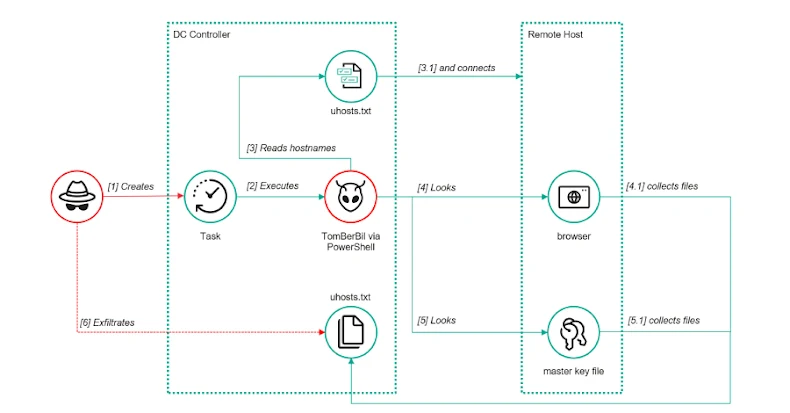
ToddyCat’s Advanced Tactics: Unveiling New Tools for Email and Credential Theft The cyber threat group known as ToddyCat has recently enhanced its arsenal with sophisticated […]
Year: 2025
Cybercriminals Use Fake Windows Updates on Adult Sites to Deploy JackFix Malware
JackFix: Cybercriminals Exploit Fake Windows Updates on Adult Sites to Deploy Stealer Malware Cybersecurity experts have recently uncovered a sophisticated campaign, dubbed JackFix, that employs […]
Sensitive Data Exposed by JSONFormatter and CodeBeautify: Years of Passwords, API Keys Leaked
In a recent investigation, cybersecurity firm watchTowr Labs uncovered a significant data exposure involving the popular online code formatting tools JSONFormatter and CodeBeautify. These platforms, […]
FBI Warns of $262M in Account Takeover Fraud Amid AI-Driven Phishing Surge
