In the rapidly evolving landscape of artificial intelligence (AI), ensuring the security of AI systems has become paramount. Introducing Red AI Range (RAR), an open-source platform designed to enhance the security posture of AI applications by simulating realistic attack scenarios. RAR streamlines the discovery, analysis, and mitigation of AI-specific vulnerabilities, providing security professionals with a comprehensive toolkit to fortify AI systems against potential threats.
Key Features of Red AI Range:
1. Containerized Architecture: RAR employs a sophisticated Docker-in-Docker implementation, allowing for the isolation of conflicting dependencies across multiple AI frameworks. This ensures that each simulated AI target and testing tool operates within its own container, maintaining environmental consistency and enabling rapid resets to baseline configurations.
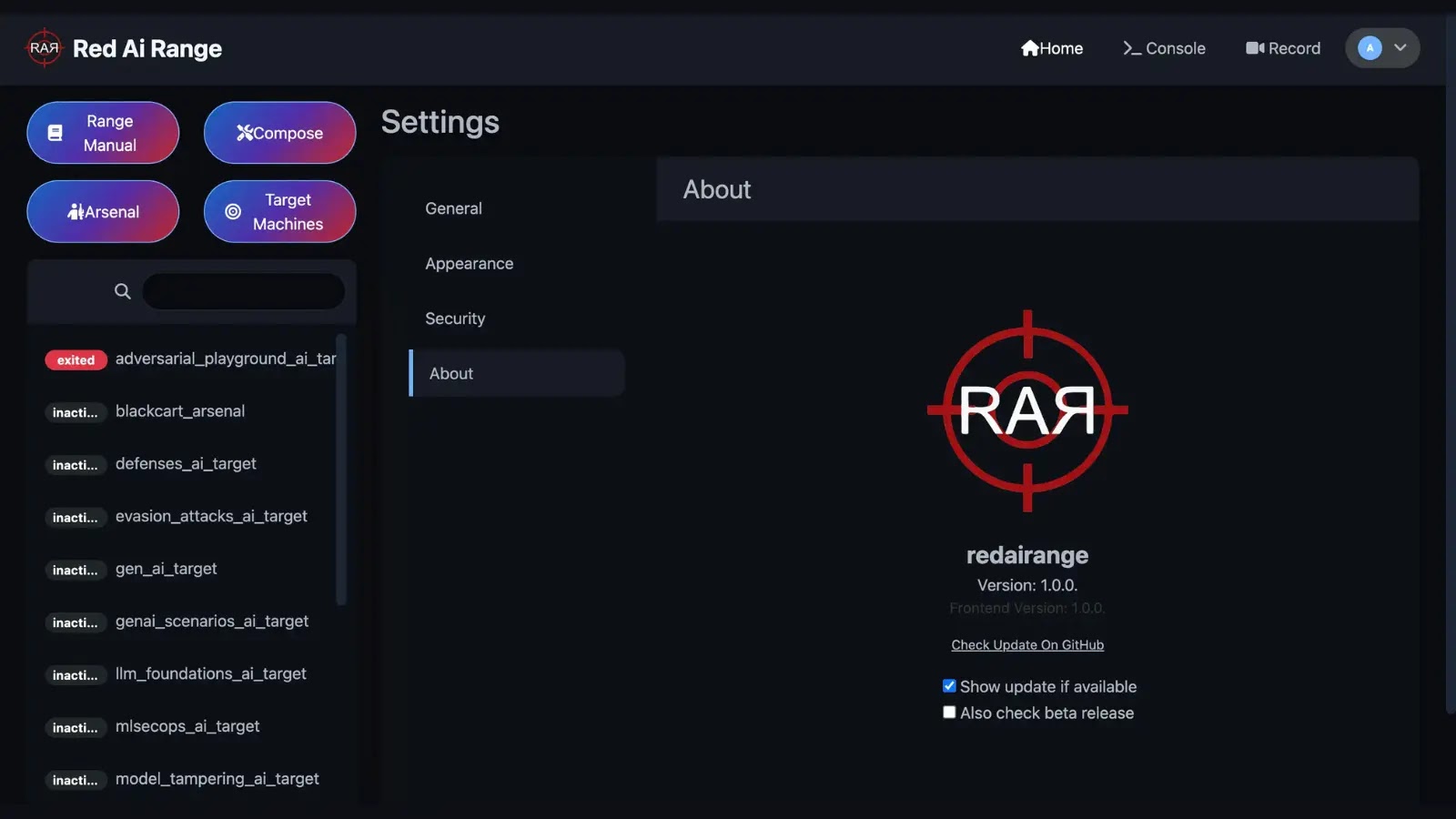
2. Interactive Dashboard: The platform features an intuitive web-based interface where users can deploy vulnerability scanners, adversarial-attack frameworks, and intentionally vulnerable AI models. The dashboard provides real-time activity status, displaying active, exited, and inactive environments, and offers controls to convert running instances into reusable Docker Compose files.
