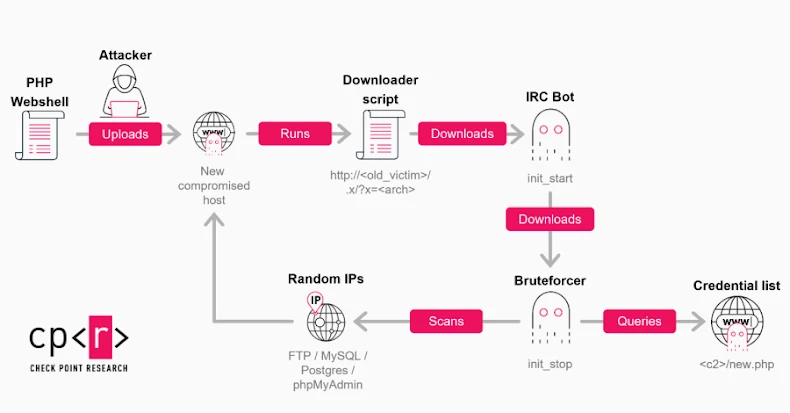
Cybersecurity in 2025: How Attackers Leveraged AI to Exploit Traditional Vulnerabilities In 2025, the cybersecurity landscape witnessed a significant evolution in attack methodologies, primarily driven […]
Day: January 13, 2026
AI Vulnerability Ni8mare and Kimwolf Botnet Threaten Cybersecurity; China-Linked Espionage Targets Telecom Firms
AI Automation Exploits and Telecom Espionage: A Deep Dive into Recent Cybersecurity Threats In the rapidly evolving digital landscape, recent cybersecurity incidents have underscored the […]
ServiceNow Patches Critical AI Platform Flaw Allowing User Impersonation; Urges Immediate Updates
ServiceNow Addresses Critical AI Platform Vulnerability Allowing Unauthenticated User Impersonation ServiceNow has recently addressed a significant security vulnerability within its AI Platform, identified as CVE-2025-12420, […]
Service Providers Enable Industrial-Scale Pig Butchering Scams with Comprehensive Tools and Infrastructure
Unveiling the Backbone of Industrial-Scale Pig Butchering Scams: Service Providers’ Role Cybersecurity experts have recently exposed the critical role of certain service providers in enabling […]
SHADOW#REACTOR Campaign Unveiled: Multi-Stage Malware Uses Remcos RAT, Bypasses Detection with Advanced Evasion Techniques
SHADOW#REACTOR: Unveiling the Multi-Stage Malware Campaign Deploying Remcos RAT Cybersecurity experts have recently uncovered a sophisticated malware campaign, dubbed SHADOW#REACTOR, which employs a complex, multi-stage […]
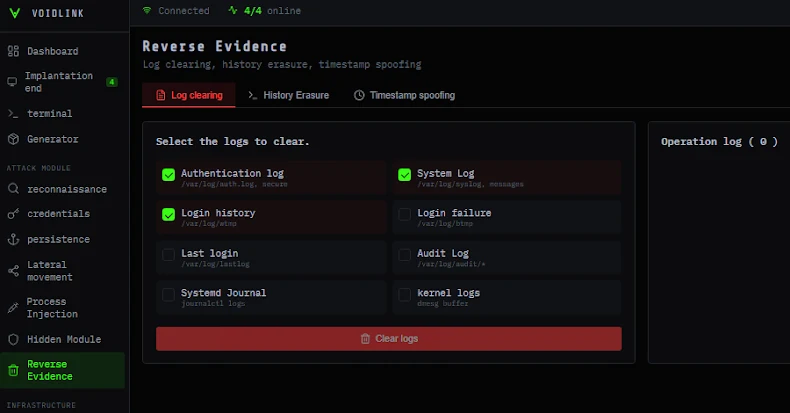
Emerging Threat: VoidLink Malware Targets Linux-Based Cloud Infrastructures with Advanced Capabilities
In the ever-evolving landscape of cybersecurity threats, a new and sophisticated malware framework named VoidLink has emerged, specifically targeting Linux-based cloud environments. Discovered in December […]
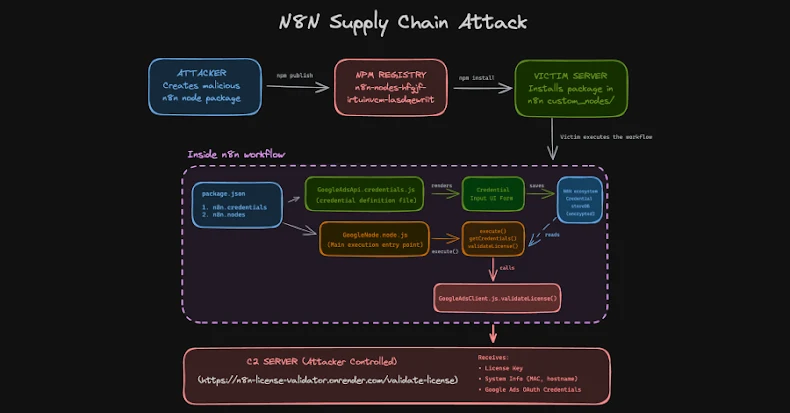
Supply Chain Attack Targets n8n Platform, Steals OAuth Tokens Through Malicious npm Packages
n8n Supply Chain Attack Exploits Community Nodes to Steal OAuth Tokens In a recent and sophisticated supply chain attack, malicious actors have infiltrated the npm […]
GoBruteforcer Botnet Targets Cryptocurrency Databases via Weak Credentials on Linux Servers
GoBruteforcer Botnet Exploits Weak Credentials to Target Cryptocurrency Databases A recent surge in cyberattacks has been attributed to GoBruteforcer, a sophisticated botnet that infiltrates databases […]
CISA Warns of Active Exploitation of Gogs Vulnerability Allowing Code Execution
CISA Alerts on Active Exploitation of Gogs Vulnerability Leading to Code Execution The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently issued a warning […]
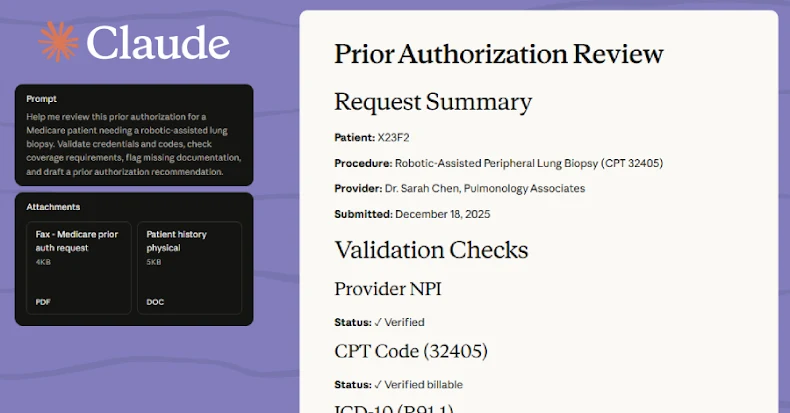
Anthropic Launches Claude AI for Healthcare, Enhancing Personalized Health Management with Secure Data Integration
Anthropic Unveils Claude AI for Healthcare: A New Era in Personalized Health Management In a significant advancement for digital health, Anthropic has introduced Claude for […]