FBI Reports $262 Million in Account Takeover Fraud Amid Surge in AI-Driven Phishing and Holiday Scams The Federal Bureau of Investigation (FBI) has issued a […]
Hackers Exploit WhatsApp to Spread Stealthy Malware, Target Brazilian Users
Hackers Exploit WhatsApp to Deploy Stealthy Malware Harvesting Logs and Contacts A sophisticated malware campaign has recently emerged, targeting Brazilian users by exploiting WhatsApp as […]
Critical Flaws in NVIDIA Isaac-GR00T Expose Systems to Code Injection; Urgent Patch Released
Critical Vulnerabilities in NVIDIA’s Isaac-GR00T Robotics Platform Expose Systems to Code Injection Attacks NVIDIA has recently identified and disclosed two critical vulnerabilities within its Isaac-GR00T […]
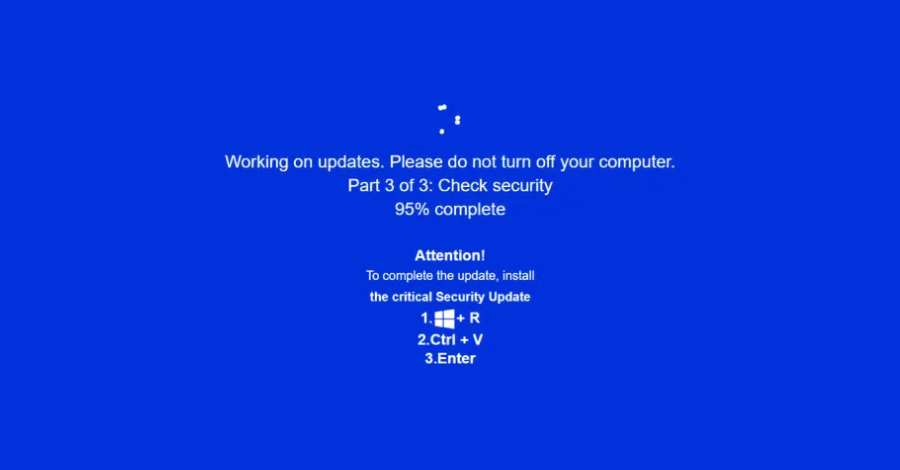
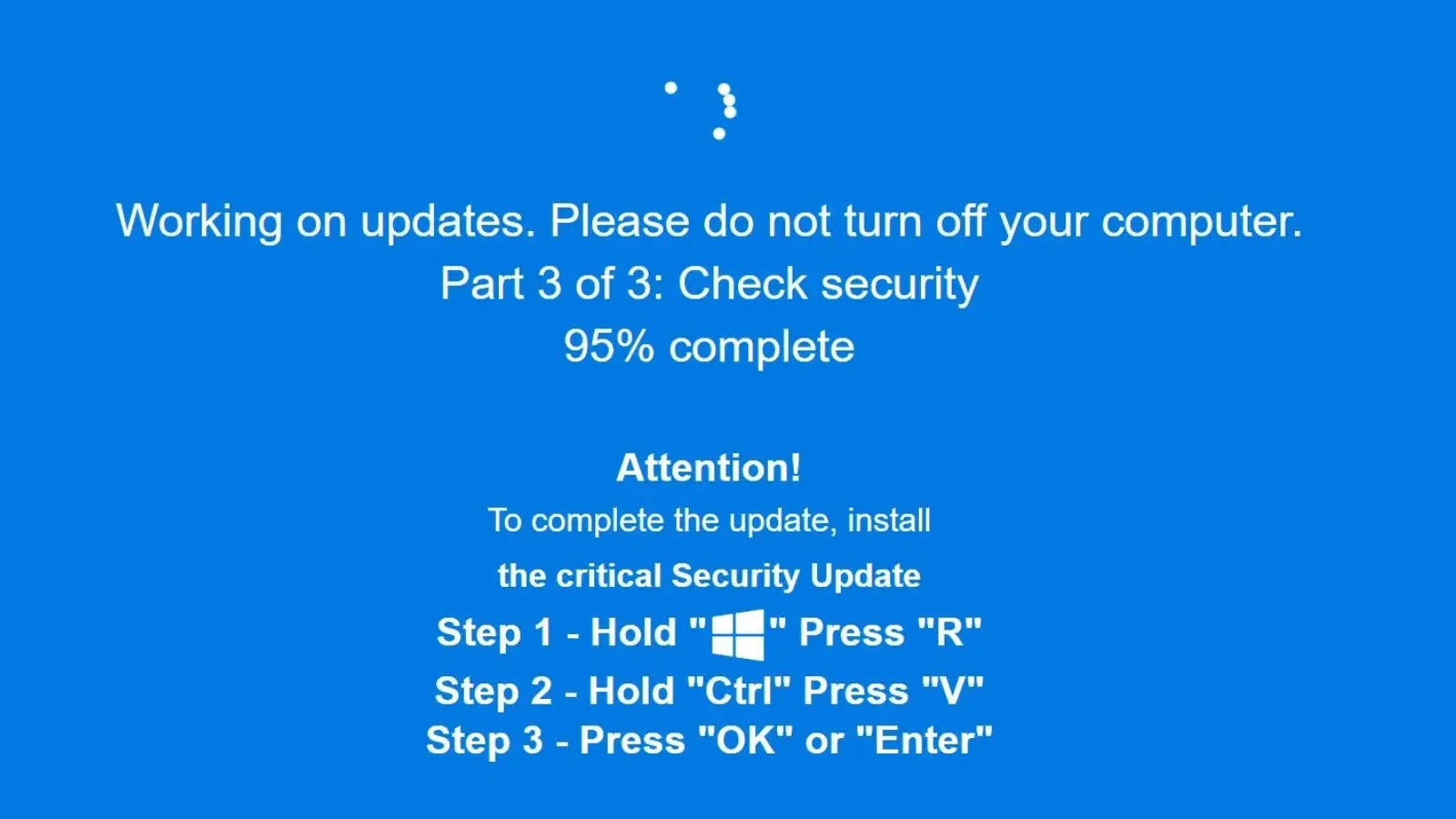
Cybercriminals Use Fake Windows Update Screens, Steganography to Spread LummaC2 and Rhadamanthys Malware
