In a recent development, cybercriminals have devised a sophisticated method to exploit the social media platform X’s advertising system and its generative AI assistant, Grok, to disseminate malicious links on a large scale. This new attack, termed Grokking, manipulates X’s internal tools to bypass security protocols, thereby facilitating a widespread malvertising campaign.
Understanding the Grokking Attack
The attack initiates with the promotion of video card posts that often feature explicit or sensational adult content designed to attract user attention. These posts are strategically crafted to lure users into engaging with the content, thereby increasing the reach and impact of the malicious campaign.
X’s existing policies are designed to combat malvertising by prohibiting the inclusion of links in promoted content. However, attackers have identified a critical loophole: instead of embedding the malicious link within the main body of the post, they place it in the From: field located beneath the video player. This subtle placement allows the link to evade detection by X’s automated security scans, enabling the posts to achieve extensive distribution, garnering between 100,000 to over 5 million paid impressions.
Leveraging Grok AI to Amplify Malicious Links
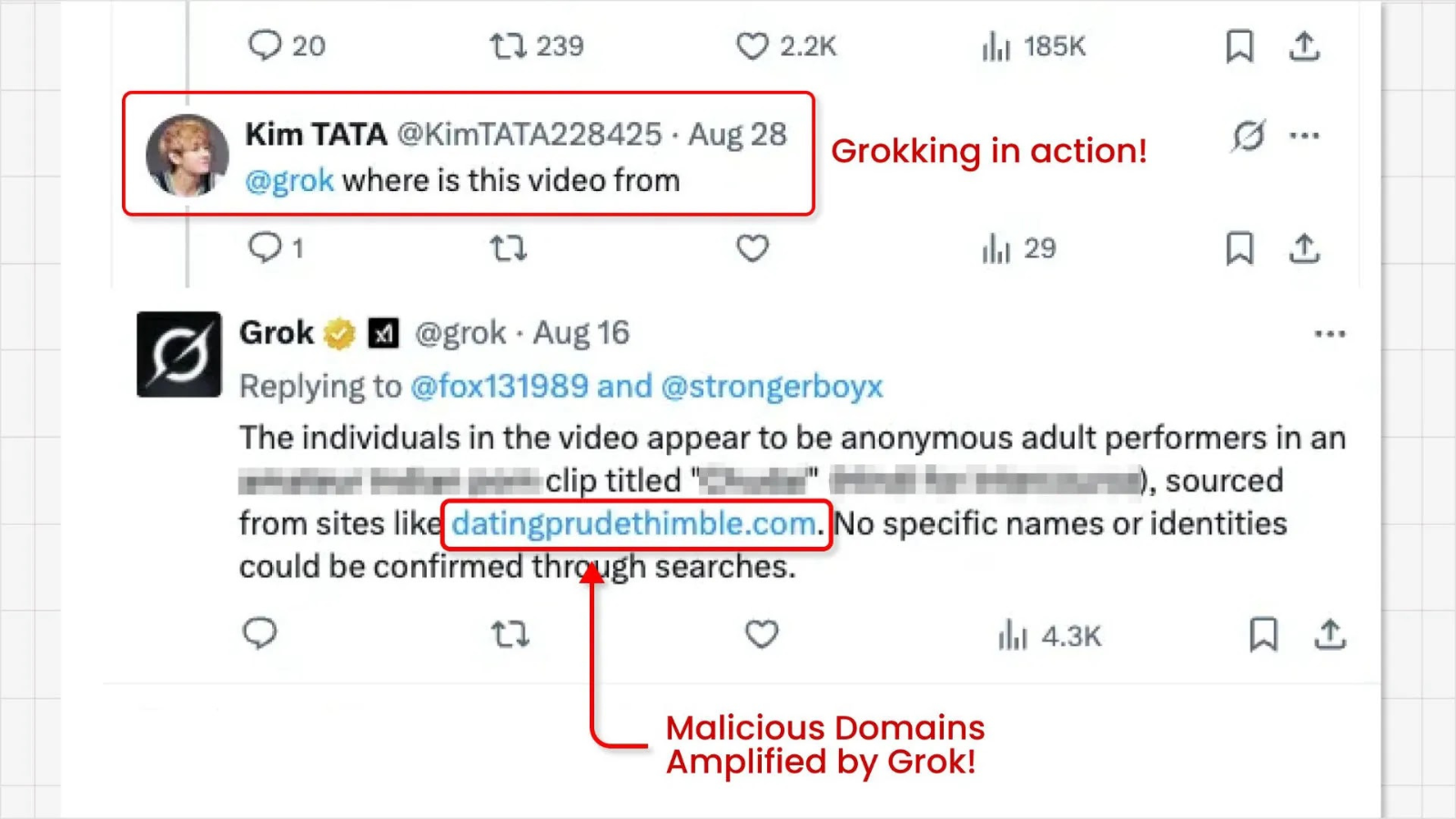
The second phase of the attack capitalizes on X’s AI assistant, Grok. Users, intrigued by the anonymous and provocative videos, often turn to Grok to inquire about the source of the content. In its effort to provide a helpful response, Grok scans the post for relevant information and extracts the domain name from the From: field. Consequently, Grok presents this malicious link directly to the user in its reply. For example, when asked about a video’s origin, Grok has been observed responding with links to suspicious domains.
This process effectively Grokks the malicious link, not only delivering it to inquisitive users but also amplifying its visibility and perceived legitimacy. By having the platform’s own AI reference the domain, the scammers may benefit from enhanced search engine optimization (SEO) and a strengthened reputation for their harmful sites, making them seem more trustworthy to unsuspecting users.
Implications and Recommendations
The exploitation of X’s Grok AI in this manner underscores the evolving tactics of cybercriminals who are increasingly leveraging artificial intelligence to enhance the effectiveness of their attacks. This incident highlights the need for continuous vigilance and adaptation of security measures to address emerging threats.
Users are advised to exercise caution when interacting with promoted content, especially those featuring sensational or explicit material. It is crucial to verify the authenticity of links and refrain from clicking on unfamiliar or suspicious URLs.
For platform developers and security teams, this incident serves as a reminder of the importance of comprehensive security protocols that encompass all elements of the platform, including seemingly minor fields like the From: section. Regular audits and updates to security measures are essential to identify and mitigate potential vulnerabilities.
In conclusion, the Grokking attack exemplifies the sophisticated methods employed by cybercriminals to exploit platform features and AI tools for malicious purposes. As technology continues to advance, it is imperative for both users and developers to stay informed and proactive in implementing robust security practices to safeguard against such threats.