TikTok Shop Introduces Digital Gift Cards to Rival Amazon and eBay TikTok Shop has unveiled a new feature that enables users to purchase digital gift […]
Year: 2025
ChatGPT’s Impact Surges: 300M Weekly Users, New Features, and Safety Upgrades Propel AI Chatbot Forward
ChatGPT: A Comprehensive Guide to OpenAI’s Revolutionary AI Chatbot Since its debut in November 2022, OpenAI’s ChatGPT has rapidly transformed from a novel AI experiment […]
Tech Layoffs Surge in 2025: Over 22,000 Jobs Cut Amidst AI and Automation Impact
Tech Industry Faces Unprecedented Layoffs in 2025: A Comprehensive Overview The technology sector has experienced a significant wave of layoffs throughout 2025, marking a continuation […]
Uber and Lyft to Test Baidu-Backed Robotaxis in London by 2026
Uber and Lyft to Launch Baidu-Powered Robotaxi Trials in London by 2026 In a significant advancement for autonomous transportation, ride-hailing giants Uber and Lyft have […]
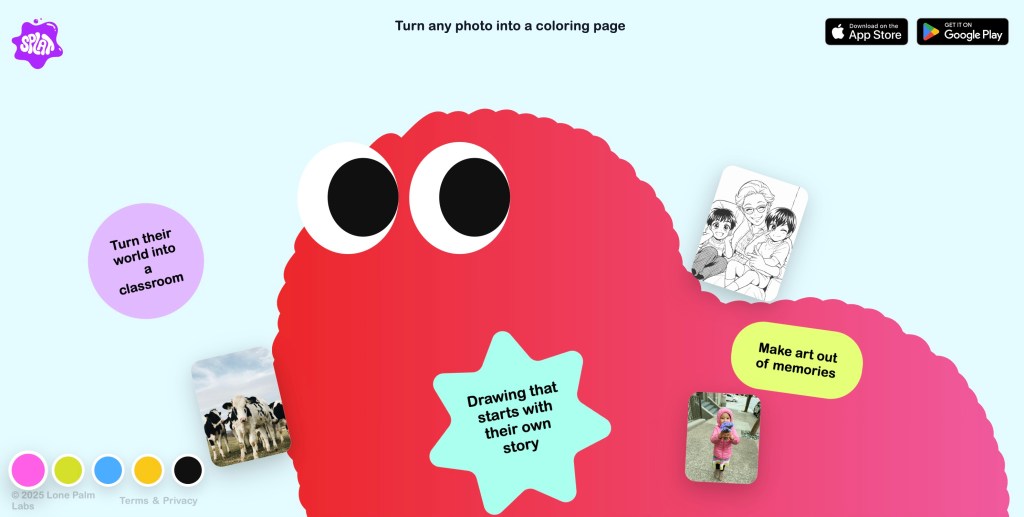
Splat App Transforms Personal Photos into Kids’ Coloring Pages with AI Technology
Transform Your Photos into Kids’ Coloring Pages with Splat’s AI-Powered App In an era where technology continually reshapes our daily experiences, the team behind the […]