3. Session Recording: RAR includes an integrated session recorder that captures video recordings and timestamped logs of red teaming exercises. This functionality facilitates comprehensive post-test analysis and knowledge transfer, allowing teams to review and refine their security strategies effectively.
4. Comprehensive Training Modules: Beyond its core deployment capabilities, RAR offers a suite of training modules covering foundational AI security concepts through advanced adversarial techniques. Topics include poisoning attacks, such as clean-label backdoor injection, and evasion methods like Projected Gradient Descent (PGD) and Carlini & Wagner (C&W) attacks. Each module provides Jupyter Notebook tutorials, enabling practitioners to experiment interactively with code examples in a controlled environment.
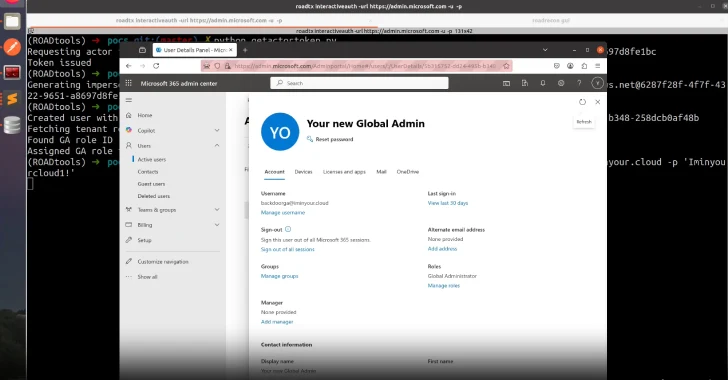
5. Remote Agent Architecture: RAR supports a remote agent architecture, allowing teams to distribute testing workloads across GPU-enabled hosts on AWS or on-premises GPU clusters. Secure authentication between the central RAR console and remote agents ensures that large-scale vulnerability assessments, especially those targeting large language models (LLMs) or high-compute models, can be coordinated seamlessly. Agents register via a token-based handshake and appear in the Agent Control Panel for deployment orchestration.
Enhancing AI Vulnerability Assessment:
By integrating RAR into critical infrastructure testing pipelines, organizations can proactively identify weaknesses in machine learning models, data handling processes, and deployment configurations before adversaries exploit them. The platform’s containerized architecture ensures that each simulated AI target and testing tool runs in its own environment, preserving consistency and enabling rapid resets to baseline configurations.
The interactive dashboard allows red teamers to deploy various tools and models, each appended with _arsenal or _ai_target to their stack name for clear identification. Once containers are up, the dashboard displays real-time activity status, showing active, exited, and inactive environments, and provides controls to convert running instances into reusable Docker Compose files.
The integrated session recorder effectively captures video recordings and timestamped logs of red teaming exercises, facilitating comprehensive post-test analysis and knowledge transfer. This feature is particularly beneficial for teams looking to review and refine their security strategies based on real-world scenarios.
Integrated Training Modules:
RAR’s training modules cover a wide range of topics, from foundational AI security concepts to advanced adversarial techniques. Modules include tutorials on poisoning attacks, such as clean-label backdoor injection, and evasion methods like PGD and C&W attacks. Each module provides Jupyter Notebook tutorials, enabling practitioners to experiment interactively with code examples in a controlled environment.
The platform also supports a remote agent architecture, allowing teams to distribute testing workloads across GPU-enabled hosts on AWS or on-premises GPU clusters. Secure authentication between the central RAR console and remote agents ensures that large-scale vulnerability assessments, especially those targeting LLMs or high-compute models, can be coordinated seamlessly. Agents register via a token-based handshake and appear in the Agent Control Panel for deployment orchestration.
Empowering Security Teams:
By consolidating AI-specific vulnerabilities, automation tools, and training resources into a unified framework, Red AI Range empowers security teams to elevate their AI red teaming operations. As enterprises continue to adopt AI in critical systems, integrating RAR into regular security workflows will be essential for uncovering hidden risks, refining mitigation strategies, and maintaining trust in AI-driven services.
In conclusion, Red AI Range represents a significant advancement in the field of AI security. Its comprehensive suite of tools and training modules provides security professionals with the resources needed to proactively identify and mitigate vulnerabilities in AI systems. As AI continues to permeate various sectors, platforms like RAR will play a crucial role in ensuring the security and reliability of AI-driven applications.