortening services, complicating detection efforts.
Security analysts at Okta identified the initial infrastructure through alerts triggered by anomalies in FastPass enrollment. Users protected by phishing-resistant authenticators received warnings about unusual sign-in attempts, leading to the discovery of VoidProxy’s activities.
The platform utilizes disposable, low-reputation domains (such as .icu, .xyz, .top) hosted behind Cloudflare to obscure the actual server IP addresses, making takedown efforts more challenging. Before accessing any page, victims are required to complete a Cloudflare CAPTCHA challenge to confirm human interaction. This measure effectively neutralizes automated scanners and security tools, which are presented with a generic welcome page instead.
Upon passing the CAPTCHA, the victim’s browser communicates with a Cloudflare Worker service that filters traffic and loads the appropriate phishing portal. These portals are meticulously designed to replicate legitimate login pages for both Microsoft and Google, including support for federated single sign-on (SSO) via Okta.
Advanced Credential Harvesting
VoidProxy’s AitM engine is particularly sophisticated in its ability to intercept session cookies and tokens in real time. When a legitimate service returns a session cookie, the proxy exfiltrates a copy to the attacker’s admin panel, granting immediate access to the compromised account.
The backend infrastructure employs dynamic DNS wildcard services (such as sslip.io and nip.io) to host ephemeral AitM proxy engines and customer-facing admin panels. The VoidProxy admin panel dashboard allows threat actors to configure campaigns, monitor victims, and collect stolen credentials efficiently.
Infection Mechanism and Evasion Tactics
The infection chain initiated by VoidProxy begins with well-crafted phishing emails that exploit the reputation of legitimate ESPs. The multi-tier redirect chain not only evades URL-based detection but also ensures that each disposable domain is used briefly before being abandoned, further complicating tracking efforts.
The Cloudflare Worker gatekeeper segregates legitimate targets from analysis tools, while CAPTCHA challenges add an additional layer of defense against automated analysis.
Behind the scenes, the AitM proxy server integrates robust session hijacking techniques. After validating credentials against Microsoft, Google, or Okta, it relays the session cookie to attackers while maintaining an active connection for the user.
A sample proxy snippet demonstrates how the engine captures and logs session tokens:
“`javascript
fetch(targetUrl, {
method: ‘POST’,
headers: request.headers,
body: request.body
}).then(response => {
const sessionCookie = response.headers.get(‘set-cookie’);
logStolenCookie(sessionCookie);
return response;
});
“`
This seamless relay ensures that victims remain unaware of the compromise, allowing attackers to perform business email compromise (BEC), data exfiltration, and lateral movement within enterprise environments.
Implications and Defensive Measures
The emergence of VoidProxy underscores the evolving sophistication of phishing attacks and the increasing accessibility of advanced tools to cybercriminals. Phishing-as-a-Service platforms like VoidProxy lower the barrier to entry for less-skilled threat actors, enabling them to launch complex attacks with relative ease.
To defend against such threats, organizations should implement multi-layered security measures, including:
– Phishing-Resistant Authentication: Adopt authentication methods that are resistant to phishing, such as hardware tokens or biometric verification, to reduce the risk of credential theft.
– Email Filtering and Monitoring: Enhance email filtering systems to detect and block phishing attempts, and monitor for anomalies in email traffic patterns.
– User Education and Awareness: Conduct regular training sessions to educate employees about the latest phishing tactics and how to recognize suspicious emails and links.
– Incident Response Planning: Develop and regularly update incident response plans to quickly address and mitigate the impact of phishing attacks.
By understanding the mechanisms employed by platforms like VoidProxy and implementing robust security protocols, organizations can better protect themselves against the growing threat of sophisticated phishing campaigns.