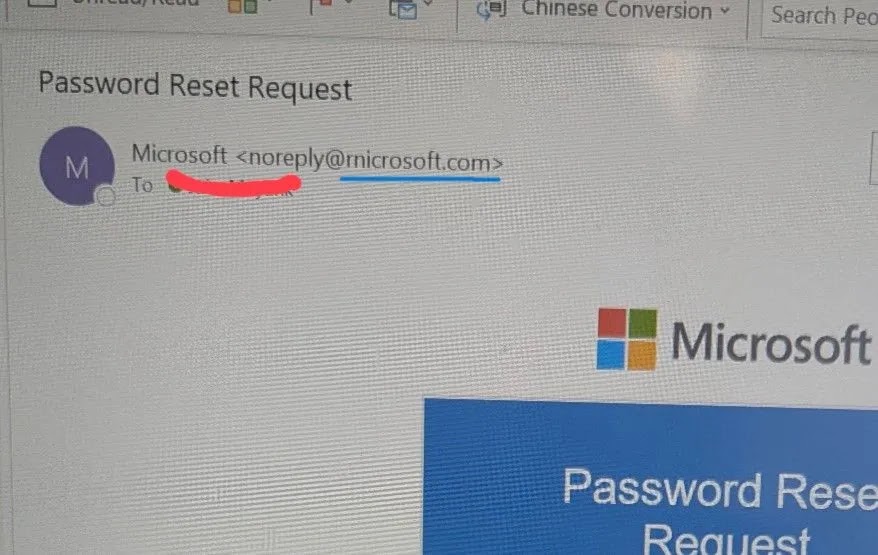
Cybercriminals Exploit Typographical Deception to Mimic Microsoft Domains and Steal Credentials In a sophisticated phishing campaign, cybercriminals are employing a subtle typographical trick to deceive […]
Year: 2025
Python-Based Malware Evades Detection by Integrating Into Legitimate Windows Processes, Researchers Warn
Cybercriminals Exploit Python-Based Malware to Conceal Attacks Within Legitimate Windows Processes In a significant advancement of cyberattack methodologies, security researchers have identified a sophisticated Python-based […]
Zapier and ENS NPM Accounts Breached in Massive Supply Chain Attack by Shai Hulud Malware
Massive Supply Chain Attack: Zapier’s NPM Account Compromised by Shai Hulud Malware In a significant escalation of software supply chain attacks, the NPM accounts of […]
ToddyCat APT Exploits OAuth 2.0 to Hijack Corporate Emails, Elevating Cyber Threats
ToddyCat APT’s Advanced Tactics: Infiltrating Corporate Email Communications In the ever-evolving landscape of cyber threats, the Advanced Persistent Threat (APT) group known as ToddyCat has […]
Cybercriminals Exploit Blockchain with EtherHiding Malware Technique
EtherHiding: The New Frontier in Malware Delivery via Blockchain In the ever-evolving landscape of cyber threats, a novel technique named EtherHiding has emerged, leveraging blockchain […]
Malicious PyPI Package Targets Cryptocurrency Users with Sophisticated Malware Techniques
Malicious PyPI Package Targets Cryptocurrency Users with Sophisticated Malware A recent cybersecurity incident has unveiled a malicious campaign targeting cryptocurrency users through a deceptive Python […]
AI-Driven Malware Emerges: GPT-3.5-Turbo and GPT-4 Used by Cybercriminals to Bypass Security Defenses
Emerging Threats: How GPT-3.5-Turbo and GPT-4 Are Enabling Autonomous Malware Development The advent of advanced large language models (LLMs) such as GPT-3.5-Turbo and GPT-4 has […]
Critical Vulnerabilities in Tenda Routers Risk Remote Code Execution; No Patches Available
Critical Vulnerabilities in Tenda N300 Routers Expose Users to Remote Code Execution Recent security analyses have uncovered severe vulnerabilities in Tenda N300 wireless routers and […]
Leaked Docs Expose APT35: Insights Into Iranian Cyber Espionage Tactics and Global Targeting
Unveiling APT35: Leaked Documents Reveal Iranian Cyber Espionage Tactics In October 2025, a significant data breach exposed the internal operations of APT35, also known as […]
India-Linked Dropping Elephant Targets Pakistan Defense with Complex Cyber-Espionage Attack
Dropping Elephant’s Sophisticated Cyber Assault on Pakistan’s Defense Sector In a recent escalation of cyber-espionage activities, the India-aligned threat group known as Dropping Elephant has […]