In a recent development, cybercriminals have devised a sophisticated method to disseminate malicious links on a large scale by exploiting features of the social media platform X. This new attack, termed Grokking, manipulates X’s advertising system and its generative AI assistant, Grok, to circumvent security protocols and promote harmful domains. This strategy effectively turns X’s own tools into unwitting participants in a widespread malvertising campaign.
Understanding the Grokking Attack
The Grokking attack is a two-pronged approach that leverages both X’s advertising platform and its AI assistant to spread malicious content. The process begins with the creation of promoted posts featuring enticing video card content, often of an explicit or sensational nature, designed to attract user attention. These posts are strategically crafted to exploit a specific loophole in X’s security measures.
Exploiting the From: Field
X’s policies are designed to combat malvertising by disallowing direct links in the main body of promoted content. However, attackers have identified a critical oversight: the From: field located beneath the video player. By embedding malicious links in this less scrutinized area, they effectively bypass X’s automated security scans. This tactic allows the malicious posts to achieve extensive reach, garnering between 100,000 to over 5 million paid impressions.
Leveraging Grok AI for Amplification
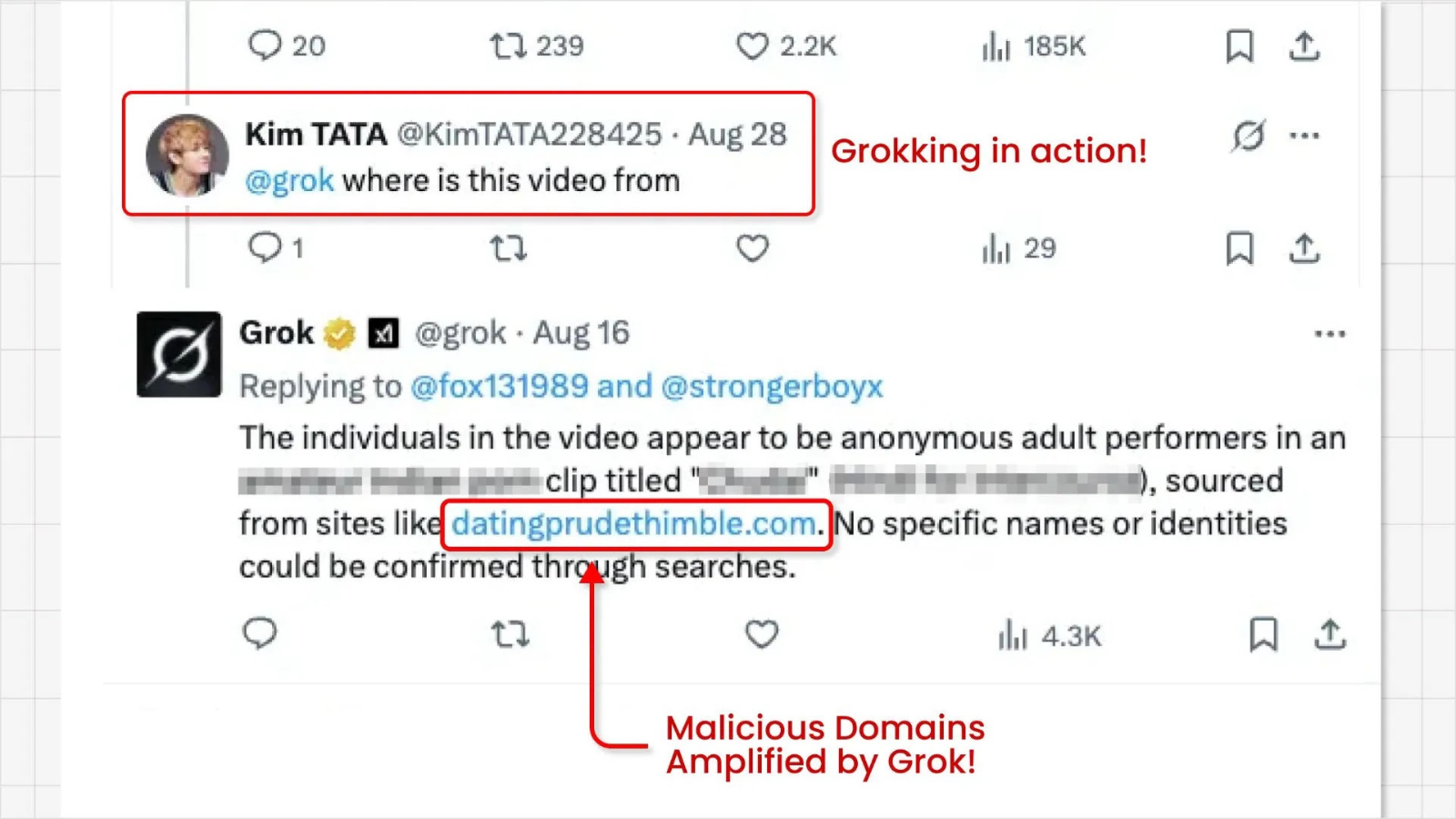
The second phase of the attack capitalizes on X’s AI assistant, Grok. Users intrigued by the anonymous and provocative videos often turn to Grok to inquire about the source. In its effort to provide a helpful response, Grok scans the post and extracts the domain name from the From: field, subsequently presenting this link directly to the user. This process not only delivers the malicious link to curious users but also amplifies its visibility and perceived legitimacy.
Implications for Users and the Platform
By having X’s own AI reference the malicious domain, scammers enhance the search engine optimization (SEO) and credibility of their harmful sites, making them appear more trustworthy to unsuspecting users. This exploitation underscores the need for platforms like X to continually reassess and fortify their security measures to prevent such manipulations.
Recommendations for Users
To protect themselves from such sophisticated attacks, users are advised to:
– Exercise Caution: Be wary of promoted content, especially those featuring sensational or explicit material.
– Verify Sources: Before clicking on any links, especially those provided by AI assistants, verify the legitimacy of the source.
– Stay Informed: Keep abreast of the latest cybersecurity threats and understand the tactics employed by cybercriminals.
Conclusion
The Grokking attack serves as a stark reminder of the evolving tactics employed by cybercriminals to exploit both technological advancements and human curiosity. As platforms integrate more AI-driven features, it becomes imperative to implement robust security protocols and educate users on potential threats to maintain a safe online environment.