Cybercriminals Exploit Fake Windows Update Screens to Deploy Stealthy Malware A sophisticated cyberattack campaign has emerged, leveraging counterfeit Windows Update screens and advanced steganography techniques […]
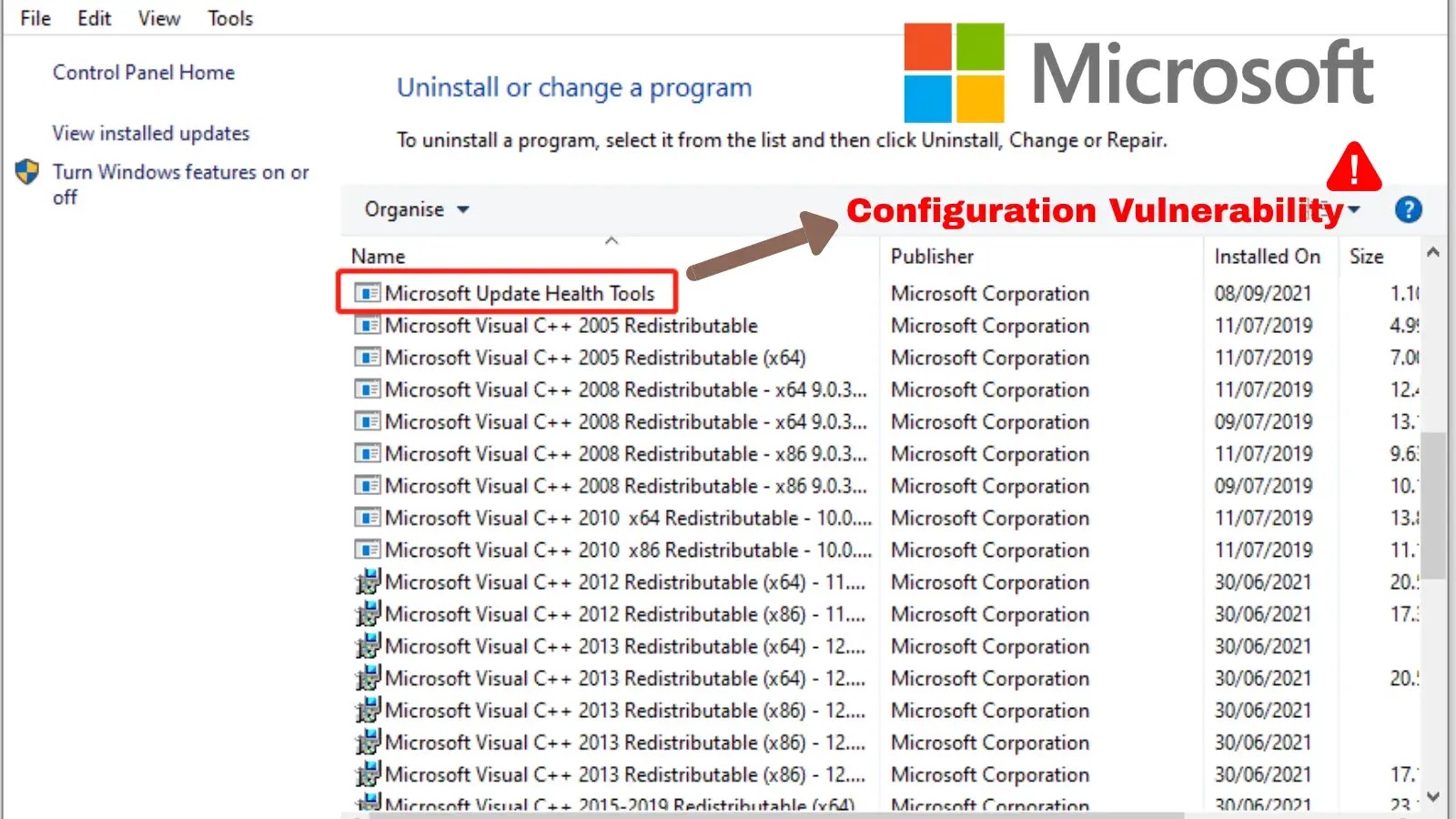
Critical Vulnerability in Microsoft’s Update Health Tools Allows Remote Code Execution
Critical Vulnerability in Microsoft’s Update Health Tools Exposes Systems to Remote Code Execution A significant security flaw has been identified in Microsoft’s Update Health Tools […]
Top EM Tools for Cybersecurity in 2026: Mandiant, Wiz, RiskProfiler Lead the Pack
Top 10 Exposure Management Tools to Fortify Your Cybersecurity in 2026 In the rapidly evolving digital landscape, organizations face an ever-expanding array of cyber threats. […]
Canon Hit by Clop Ransomware Using Oracle EBS Zero-Day; Breach Isolated to U.S. Subsidiary
Article Title: Canon Targeted in Clop Ransomware Attack Exploiting Oracle E-Business Suite Zero-Day Canon Inc., a global leader in imaging and optical products, has confirmed […]