Tory Bruno Resigns as CEO of United Launch Alliance; John Elbon Named Interim Leader
Tory Bruno Steps Down as CEO of United Launch Alliance After 12 Years Tory Bruno, who has led United Launch Alliance (ULA) as President and […]
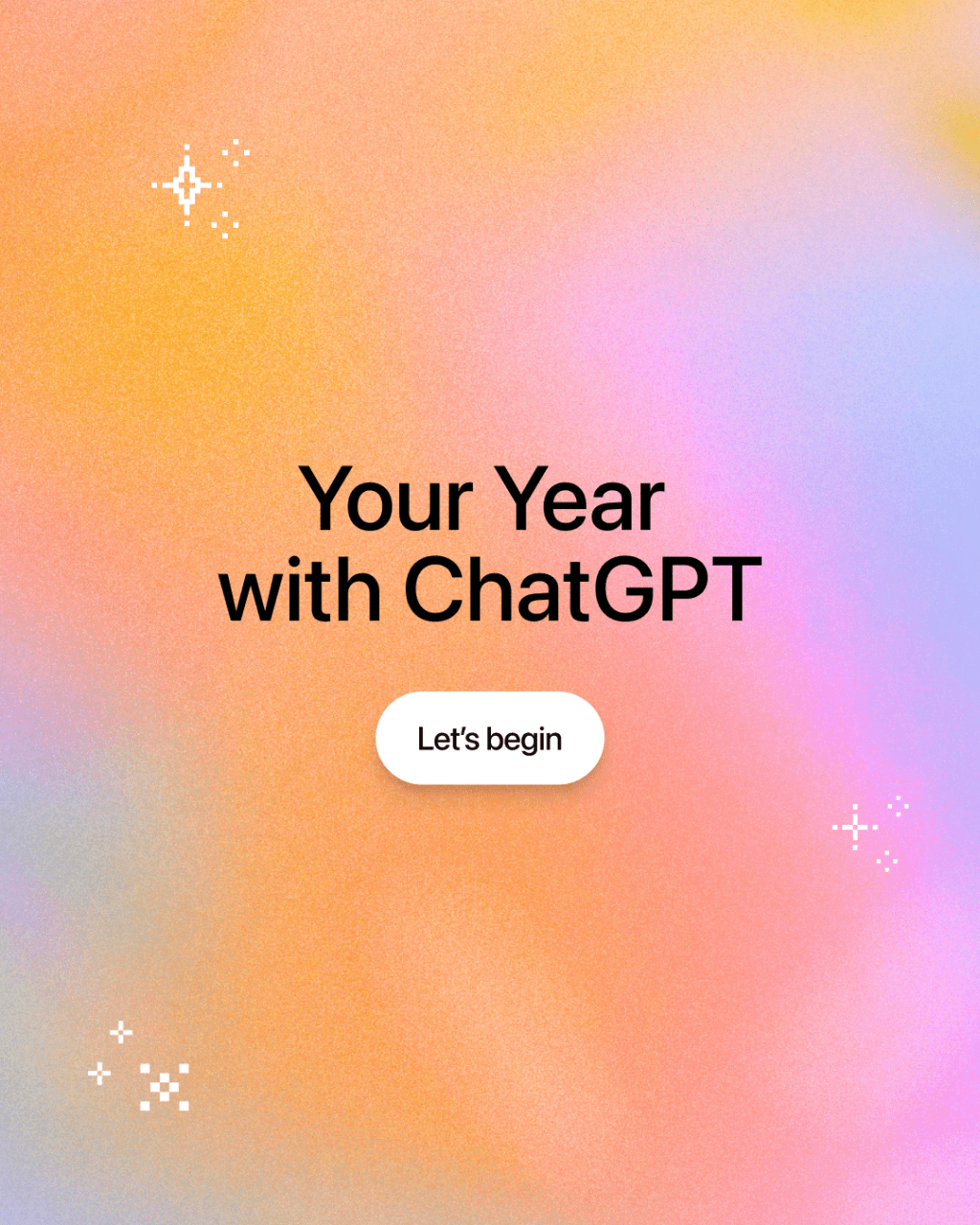
OpenAI Launches Your Year with ChatGPT for Personalized AI Interaction Review
ChatGPT Unveils ‘Your Year with ChatGPT’: A Personalized Annual Review Experience In a move reminiscent of Spotify’s popular Wrapped feature, OpenAI has introduced Your Year […]
Paramount Intensifies Warner Bros. Acquisition Bid with Larry Ellison’s $40B Backing
Article Title: Paramount’s Renewed Pursuit of Warner Bros. with Larry Ellison’s $40 Billion Commitment In a bold move to reshape the entertainment industry, Paramount Skydance […]
Alphabet Acquires Intersect Power for $4.75B to Boost AI Expansion with Sustainable Energy Solutions
Alphabet’s $4.75 Billion Acquisition of Intersect Power: A Strategic Move to Energize AI Expansion In a significant strategic maneuver, Alphabet Inc., the parent company of […]
Trump Administration Halts Offshore Wind Projects Citing National Security Concerns
Trump Administration Suspends Offshore Wind Leases Citing Radar Interference Concerns In a move that has reignited debates over the future of renewable energy in the […]