WhatsApp Introduces ‘Strict Account Settings’ to Fortify User Security In a significant move to bolster user security, WhatsApp has unveiled a new feature called ‘Strict […]
Day: January 29, 2026
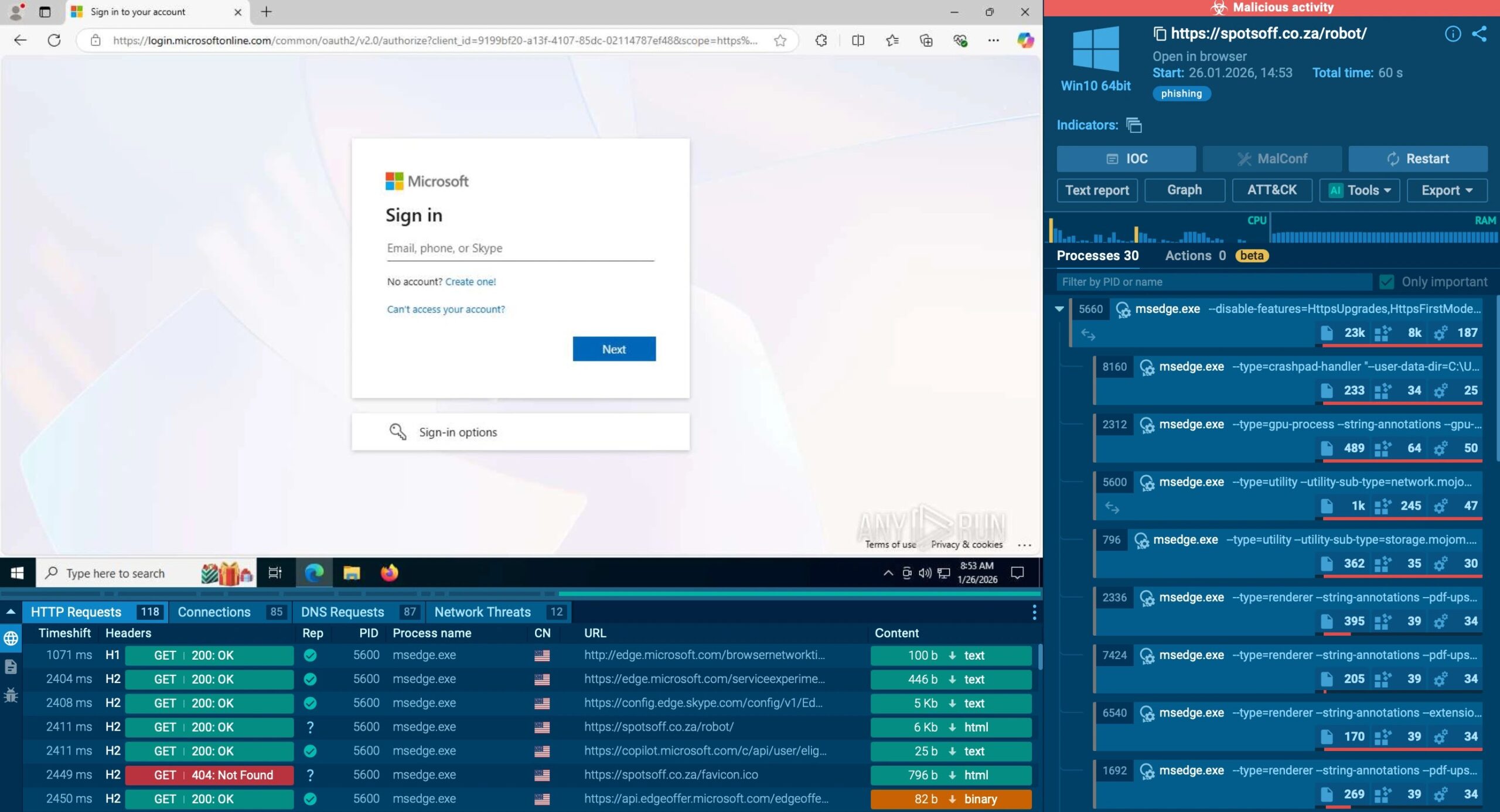
Cybercriminals Use Fake CAPTCHA, Microsoft App-V to Deploy Amatera Stealer Maliciously
Cybercriminals Exploit Fake CAPTCHA and Microsoft App-V to Deploy Amatera Stealer In a newly uncovered cyberattack campaign, threat actors are employing a sophisticated blend of […]
Chinese National Sentenced to 46 Months for $36.9M Crypto Fraud Targeting US Investors
Chinese National Sentenced to 46 Months for Laundering Millions Stolen from American Investors In a significant crackdown on international financial crime, Chinese national Jingliang Su […]
WhatsApp Denies Lawsuit Claims, Reaffirms Commitment to Encrypted Message Privacy
Article Title: WhatsApp Refutes Lawsuit Allegations, Affirms Message Privacy Through End-to-End Encryption WhatsApp, the globally renowned messaging platform, has recently come under legal scrutiny with […]
Memory Leak in ZAP’s JavaScript Engine Impacts Active Scanning, Urgent Fix Issued
Critical Memory Leak in ZAP’s JavaScript Engine Disrupts Active Scanning The Zed Attack Proxy (ZAP), a widely utilized open-source web application security scanner, has recently […]
Critical Vulnerability Found in TP-Link Archer MR600 v5 Routers; Urgent Firmware Update Advised
Critical Vulnerability in TP-Link Archer MR600 v5 Routers: Immediate Action Required A significant security flaw has been identified in TP-Link’s Archer MR600 v5 routers, potentially […]
Semantic Chaining Reveals Security Flaws in Grok 4 and Gemini Nano AI Models
Semantic Chaining: The New AI Jailbreak Technique Undermining Grok 4 and Gemini Nano Security In the rapidly evolving landscape of artificial intelligence, ensuring the safety […]
Zero-Day in Gemini MCP Tool Poses Severe Remote Code Execution Threat; No Patch Available
Critical Zero-Day Vulnerability in Gemini MCP Tool Exposes Systems to Remote Code Execution A severe zero-day vulnerability has been identified in the Gemini MCP Tool, […]
Cybercriminals Hijack Enterprise Emails to Deploy Sophisticated Phishing Links Targeting Middle East Firms
Cybercriminals Exploit Genuine Enterprise Email Threads to Deploy Phishing Links In a sophisticated supply chain phishing attack, cybercriminals infiltrated an active email conversation among C-suite […]
CISA Chief’s Use of ChatGPT for Sensitive Data Sparks Security Review
Article Title: CISA Chief’s ChatGPT Use Raises Security Concerns In August 2025, Madhu Gottumukkala, the acting director of the Cybersecurity and Infrastructure Security Agency (CISA), […]