Iranian Cyber Espionage Targets Aerospace and Defense Sectors with Advanced Malware In a series of sophisticated cyber espionage campaigns, Iranian state-sponsored threat actors have been […]
Year: 2025
Tuoni C2 Framework Used in Advanced Cyber Attack on U.S. Real Estate Firm
Emerging Tuoni C2 Framework Exploited in Sophisticated Real Estate Cyber Attack In mid-October 2025, a significant cyber attack targeted a prominent U.S.-based real estate company, […]
Meta Boosts WhatsApp Security with Research Proxy Tool and $4M Bug Bounties
Meta Enhances WhatsApp Security with New Research Tools and $4 Million in Bug Bounties In a significant move to bolster the security of its widely-used […]
Sneaky 2FA’ Phishing Kit Mimics Legitimate Prompts with Advanced Browser Tactics
Advanced Phishing Kit ‘Sneaky 2FA’ Employs Browser-in-the-Browser Tactics to Mimic Legitimate Login Prompts Cybersecurity researchers have identified a significant advancement in phishing techniques with the […]
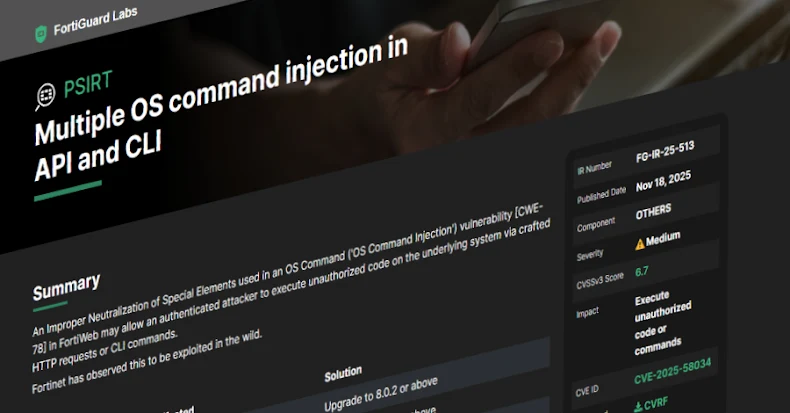
Fortinet Discloses CVE-2025-58034 Flaw in FortiWeb Exploited, Urges Immediate Patching
Fortinet has recently disclosed a medium-severity vulnerability in its FortiWeb web application firewall (WAF), identified as CVE-2025-58034, which has been actively exploited in the wild. […]
Xanthorox AI Tool Empowers Cybercriminals with Malicious Code Generation, Posing New Cybersecurity Threat
Xanthorox: The AI Tool Empowering Cybercriminals with Malicious Code Generation In the ever-evolving landscape of cybersecurity threats, a new and formidable adversary has emerged: Xanthorox. […]
Microsoft Azure Mitigates Record 15 Tbps DDoS Attack by Aisuru Botnet Targeting IoT Devices
Unprecedented 15 Tbps DDoS Attack Targets Microsoft Azure Network On October 24, 2025, Microsoft Azure successfully mitigated one of the most significant distributed denial-of-service (DDoS) […]
Google Issues Urgent Chrome Security Update to Fix Critical Zero-Day Exploited in the Wild
Critical Chrome Zero-Day Vulnerability Exploited in the Wild – Immediate Update Required Google has urgently released a security update for its Chrome browser to address […]
Critical IBM AIX Vulnerabilities Allow Remote Command Execution; Urgent Patch Recommended
Critical IBM AIX Vulnerabilities Expose Systems to Remote Command Execution IBM has recently addressed two critical security vulnerabilities in its AIX operating system that could […]
Cybercriminals Use RDP Flaws to Deploy Lynx Ransomware and Destroy Backups
Cybercriminals Exploit RDP Vulnerabilities to Deploy Lynx Ransomware and Sabotage Backups In recent cybersecurity incidents, attackers have been leveraging compromised Remote Desktop Protocol (RDP) credentials […]