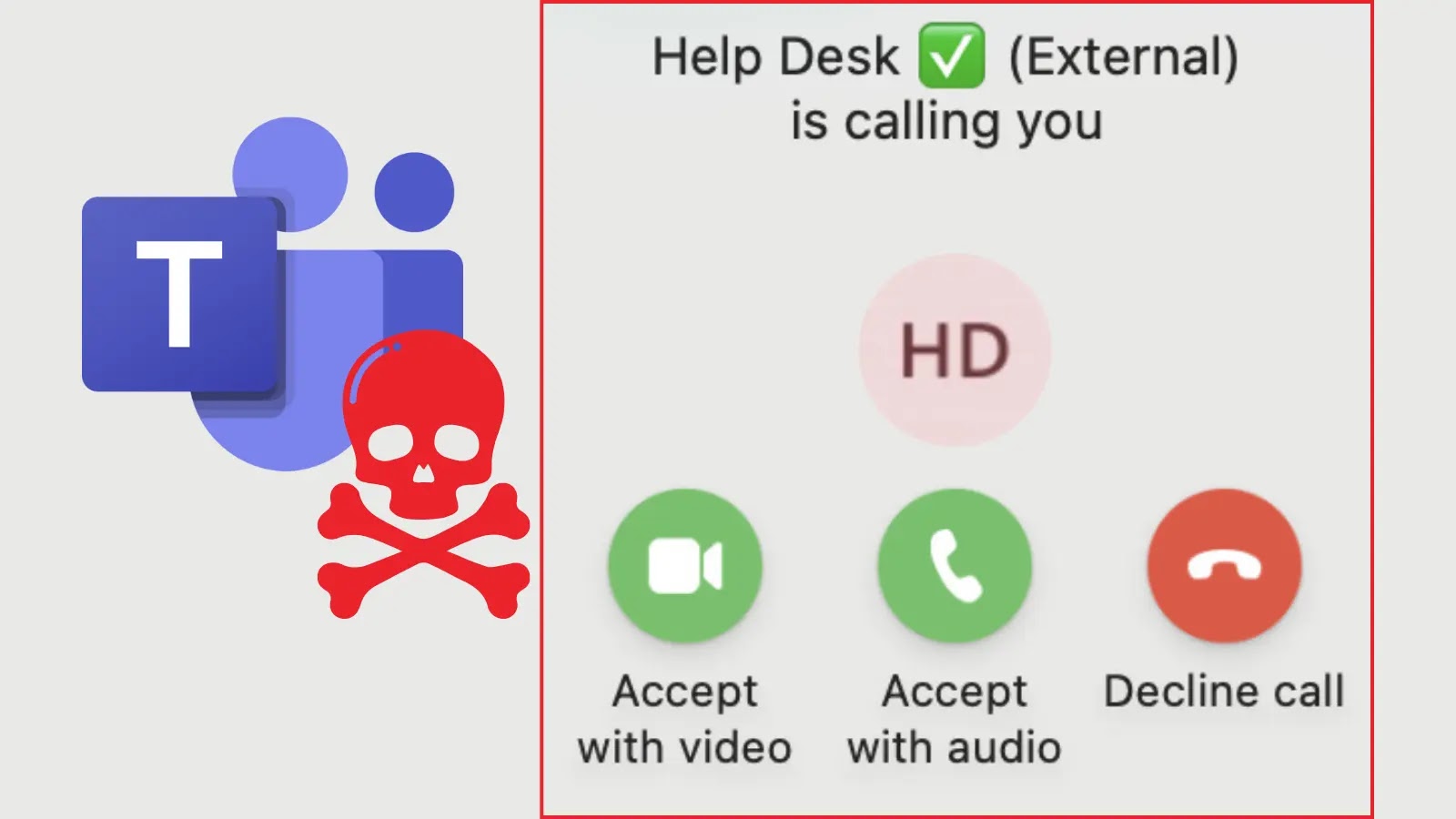
In a recent wave of cyberattacks, malicious actors have been exploiting Microsoft Teams to impersonate IT support personnel, thereby gaining unauthorized access to sensitive systems. This sophisticated phishing campaign leverages Teams’ external communication features, which are enabled by default in Microsoft 365 tenants, allowing attackers to bypass traditional email security measures.
Exploitation of Default Teams Settings
Microsoft Teams is widely used for internal and external collaboration, with default settings that permit external users to initiate contact without prior authentication. Cybercriminals exploit this feature by creating malicious Entra ID tenants with .onmicrosoft.com domains—Microsoft’s default fallback domains for business accounts lacking custom configurations. This tactic enables attackers to appear as legitimate entities within the Teams environment.
Voice Call Phishing and Remote Control
The primary attack vector involves voice call phishing, or vishing. Attackers conduct reconnaissance using Teams’ user search functionality to verify target email addresses and confirm message delivery capabilities. They then initiate voice calls to potential victims, impersonating IT support staff. Notably, voice calls from external Teams users do not trigger security warnings, unlike text-based communications. Once trust is established, attackers request screen-sharing permissions, allowing them to observe user activities and potentially guide them through malicious actions.
In some cases, attackers exploit remote control capabilities within Teams. Although Microsoft has disabled the Give Control and Request Control options by default for external participants, organizations that have modified these settings are at significant risk. Attackers can gain full remote access to victim workstations through Teams’ integrated remote control features, eliminating the need for traditional Remote Monitoring and Management (RMM) tools like QuickAssist or AnyDesk.
Detection and Mitigation Strategies
Security teams can detect these attacks by monitoring specific Microsoft 365 audit log entries. Key indicators include ChatCreated events that establish new one-on-one chats between attackers and victims, containing metadata such as Chat Thread IDs, sender display names, email addresses, and Organization IDs for both parties. MessageSent logs provide additional information, including sender IP addresses and embedded URLs.
To mitigate these threats, organizations should implement comprehensive monitoring of Teams audit logs, conduct user education programs focused on IT helpdesk impersonation tactics, and enforce restrictive external communication policies. Regularly reviewing and adjusting Teams’ external collaboration settings can also reduce the attack surface.
Broader Implications and Related Threats
This campaign is part of a broader trend where cybercriminals exploit trusted communication platforms to execute sophisticated attacks. For instance, attackers have been known to use Microsoft Teams messages to deliver malicious payloads, establishing persistence and remote access to corporate networks. These attacks often involve social engineering tactics, such as impersonating IT support personnel, to trick employees into granting remote access or executing malicious commands.
In another related attack vector, cybercriminals have combined browser cache exploitation with DLL proxying to deliver malware through Microsoft Teams and OneDrive. This technique, known as Browser Cache Smuggling, allows attackers to bypass traditional security defenses by leveraging browsers’ caching mechanisms to deliver malware disguised as benign files.
Furthermore, threat actors have been abusing Microsoft Teams meeting invites to execute device code phishing attacks. By manipulating the OAuth 2.0 Device Authorization Grant flow, attackers can steal authentication tokens, granting them persistent access to victims’ accounts without requiring passwords or multi-factor authentication.
Conclusion
The exploitation of Microsoft Teams by cybercriminals underscores the need for organizations to remain vigilant and proactive in their cybersecurity measures. By understanding the tactics employed by attackers and implementing robust detection and mitigation strategies, organizations can better protect themselves against these evolving threats.