Amazon has recently identified and disrupted a sophisticated cyber espionage campaign orchestrated by the Russian state-sponsored group APT29, also known as BlueBravo, Cloaked Ursa, Cozy Bear, and Midnight Blizzard. This operation involved compromising legitimate websites to redirect unsuspecting visitors to malicious domains, aiming to exploit Microsoft’s device code authentication process.
Understanding the Attack Mechanism
The attackers infiltrated various authentic websites, embedding malicious JavaScript code that redirected approximately 10% of site visitors to domains under their control. These domains, such as findcloudflare[.]com, were meticulously crafted to resemble legitimate Cloudflare verification pages, thereby deceiving users into believing they were interacting with a trusted service.
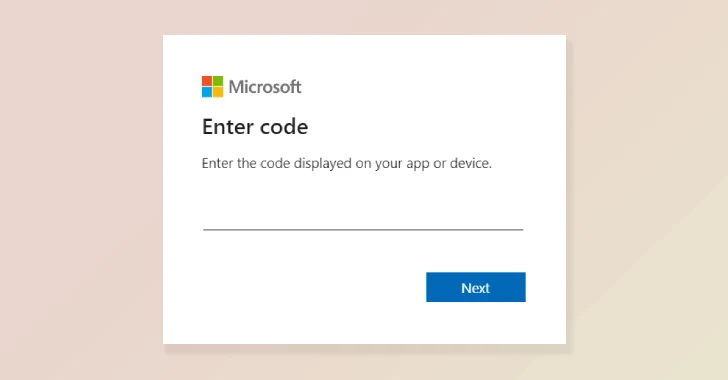
Once redirected, users were prompted to enter a device code into a Microsoft sign-in page. Unbeknownst to them, this code was generated by the attackers, and by entering it, victims inadvertently granted the threat actors access to their Microsoft accounts and associated data. This method of exploitation, known as device code phishing, has been previously documented by cybersecurity firms like Microsoft and Volexity.
APT29’s Evolving Tactics
APT29 has a history of adapting its strategies to enhance the effectiveness of its cyber espionage activities. In recent months, the group has been linked to various phishing techniques, including device code phishing and device join phishing, to gain unauthorized access to Microsoft 365 accounts. Notably, in June 2025, Google identified a campaign attributed to APT29 that exploited Google’s application-specific passwords feature to access victims’ emails.
The group’s ability to evolve and diversify its attack vectors underscores the persistent threat it poses to global cybersecurity.
Amazon’s Countermeasures
Upon detecting the malicious activity, Amazon’s threat intelligence team took immediate action to disrupt the campaign. The team identified the compromised websites and the malicious infrastructure used by APT29, implementing measures to neutralize the threat. Despite the attackers’ attempts to migrate their operations to new infrastructure, including moving off Amazon Web Services (AWS) to other cloud providers, Amazon continued to monitor and counteract their activities.
CJ Moses, Amazon’s Chief Information Security Officer, highlighted the significance of this intervention, stating, This opportunistic approach illustrates APT29’s continued evolution in scaling their operations to cast a wider net in their intelligence collection efforts.
Technical Evasion Techniques Employed by APT29
To enhance the stealth and effectiveness of their campaign, APT29 employed several sophisticated evasion techniques:
– Base64 Encoding: The malicious code was encoded in Base64 to obfuscate its true nature, making it more challenging for security tools to detect.
– Cookie Manipulation: Cookies were set to prevent the same visitor from being redirected multiple times, reducing the likelihood of detection through repeated suspicious activity.
– Infrastructure Shifting: Upon detection and blocking of their domains, the attackers swiftly moved to new infrastructure, registering domains like cloudflare.redirectpartners[.]com to continue their operations.
Broader Implications and Recommendations
This incident underscores the evolving nature of cyber threats and the importance of vigilance in the digital landscape. Organizations are advised to implement robust security measures, including:
– Regular Security Audits: Conduct thorough assessments of web assets to identify and remediate vulnerabilities that could be exploited by attackers.
– User Education: Train employees and users to recognize phishing attempts and suspicious prompts, especially those requesting authentication codes or credentials.
– Multi-Factor Authentication (MFA): Enforce the use of MFA to add an additional layer of security, making it more difficult for attackers to gain unauthorized access.
– Monitoring and Incident Response: Establish continuous monitoring systems to detect unusual activities promptly and have a well-defined incident response plan to address potential breaches.
By adopting these proactive measures, organizations can enhance their resilience against sophisticated cyber threats like those posed by APT29.