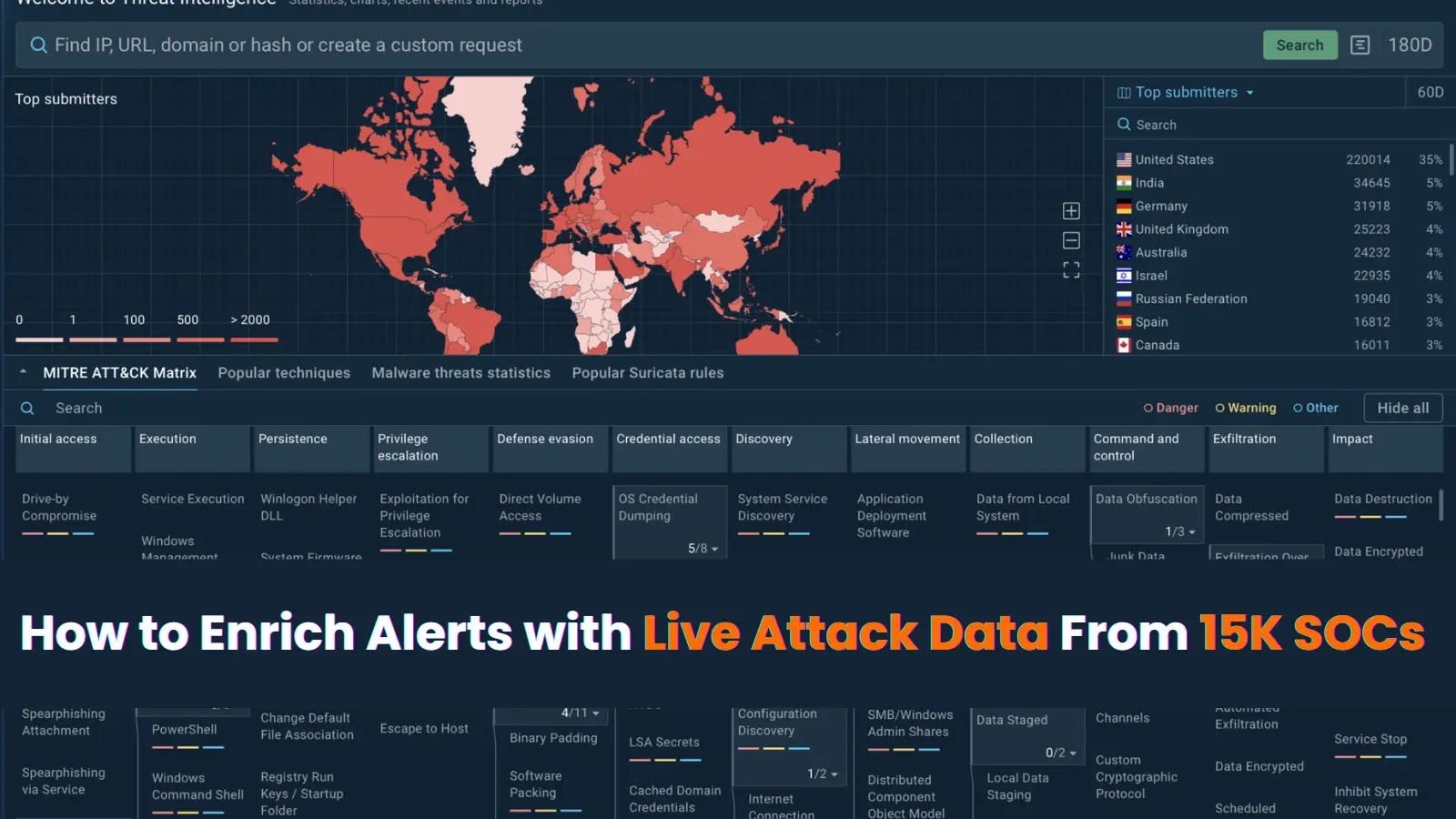
Security Operations Centers (SOCs) are inundated daily with a deluge of alerts generated by Security Information and Event Management (SIEM) systems. This overwhelming volume poses a significant challenge: how can analysts effectively prioritize and respond to these alerts without succumbing to alert fatigue? The key lies in enriching these alerts with live attack data sourced from a vast network of SOCs, thereby transforming raw data into actionable intelligence.
The Challenge of Alert Overload
Modern SOCs face an unprecedented influx of alerts, many of which are false positives or lack sufficient context. This scenario leads to:
– Alert Fatigue: Analysts become overwhelmed by the sheer number of alerts, potentially causing critical threats to be overlooked.
– Resource Drain: Time and resources are consumed in sifting through massive amounts of raw data, diverting attention from higher-value tasks such as incident response and threat hunting.
– Lack of Actionable Insights: Without sufficient context, raw indicators provide little guidance on how to respond, leaving analysts to make educated guesses about the relevance and severity of each alert.
The Importance of Contextual Threat Intelligence
Integrating contextual threat intelligence into SOC workflows is essential for transforming raw data into actionable insights. Contextual information includes:
– Threat Actor Attribution: Identifying the entities behind the attack, their motives, and their typical behaviors.
– Attack Patterns and Tactics: Understanding the methods and strategies employed by attackers, often mapped to frameworks like MITRE ATT&CK.
– Historical Data: Analyzing past incidents to recognize patterns and predict future threats.
By incorporating this context, SOCs can prioritize alerts more effectively, focusing on those that pose the most significant risk to the organization.
Leveraging Collective Defense Through Shared Data
The concept of collective defense involves sharing threat intelligence across organizations to enhance overall security posture. By accessing live attack data from a network of 15,000 SOCs, organizations can:
– Identify Emerging Threats: Detect new attack vectors and tactics as they are observed in the wild.
– Correlate Indicators of Compromise (IOCs): Cross-reference IOCs with data from other organizations to assess their relevance and severity.
– Enhance Incident Response: Utilize shared intelligence to inform and expedite response strategies.
Implementing Threat Intelligence Enrichment
To effectively enrich alerts with live attack data, organizations can adopt the following strategies:
1. Integrate Threat Intelligence Platforms (TIPs): Utilize platforms that aggregate and analyze threat data from multiple sources, providing real-time insights.
2. Automate Data Correlation: Implement automation tools that correlate incoming alerts with existing threat intelligence, reducing manual analysis time.
3. Establish Information Sharing Agreements: Participate in industry-specific information sharing and analysis centers (ISACs) to access and contribute to collective threat intelligence.
4. Continuous Training and Adaptation: Ensure that SOC analysts are trained to interpret and act upon enriched threat data, adapting to evolving threat landscapes.
Case Study: ANY.RUN’s Threat Intelligence Lookup
ANY.RUN offers a Threat Intelligence Lookup service that exemplifies the benefits of integrating live attack data into SOC operations. This service allows analysts to:
– Search for IOCs: Input hashes, IP addresses, domains, URLs, or files to retrieve relevant threat data.
– Access Real-World Attack Data: View information on how specific IOCs have been used in actual attacks observed across thousands of SOCs.
– Obtain Contextual Information: Gain insights into malware families, attack behaviors, and timestamps of malicious activities.
By leveraging such services, SOCs can enhance their alert management processes, making informed decisions swiftly and effectively.
Conclusion
In the face of escalating cyber threats and an overwhelming volume of alerts, enriching SOC alerts with live attack data from a broad network of SOCs is not just beneficial—it’s imperative. By integrating contextual threat intelligence, automating data correlation, and participating in collective defense initiatives, organizations can transform their SOCs into proactive, efficient, and resilient units capable of defending against sophisticated cyber adversaries.